
Microsoft Defender caught issuing false warnings about safe URLs
Microsoft has confirmed an issue with Defender which resulted in users being shown warnings about URLs that were entirely safe. The emails advised admins that "a potentially malicious URL click was detected", with affected users complaining that legitimate URLs, such as Zoom meeting links, were being flagged up as dangerous.
In addition to the false positives, the "View alerts" link included in the warning emails sent out to admins failed to provide any further information that could prove useful.
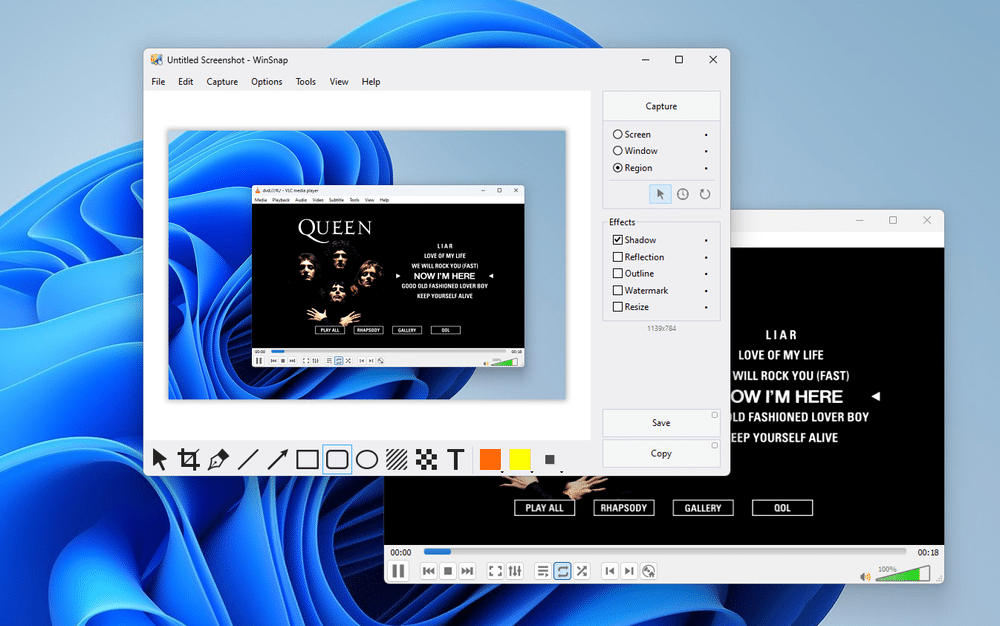
WinSnap 6.01 unveils modern facelift, major reorganization of tools
NTWind Software has unveiled a major new version of its powerful shareware screen capture tool for Windows. WinSnap 6.0.1 comes with a Windows 11-friendly facelift, a reorganization of its major tools and some useful improvements.
The biggest improvement is immediately apparent when the program first opens -- it now boasts a modern UI in keeping with the Windows 11 desktop, complete with support for automatic switching between dark and light modes.

The Last of Us Part 1 bombs on PC
The long awaited first part of the previously PlayStation exclusive The Last of Us game has been released on March 28, 2023 on Steam. The remastered version of the game has received praising reviews for PlayStation, but when you check the Steam ratings one day after release, you notice that they are mostly negative on the site.
In numbers, more than 4,200 of the 5,740 reviews are mostly negative, and this leads to the question how this could have happened. From Game of the Year to one that sits at the bottom of Steam’s ranking charts.

Get 'Difficult Decisions' (worth $18) for FREE
What do you do when the algorithm doesn’t have the answer?
Countless tools and frameworks claim to make decisions objective and bias-free. But in reality, the defining decisions that leaders face are complex ones with subjective information sources and conflicting courses of action. That’s why the toughest choices are left to the leaders, and that’s why formulas won’t answer them.

System76 refreshes Gazelle Linux laptop with Intel Core i9-13900H CPU and NVIDIA GeForce RTX 3050 GPU
Today, System76 unveils the latest generation of its Gazelle laptop. The Gazelle is a powerful and versatile laptop that is perfect for a wide range of users. It is a great choice for creative professionals, gamers, and anyone who needs a powerful laptop for work or play.
The Gazelle is powered by the 14-core Intel Core i9-13900H processor, which offers a max clock speed of 5.4Ghz. This new CPU provides up to 8 percent better performance compared to the previous generation of the Gazelle laptop. The computer also features an NVIDIA GeForce RTX 3050 GPU, which delivers exceptional performance for both gaming and graphics-intensive tasks.
Amid ChatGPT's rise to fame, how can enterprises work to eliminate AI bias?
Artificial intelligence continues to hog the headlines, as more people discover the power of tools like OpenAI’s DALL-E 2 and especially ChatGPT. These futuristic-seeming tools work by taking a human’s query or prompt and returning an intelligent textual or visual response.
From an enterprise perspective, AI adoption is growing rapidly. According to Forrester, spending on AI software is set to accelerate from $33 billion in 2021 to $64 billion in 2025 -- growing twice as fast as the overall software market. But while tools like ChatGPT may seem like magic, it’s important to understand these solutions aren’t perfect.

60 percent of organizations have had authentication breaches in the last year
Insecure authentication is a primary cause of cyber breaches and cumbersome login methods take an unacceptable toll on employees and business productivity, according to a new report.
The 2023 State of Passwordless Security Report, released by HYPR and Vanson Bourne, shows that 60 percent of organizations have reported authentication breaches over the last 12 months and that three out of the top four attack vectors are connected to authentication.

Get 'Cloud Native Security' (worth $24) for FREE
Cloud Native Security delivers a detailed study into minimizing the attack surfaces found on today's Cloud Native infrastructure.
Throughout the work, hands-on examples walk through mitigating threats and the areas of concern that need to be addressed. The book contains the information that professionals need in order to build a diverse mix of the niche knowledge required to harden Cloud Native estates.

Smaller means safer as bigger businesses see more endpoint infections
Of businesses with between 21 and 100 protected endpoints, only five percent encountered a malware infection in 2022. For smaller firms with one to 20 endpoints, the rate is 6.4 percent, but as companies grow so do infections.
For businesses between 101 and -500 endpoints the rate rises to 58.7 percent and over 500 it's 85.8 percent. These findings are from a new report by OpenText Cybersecurity which looks at the latest threats and risks to the small and medium business (SMB) and consumer segments.

Phishing emails soar as messages bypass standard email security solutions
A new report shows that 2022 saw a 569 percent increase in malicious phishing emails and a 478 percent increase in credential phishing-related threat reports published.
The report from Cofense also looks at emails bypassing SEGs and hitting users' inboxes and highlights that delivery methods for carrying out phishing campaigns continue to keep up with the advancement of technology. Cofense has witnessed a continued blending of tactics to make detection and mitigation even more difficult for organizations.

API attacker activity up 400 percent in six months
The latest State of API Security Report from Salt Security shows a 400 percent increase in unique attackers in the last six months.
In addition, around 80 percent of attacks happened over authenticated APIs. Not surprisingly, nearly half (48 percent) of respondents now say that API security has become a C-level discussion within their organization.

Getting the most value out of your data [Q&A]
The past few years have seen a boom in digital transformation as enterprises have sought to modernize their operations to take advantage of a new, more flexible world of work.
But this change has often led to unwieldy data structures that are difficult to manage, which means that extracting value from the data is harder than it should be.

Spotify launches powerful new playlist feature called Niche Mixes
Spotify has launched a new personalized playlist option which gives users a unique way to create mixes to suite any mood, occasion or activity.
The company describes Niche Mixes as "a set of personalized playlists that combines all that our Mixes offer in a playful way". What this means in practice is that you can search for an "activity, vibe or aesthetic" (running, 80s, meditative, for instance), add the word "mix", and you'll be provided with a custom playlist to suit.

Microsoft's Windows 12 plans revealed
Adoption of Windows 11 may well be much slower than Microsoft would have hoped or expected, but this isn't stopping the company forging ahead with its successor. The project is currently dubbed CorePC, but it is being referred to by many as -- naturally -- Windows 12.
What can be expected from Windows 12? Leaks from sources close to the company mean that plans for the next generation of the operating system have been exposed. Predictably, Microsoft is said to be leaning heavily on AI as it looks to modernize Windows. There is also a strong focus on security and faster delivery of updates on the cards.

Microsoft releases KB5023778 update for Windows 11 bringing fixes, taskbar improvements and Start menu notifications
Microsoft has released a new cumulative update for Windows 11 22H2 that sees the arrival of Microsoft account notifications in the Start menu. There are also new features and improvements in Microsoft Defender for Endpoint.
The KB5023778 update is a preview of the update that will be released more widely next Patch Tuesday, and as such it is an optional update that you will need to manually install. Installing KB5023778 not only adds Start menu features, but also updates the taskbar search box, adds new functionality and fixes a large number of issues that have been found in Windows 11.



