
Seagate launches Game Drive PS5 NVMe SSD
Today, Seagate launches its new, officially licensed storage drive for PlayStation gamers, the Game Drive PS5 NVMe SSD. This drive brings fast storage technology, PCIe Gen4 NVMe SSD, right to the PlayStation 5 console.
Seagate’s new drive is a speed demon, boasting read speeds of up to 7300 MB/s, which is way faster than the older PCIe Gen3 SSDs. Basically, this means your games will load lightning fast.
elementary OS 7.1 Linux distribution focuses on privacy, inclusivity, and more
Today is a very exciting day for the Linux community. You see, elementary OS 7.1 is finally here! Don’t mistake this for a boring point release either -- it is a fresh update to the operating system that comes packed with features focusing on privacy, user consent, and inclusivity.
One of the big highlights is its integration with FreeDesktop.org's Portals, which are designed to provide a safe way for apps to interact with the operating system while ensuring they only access data and features approved by the user. There's a new feature called the Background & Autostart Portal that alerts you when apps are running in the background and makes sure they ask for your permission before they can start automatically when you turn on your device.

How and why we need to break the stigma around second hand tech
Mountains of e-waste, increasingly scarce resources, and volatile supply chains; these are just three of the reasons that the technology industry should be re-considering its current model of 'take, make and replace'. We’ve seen across other industries, such as fashion, that the cost-of-living crisis and increasingly eco-conscious consumers have led to the second-hand market becoming a lucrative business.
Through holding onto stigmas around the quality and performance of second-hand tech, we continue to purchase brand new despite the negative impact this is having on our planet. So, what needs to be done to see similar change across the tech industry?

Samsung T9 Portable SSD blends luxury and ruggedness with top notch performance
Samsung today expands its T-series storage product line with the launch of the T9 Portable Solid State Drive (SSD), blending aesthetics with portability and performance. The T9 is engineered to be a reliable companion for data safety during transit, boasting swift data transfer rates and generous storage capacities. The rugged USB-C drive can survive drops up to nine feet, but if it does somehow become inoperable, it comes with a five-year warranty.
“Modern-day creators necessitate a storage ally capable of securely housing their artworks, while also saving them precious time, particularly when on-the-move,” remarked Jose Hernandez, the Senior Director of Memory Product Marketing at Samsung. “The T9 emerges as an apt choice, aiding a vast global community of creators in effortlessly capturing high-definition photographs, filming and editing 4K videos, transferring files, and executing seamless backups in a matter of seconds.”

Microsoft borrows a feature from 'Windows Utopia' to make Windows 11 setup more fun
While the world waits for Microsoft to announce Windows 12, there are a number of talented concept creators coming up with their own visions for what that future OS might look like. Some are even showing us entirely original Windows creations.
One such example of this is Windows Utopia, which concept designer AR 4789 came up with two months ago. As with his previous concepts, the video takes us through the "installation" process, and one of his ideas from this has just arrived in Windows 11.

Gen Z twice as likely to think cybersecurity isn't worth the effort
In a study that echoes the findings we reported earlier today on employee security habits, research from the National Cybersecurity Alliance (NCA) and CybSafe finds that Gen Z is twice as likely as older generations to think cybersecurity isn't worth the effort.
The poll of over 6,000 individuals across the US, UK, Canada, Germany, France and New Zealand, examined key cybersecurity behaviours, attitudes and trends ahead of October's Cybersecurity Awareness Month.

One in eight open source downloads have known and avoidable risks
This year has seen twice as many software supply chain attacks as 2019-2022 combined and one in eight open source downloads today pose known and avoidable risks.
The latest State of the Software Supply Chain Report from Sonatype, which logged 245,032 malicious packages in 2023, also shows that 96 percent of vulnerabilities are still avoidable.

Plugable releases Thunderbolt 4 and USB4 docking station (TBT4-UDX1)
Today, Plugable releases its latest product -- the Thunderbolt 4 and USB4 docking station (TBT4-UDX1). This device emphasizes the Thunderbolt 4 experience and 10-in-1 expansion, accommodating dual 4K 60Hz displays.
The TBT4-UDX1 is notable for its Thunderbolt certification, ensuring users the leverage of improved power delivery alongside a 40Gbps bi-directional bandwidth. The dock further includes two downstream Thunderbolt ports, broadening the horizon for users to connect a range of peripherals and external displays.

The future of AI in payments is already here
The strongest case for bringing artificial intelligence-powered technology into the electronic bill payment and presentment (EBPP) space stems from the reality that, in some ways, it is already here. Many of the buzziest applications like machine learning-powered customer service chatbots and AI-written content are continually developing and still a ways off from being called perfected. But there are other ways AI tools are already quietly powering some facets of the EBPP industry.
The EBPP industry is still in the earliest stages of implementing these tools. By working to understand the reality of AI in the EBPP space today, executives seeking to find the most effective uses of AI and forecast the future of the industry can both reframe their current perspectives, and calibrate their expectations and strategies for what’s to come. The areas in which AI solutions can be most helpful as they grow more advanced may not be the most headline-grabbing, but they will make a significant impact on the industry.

Younger employees more likely to have unsafe cybersecurity habits
A new report into hidden threats from Ivanti finds that one in three employees believe their actions do not impact their organization's security.
The research also shows that Millennial and Gen Z office workers are more likely to have unsafe cybersecurity habits when compared to Gen X and older (those above 40 years of age).

Are doubled specs and a bunch of promises from Google enough to make Chromebook Plus devices successful?
Did Chromebook ever live up to the hype? Were they ever successful and popular? The answer to these questions depends entirely on who you ask, but with the introduction of a completely new category of Chromebook, Google is hoping to appeal to a whole new audience.
With Chromebook Plus, Google is upping the minimum guaranteed hardware specs. This means a doubling of memory to at least 8GB, a minimum of 128GB of storage, and a better display and webcam. To earn the Chromebook Plus label, a device will also have to pack an Intel Core i3 12th Gen or above, or AMD Ryzen 3 7000 series or above. Google is also introducing new features -- and promising more in the future -- for ChromeOS, including for existing devices that already meet the requirements.

UK businesses struggle with security budgets as cyber incidents increase
UK businesses have experienced on average 30 cyber incidents over the last twelve months, marking a 25 percent increase compared to last year.
But a new report from iomart and Oxford Economics finds that 27 percent of organizations think their cyber security budget is inadequate to fully protect them from growing threats. This is despite spending more than £40,000 ($48,000) a year on cyber protection such as vulnerability assessments, penetration testing, and red team engagements.

Microsoft admits what many Windows 11 users already knew: Copilot is buggy
The current enthusiasm for everything to be injected with a dose of AI means that just about nothing is left untouched by artificial intelligence, and that includes Windows 11.
Microsoft recently started the roll out of Copilot, its AI assistant, and it has received something of a lukewarm reception. Promising much but currently delivering little, the disappointment surrounding Copilot is heightened by the presence of various bugs -- especially for anyone who is reliant on Narrator.
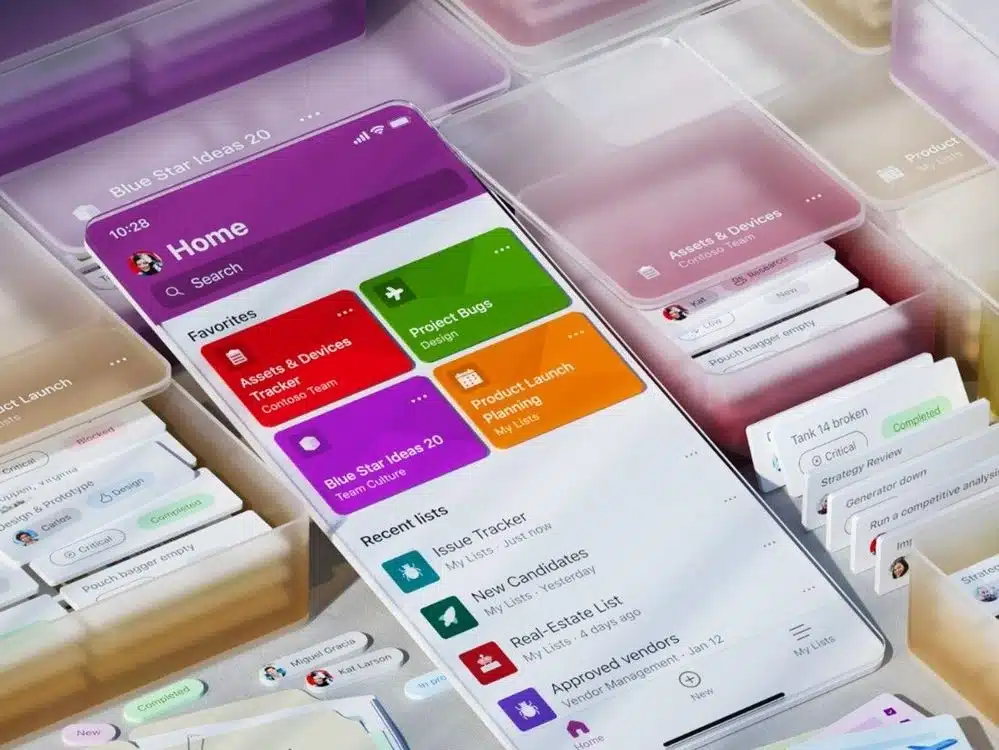
Microsoft Lists is now available to everyone as it is freed from the shackles of being a businesses-only task manager
Microsoft Lists, the company's task manager app, has been made available to anyone who is looking for a way to manage a range of projects. Now three years old, Lists was originally limited to business and enterprise users, but Microsoft has taken the decision to open it up to everyone.
The move comes after the company conducted a limited test with several thousand consumer-level users. During its time as a business/enterprise-only app, Microsoft Lists gained a reputation for ease of use, an intuitive workflow and an impressive range of templates for managing a variety of tasks on iOS, Android and the web.

MINISFORUM launches BD770i mini-ITX motherboard with integrated AMD Ryzen 7 7745HX processor
Today, MINISFORUM launches a new mini-ITX motherboard with an integrated (and non-replaceable) AMD processor that is sure to delight fans of small computers. Called “BD770i,” the board is powered by the Ryzen 7 7745HX CPU, known for its power efficiency and quiet operation. The BD770i also features two PCIe 5.0 M.2 slots for fast data access and storage.
One of the key features of the BD770i is its advanced cooling system. This system ensures that both the processor and the dual PCIe 5.0 SSDs stay cool, providing consistent performance whether you're gaming, creating content, or enjoying a home theater experience.



