
How to measure UI/UX design impact on business
UI/UX design refers to the process of creating interfaces that users can interact with on digital platforms. The UI (User Interface) is the graphical layout of an application while the UX (User Experience) refers to the overall experience a user has when interacting with a digital product or service. UI/UX design encompasses several elements such as visual design, interaction design, information architecture, and user research.
Measuring the impact of UI/UX design on business is essential as it helps companies to understand the effectiveness of their designs in achieving their business goals. A well-designed user interface can lead to increased user satisfaction, retention, and revenue. Therefore, businesses need to have a clear understanding of how UI/UX design impacts their business to make informed decisions about design investments.

The defining characteristics and roles of an enlightened CIO
A company’s chief information officer (CIO) is responsible for overseeing the people, processes and technologies that comprise its IT environment to support business objectives. In today’s information-focused business landscape, the performance of an organization’s CIO is often critical to its overall success.
The CIO’s role and the specific responsibilities of the position have undergone significant evolution and now demands a more enlightened and holistic approach to the issues that affect the way IT impacts the current and future goals of the business.

20 percent of endpoints have legacy security vulnerabilities
According to a new report, at least 20 percent of enterprise endpoints remain unpatched after the remediation is completed, meaning that a fifth of machines still have a significant number of legacy vulnerabilities that could be exploited at any time.
The study of over 800 IT professionals from Action1 Corporation finds 10 percent of organizations suffered a breach over the past 12 months, with 47 percent of breaches resulting from known security vulnerabilities.

Get 'Digital Etiquette For Dummies' for FREE
Conducting yourself online can be challenging. It sometimes seems like the web and social media is tailor-made to cause upset and anger. But, with the right guide, anyone can learn how to be a beacon of civility and politeness online.
In Digital Etiquette For Dummies, a team of online communication experts share their combined insights into improving your presence on social media, writing emails that exude positivity and clarity, behaving correctly in virtual meetings, and much more.

Are you sure about this? Confidence in modernization projects drops as they progress
When preparing for modernization, 70 percent of companies are confident or very confident in their understanding of their applications.
However, a new report from EvolveWare shows the high confidence level drops as companies plan their modernization project (41 percent) and begin their project (28 percent), suggesting that organizations only start to understand the level of knowledge needed for these efforts after they are further into their planning or execution.

Google Cloud integrates with Shopify to combat search abandonment
As we reported recently, delivering relevant search results on websites can be hard to achieve and for retailers this can lead to searches being abandoned and sales lost.
To address this issue, Google Cloud is announcing a new integration with eCommerce platform Shopify to allow sites to deploy advanced search and browse experiences using Google Cloud.

The latest Windows 11 Release Preview build includes new features not found in Canary, Dev or Beta releases
Ordinarily Microsoft uses the less stable Windows Insider channels to try out new Windows 11 features -- something the company reiterated when it launched the ultra-cutting edge Canary channel.
But this week saw the release of a new build of Windows 11 to the Release Preview channel, the channel which is the final stage of testing before a build gets full public release. And this time around, things were a little different because the Release Preview build includes brand new features that have not been seen in other builds -- including notifications for Microsoft accounts in the Start menu.

New solution helps enterprises manage cloud assets
As organizations turn increasingly to the cloud they face the challenge of understanding not just the cost but also the value of their operation.
To help organizations maximize business value from their technology investments, Flexera is launching a new solution that strengthens an enterprise's FinOps and cloud central teams, while allowing the convergence of IT asset management (ITAM) and FinOps.
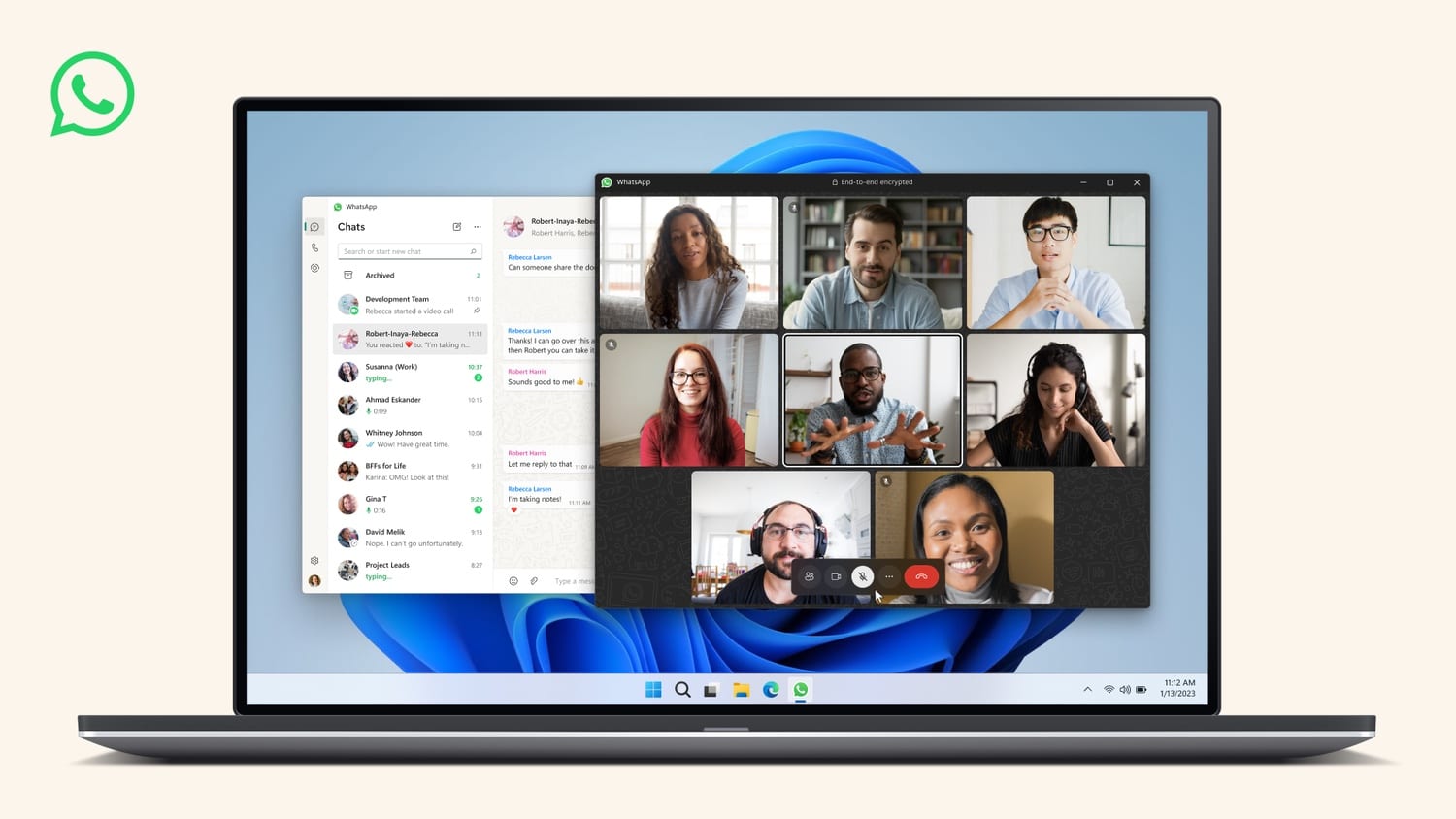
There is a new, faster version of WhatsApp for Windows with improved calling features
While WhatsApp is most commonly used on mobile devices, growing numbers of users are adopting the desktop version of the app. Meta has just announced the release of a significantly improved version of the Windows app.
Speed is a key upgrade here, with load times being reduced, but there are also feature improvements. The latest version of WhatsApp for Windows now supports larger group video and audio calls.
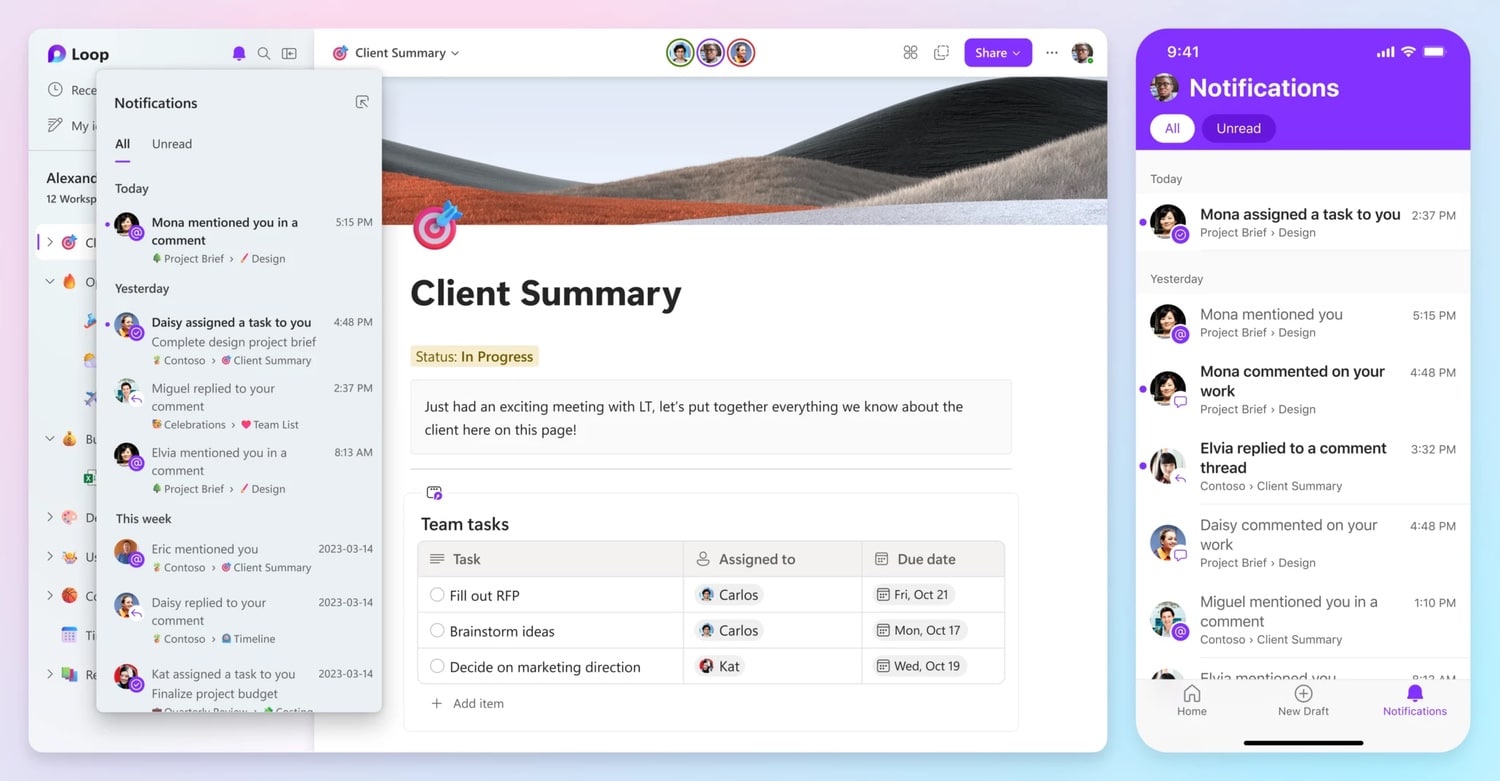
Collaborative working app Microsoft Loop is now available in public preview
Microsoft has announced the availability of a public preview of its new collaborative working app, Loop. The public launch follows a period of private previews with enterprise customers.
Microsoft Loop is available on the web, as well as for iOS and Android, and it allows teams to work together in shared workspaces that integrate neatly with Microsoft 365 apps. The app competes with the likes of Asana and Notion and has been in development for a couple of years. As you might expect, there is a dash of AI thanks to Microsoft 365 Copilot's support for Loop.

Microsoft panics Windows 11 users with 'Local Security Authority protection is off' warning
Users of Windows 11 have been concerned by the appearance of a message that reads: "Local Security protection is off. Your device may be vulnerable". Microsoft is blaming a recent update (KB5007651) for the warning which implies that an important security feature has been disabled.
The issue affects Windows 11 version 21H2 and 22H2, and those hit by the message have been left confused about what they need to do. So what is going on?

BenQ PD2706UA is a 27-inch 4K UHD professional designer monitor
BenQ has established a reputation for producing high-quality monitors that cater to the needs of various users, and the PD2706UA is no exception. This monitor has been designed specifically for creative professionals who require the best possible color accuracy, resolution, and viewing angles.
The PD2706UA is a 27-inch monitor that boasts a QHD resolution of 2560 x 1440. The display is made with an IPS panel that provides excellent color reproduction and wide viewing angles. This makes it ideal for professionals who require accurate color representation, such as graphic designers, photographers, and videographers.

GNOME 44 'Kuala Lumpur' is finally here
There are many great desktop environments for Linux, such as Cinnamon, KDE Plasma, and MATE to name a few. With that said, only one can be the best, and that is obviously GNOME. Look, folks, there's a reason Canonical uses it as the default DE for Ubuntu -- it's that good.
If you are a GNOME fan, I have some extremely exciting news. You see, as of today, GNOME 44 is officially here! Named "Kuala Lumpur," this version of the desktop environment is loaded with new features. Most notably, the Software app has received several enhancements, including an improved user interface and better error messages. You can read the full release notes here.

Get 'Hands-On Software Architecture with Java' (worth $41.99) for FREE
Java, the most widespread technology in current enterprises, provides complete toolkits to support the implementation of a well-designed architecture.
Hands-On Software Architecture with Java starts with the fundamentals of architecture and takes you through the basic components of application architecture. You'll cover the different types of software architectural patterns and application integration patterns and learn about their most widespread implementation in Java.
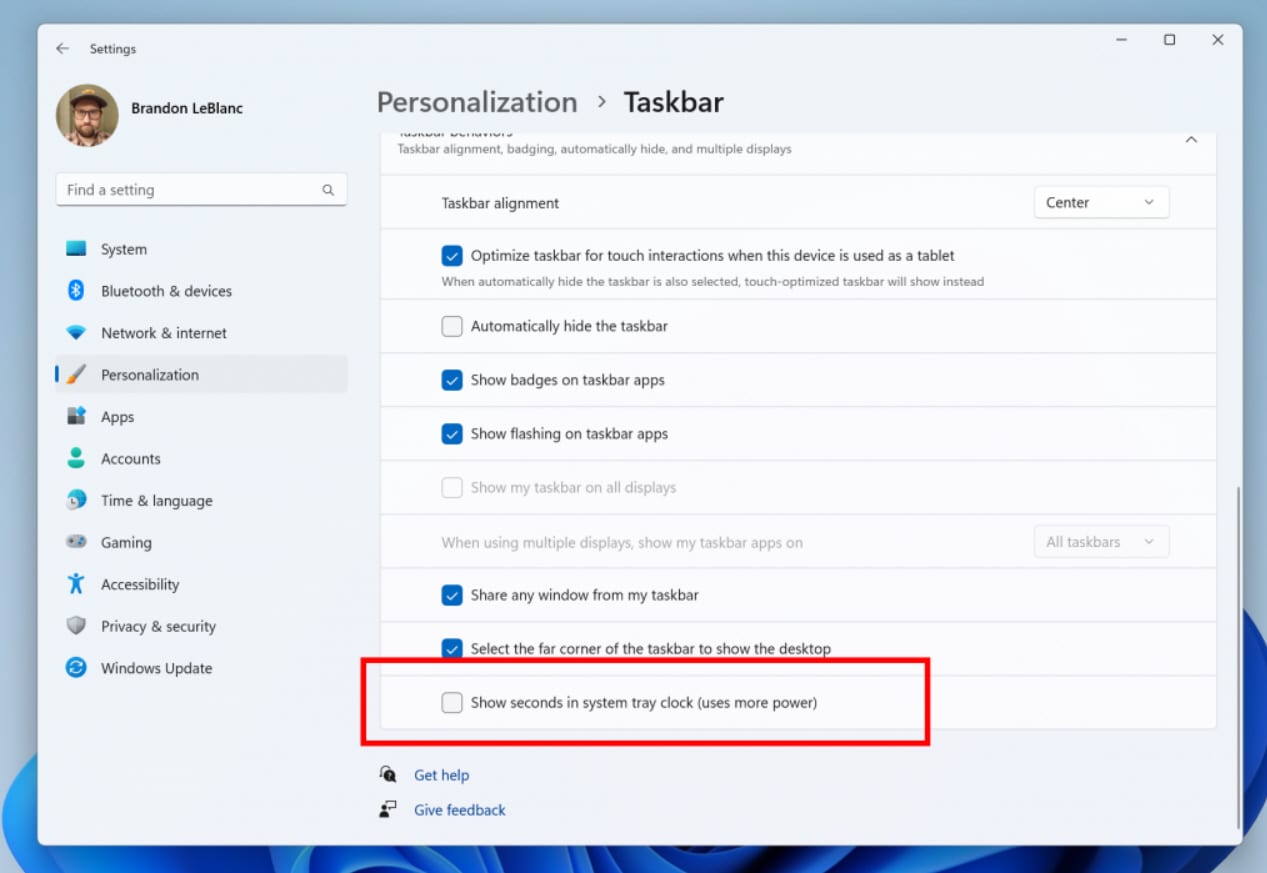
Windows 11 Build 23419 can show seconds in the system tray clock -- but the new feature comes with a warning
It’s business as usual for Windows 11 Insiders in the Dev Channel as Microsoft today releases a fresh test build for the new operating system.
Windows 11 Build 23419 comes with several new features, including introducing the ability to show seconds in the clock on the system tray. This welcome-sounding addition won't appeal to everyone, however.



