Microsoft says it will not be possible to bypass Windows 11 system requirements

Windows 11 is now just a matter of months away, and system requirements are a concern. While this is not going to be a problem for anyone buying a new computer with the operating system pre-installed, it is a major consideration for anyone upgrading to Windows 11 from Windows 10.
The requirement for TPM 2.0 is something that has attracted particular attention. While Microsoft has made it clear that for OEM customers with special requirements the TPM need can be eliminated with a custom Windows 11 image, the same is not true for the average user. Although a registry hack currently exists that makes it possible to bypass the need for TPM 2.0, Microsoft has stressed that it will not be possible to use Group Policy to get around hardware requirements -- possibly meaning that the registry hack will also not work once Windows 11 is released.
Samsung Odyssey Neo G9 curved gaming monitor uses Mini LED display technology

There are two curved displays in my home -- a computer monitor in my office and a television in my living room. Both look stylish, but truth be told, the curve doesn't make any difference when watching TV. Since I sit far back from the television, the curve doesn't add any benefit. On the computer monitor where I sit much closer, however, the curvature lends to a more immersive experience. I can't recommend curved computer monitors enough -- for both gaming and productivity.
Today, Samsung announces its latest monitor, and it is very special. Called "Odyssey Neo G9," the 49-inch display is significant for being the first-ever curved gaming monitor to use Mini LED technology.
Avoiding the big bang data migration

Data migrations are by their very nature high risk initiatives and, if not planned effectively, they can create a significant headache for both the IT team and the organization. That’s because modern technology transfers are massively complex undertakings. However, data migration problems can often be traced back to confusion and disorganization surrounding the migration plan (if one is in place) and a failure to adequately prepare for the move.
Additionally, every company’s data landscape is unique. It may encompass everything from legacy systems to homegrown one-off databases, each with its own level of support. Documentation may be non-existent, institutional knowledge may be limited, and key staff may have left. This makes the task much more complex to undertake.
What does the Edge mean for IoT?

A lot has been written about the IoT revolution and how the technology has the capability to revolutionize industries, transform productivity and unlock new levels of insight. But for those intrigued by the possibilities and looking to dip their toe in the water, the potential myths of high price point, infrastructure and connectivity challenges, as well as the required skill set can be significant hurdles that seem insurmountable.
In addition, especially when it comes to the reality of industrial IoT, the cost, time and disruption that goes into a brand new facility -- the prospect of having to rip and replace new infrastructure to support IoT just isn’t a viable option for many businesses. So what’s the alternative? In this article I'll explain how edge IoT and analytics can provide a powerful mechanism for translating complex data sources into a streamlined, lower cost platform with faster return on investment and higher value. First, let's consider some of the key challenges businesses face when considering an investment in IoT.
Is detection of ransomware the key solution for small business rather mitigation?

According to Checkpoint Research, ransomware attacks have surged significantly, hitting a double-digit increase of 93 percent year-on-year. As of June 2021, the number of organizations impacted by ransomware has risen to 1,210. This exponential rise is also attributable to the migration to remote work globally. The amount paid by victims of these attacks has increased by almost 300 percent in 2020 alone
These staggering statistics paint a grim picture of the security threat that companies face. As early as July 2021, as many as 1,500 businesses world-wide have been affected by ransomware attack -- REvil. The group has reportedly used Kaseya IT software as backbone for this notorious attack. Around $70 million dollars were demanded from the affected companies to restore business data. The companies that majorly came under the radar were supermarkets, IT companies -- primarily small to medium sized, schools and kindergartens
Mainframe applications still key to business strategy

According to a new study from the IBM Institute for Business Value, 71 percent of executives surveyed say mainframe-based applications are central to their business strategy.
Also, in three years, the percentage of organizations using mainframe assets in a hybrid cloud environment is expected to increase by more than two times.
Novostella brings it all to automated lighting [Review]

Home automation continues to grow in popularity at an ever-increasing rate. The market value is expected to reach $114 billion by 2025, with smart lighting products accounting for 25 percent of that.
It’s hard to say where the average user begins with home automation, but we’d argue it’s likely to be with a smart lightbulb for most of them. It’s a product that seems straightforward and doesn’t have the dangers of locking you out of your house (as a smart lock could) or making you feel like you’re either in a) Death Valley, or b) Nome, Alaska (unlike a smart thermostat).
Cybercriminals work together to drive greater profits

Cybercrime is getting more organized than ever, as threat actors increase collaboration and adapt methods to drive greater monetization, selling access to breached systems to organized criminal groups and ransomware gangs.
The latest HP Wolf Security Threat Insights Report, reveals a 65 percent rise in the use of hacking tools downloaded from underground forums and file sharing websites between the second half of 2020 and the first half of 2021.
Businesses continue to struggle with app security

Threats to web, mobile and API-based apps are developing rapidly and the average time taken to fix them isn't improving, with critical vulnerabilities remaining open on average for 202 days.
NTT Application Security has released its latest AppSec Stats Flash report looking at the current state of application security and the wider threat landscape. It finds the utilities sector the worst, with with 66 percent of applications in the industry having at least one serious exploitable vulnerability throughout the year.
IT leaders think remote workers are more at risk but struggle to protect them

A new survey of enterprise IT security leaders shows almost 80 percent believe remote workers are at more risk from phishing attacks now because they're isolated from their organizations' security teams.
The study from Egress also reveals that more than 59 percent of respondents feel solutions such as video training (27 percent), email reminders (20 percent), and VPNs (12 percent), are sufficient by themselves to keep organizations safe from the biggest security breach fears: damage to brand and reputation, and legal jeopardy.
Amazon denies cryptocurrency rumors, and Bitcoin drops in value

The ever-volatile price of Bitcoin took another turn as Amazon denied recent rumors that it is looking to accept the cryptocurrency as a form of payment.
Speculation about the online retailer's embrace of Bitcoin and other cryptocurrencies, as well as rumors of tokenization, caused a Bitcoin surge at the weekend. But now the company has spoken out to deny the suggestions, the value has tumbled again.
Microsoft will continue to issue 'C release' patch previews for Windows 11

Keeping Windows up-to-date has always been important, from a security point of view. While patches and updates can be released at any time they are needed, Microsoft uses the monthly Patch Tuesday to roll out updates on a regular basis -- so-called 'B releases'.
With Windows 10, the company has long-issued previews of these updates in the form of 'C releases'. Now Microsoft has confirmed that this is something that will continue with Windows 11.
Torrent site YTS loses control of its domain

Torrent sites remain just as popular as ever, as people continue to seek ways to grab copies of the latest blockbuster movies to watch free of charge. While the Pirate Bay is probably the most famous torrent site out there, it is closely followed by YTS.
But anyone trying to visit yts.mx will find that the site is inaccessible after the domain was put on hold by its registrar. It is not entirely clear what is happening, but legal issues are thought -- unsurprisingly -- to be involved.
Now you can block spam file sharing on Google Drive
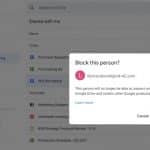
Google has a spam problem -- and we're not talking about Gmail, but Google Drive. Having discovered that the file sharing functionality of the cloud storage platform could be used to harass people, spammers have been doing exactly that.
Having announced plans to do something about the problem back in May, Google has finally started the process of roiling out anti-spam measures, giving users the ability to block spammers. While many Google Drive users will be pleased at the introduction of new controls, is it enough?
Logitech launches LINE FRIENDS Bluetooth Mouse and Keyboard Combo

The Logitech K380 Keyboard and M350 Mouse Combo is a very simple and elegant solution for controlling multiple devices. The keyboard can be paired to a Windows PC, Mac, and iPhone, for example, and then you can easily switch between them by pressing buttons -- no need to pair again every time. It is particularly great for those that dual boot on a single machine, such as with Linux and Windows.
The keyboard and mouse are quite cute already -- they have rounded keys and can be had in either pink or white colors. But now, Logitech is making them even cuter. You see, today, the company launches LINE FRIENDS variants, featuring the BROWN and CONY mascots form the popular LINE messaging app. If you aren't familiar with the bear and bunny rabbit, don't feel bad -- they are apparently far bigger in Asia than America.
Most Commented Stories
© 1998-2024 BetaNews, Inc. All Rights Reserved. Privacy Policy - Cookie Policy.




