Satechi launches Thunderbolt 4 Multi-Display Docking Station

Satechi has unveiled its latest offering: the Thunderbolt 4 Multi-Display Docking Station. Tailored for professionals, this docking station boasts cross-platform compatibility, supports up to four external monitors, and delivers up to 8K/60Hz video output along with 96W of charging power to the host device. Its sleek Space Gray design, crafted from aircraft-grade aluminum with chamfered edges, features conveniently labeled ports and a slim profile that integrates seamlessly into any work environment.
Adding to its robust Thunderbolt 4 lineup, Satechi’s new docking station distinguishes itself from the 2023 Thunderbolt 4 Multimedia Pro Dock by including Thunderbolt 4 downstream ports and DisplayLink software for additional external monitors. The Thunderbolt 4 Multimedia Pro Dock remains a solid choice for those with legacy products, focusing on USB-A ports and offering vertical docking.
Grab your free copy of 'JavaScript Essentials For Dummies' today

JavaScript Essentials For Dummies is your quick reference to all the core concepts about JavaScript -- the dynamic scripting language that is often the final step in creating powerful websites.
This no-nonsense book gets right to the point, eliminating review material, wordy explanations, and fluff. Find out all you need to know about the foundations of JavaScript, swiftly and crystal clear. Perfect for a brush-up on the basics or as an everyday desk reference on the job, this is the reliable little book you can always turn to for answers.
TP-Link launches TL-WR1502X travel router

TP-Link has introduced the TL-WR1502X, a new travel router. This compact device not only offers the latest Wi-Fi 6 technology but also boasts a host of features perfect for anyone needing reliable internet on the move.
The TL-WR1502X is capable of reaching impressive dual-band Wi-Fi speeds up to 1.5 Gbps, making it perfect for high-demand online activities like 4K streaming, large file downloads, and smooth video calls. Whether traveling, camping, or working remotely, this router ensures that connectivity is never compromised.
EssentialPIM 12.0 unveils improved contact management and email tools
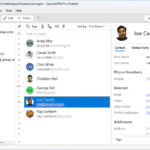
Astonsoft Ltd has released EssentialPIM 12.0, a major new version of its email client and organizer for Windows. Available in free and Pro versions, the latest release focuses on improving its contact management section and email tools.
There are two notable improvements to EssentialPIM’s Contact Management tool. The first is the implementation of a new default view displaying user initials or a photo next to each contact entry to aid finding the right contact. In addition, contact details have been redesigned so that a complete overview of each contact can be found in a single location.
Rising breach numbers drive zero-trust adoption

Two-thirds of organizations responding to a new survey list cyber risk concerns as the most important drivers for implementing a zero-trust strategy.
A new report from the Entrust Cybersecurity Institute, based on research by the Ponemon Institute, shows the pattern is even more pronounced in the US, with 50 percent of organizations citing cyber breach risk and 29 percent reporting the expanding attack surface for a combined total of 79 percent.
Logitech launches new 'Logi for Mac' product line

Logitech has introduced its latest 'Logi for Mac' lineup, featuring cutting-edge MX series devices and ergonomic solutions designed specifically for Apple users. The newly revealed products, including the MX Keys S for Mac and Ergo Wave Keys for Mac, aim to elevate performance, productivity, and comfort for macOS and iPadOS users.
Delphine Donné, Logitech's vice president and general manager of Personal Workspace Solutions, emphasized the company's dedication to innovation and sustainability. "Our Designed for Mac portfolio is crafted to enhance the Apple user experience through improved workflow, productivity, and comfort, without compromising on Mac compatibility," said Donné.
Get 'The Software Developer's Guide to Linux' (worth $31.99) for FREE

Developers are always looking to raise their game to the next level, yet most are completely lost when it comes to the Linux command line.
The Software Developer's Guide to Linux is the bridge that will take you to the next level in your software development career. Most of the skills in the book can be immediately put to work to make you a more efficient developer. It’s written specifically for software engineers, not Linux system administrators, so each chapter will equip you with just enough theory to understand what you’re doing before diving into practical commands that you can use in your day-to-day work as a software developer.
Redefining security in mobile networks with clientless SASE

As organizations adapt their IT ecosystems to incorporate IoT devices and expand remote working opportunities allowing employees to use personal mobile devices, enterprise mobility has become indispensable in modern business operations. Nonetheless, this shift presents numerous security challenges and lifecycle management considerations, especially given that mobile devices connecting to networks frequently lack compatibility with traditional security solutions such as Virtual Private Networks (VPNs) or endpoint tools.
Mobile Network Operators (MNOs) and Mobile Virtual Network Operators (MVNOs) are at the forefront of this challenge. These service providers are tasked with the dual responsibility of ensuring optimal connectivity while safeguarding data privacy and user experience. As the market for basic connectivity services becomes increasingly commoditized, these operators are compelled to explore new avenues for revenue through value-added services. Among these, security services stand out as a promising opportunity.
It's not all artificial: The 4 types of intelligence CTOs need to get the most out of AI

Enterprises plan to spend roughly $35.5 million on IT modernization in 2024, with over a third going to AI to boost productivity. But it’s not all sunshine and rainbows. At the same time, 64 percent of IT leaders worry about rushing to adopt generative AI without understanding what's needed to use it effectively and safely. And while 75 percent of organizations have experimented with generative AI, only 9 percent have adopted the technology widely. There’s so much more potential to tap into.
To get the best out of AI to supercharge operations it all comes down to intelligence. Afterall, AI is only as intelligent as those using it. There are the four types of intelligence that CTOs need to build, and it’s nothing to do with coding or super complicated technology. It’s about cultivating soft skills and human talent to control AI in a responsible way.
Microsoft releases the surprisingly feature-packed KB5037853 update for Windows 11

It is the time of the month when Microsoft releases previews versions of the following month's updates for Windows, and this week this means the KB5037853 update is available for Windows 11.
As this is a preview, it does not include security fixes and is optional. But the KB5037853 update for Windows 11 is significant because it adds a large number of features to the operating system. In addition to updating sharing options, it also fixes bugs and starts the rollout of the new account manager on the Start menu.
Compliance and cybersecurity in the age of AI [Q&A]

Artificial Intelligence is dramatically transforming the business landscape. It streamlines operations, provides critical insights, and empowers businesses to make data-driven decisions efficiently. Through machine learning, predictive analytics, and automation, AI assists in identifying trends, forecasting sales, and streamlining supply chains, leading to increased productivity and improved business outcomes. It isn't, unfortunately, without problems.
We talked to Matt Hillary, Vice President of Security and CISO at Drata, about the issues surrounding AI when it comes to critical security and compliance.
Framework launches upgraded Laptop 13 with Intel Core Ultra processors

Framework has unveiled the latest iteration of its Laptop 13, now equipped with Intel Core Ultra Series 1 processors, a high-resolution 2880x1920 120Hz display option, and a new 9.2MP webcam. The new webcam technology borrows techniques from modern smartphone cameras, delivering superior low-light performance and clearer audio with its upgraded microphones.
This year’s model marks the fourth generation of Framework Laptop 13 utilizing Intel processors, each iteration benefiting from significant performance enhancements. The latest Intel Core Ultra Series 1 processors offer substantial improvements in efficiency and battery life, notably during video playback. These processors support up to 96GB of DDR5 memory and feature a blend of 6 Performance and 8 Efficient cores, which elevate both productivity and gaming capabilities.
Unlocking cybersecurity success: The need for board and CISO alignment

The C-Suite’s perception of cybersecurity has evolved dramatically over the past decade. It’s gone from being an afterthought for technology departments to worry about, to a cornerstone for business survival and operational strategy. The heightened awareness of cybersecurity stems from a deeper grasp of the legal, reputational and financial implications of data breaches. This, combined with regulatory pressures such as the original NIS directive, has forced leaders to enhance their organizations’ cybersecurity measures.
The result is that 75 percent of organizations now report that cybersecurity is a high priority for their senior management team. While on the surface this should be celebrated, when digging deeper, conversations between CISOs and the wider C-Suite often just revolve around high-profile or user-centric security risks. More technical and advanced threats such as those related to application security are overlooked. The race to embrace AI and increasingly complicated cloud infrastructures have also made communicating cybersecurity priorities even more difficult for CISOs.
Out of the shadows and into the light: Embracing responsible AI practices amid bias and hallucinations

The path to widespread AI is a bumpy one. While its potential to enhance consumer experiences and streamline business operations through personalization, autonomy, and decentralized reasoning is evident, the technology comes with inherent risks.
AI can produce conclusions that aren’t true, spread misinformation and in some cases, perpetuate existing biases. This -- the darker side of AI’s impact -- can leave business leaders facing financial, legal, and reputational damage.
Balancing security and autonomy: Strategies for CISOs in the cloud era

Maintaining a secure cloud environment is one of the most important responsibilities of any CISO today, given that over 50 percent of all cyberattacks now originate in the cloud. However, this is a daunting task, as security must now be balanced against other priorities such as maintaining agile operations and the need to innovate.
Organizations today are racing to accelerate their cloud adoption due to the need for greater scalability and cost-efficiency. It has, therefore, become a critical business strategy to ensure efficiency, accessibility, and sustainability in operations. As a result, cloud investments are soaring across the board. Gartner predicts that end-user spending on public cloud services will reach $679 billion by the end of this year and exceed $1 trillion by 2027.
© 1998-2024 BetaNews, Inc. All Rights Reserved. Privacy Policy - Cookie Policy.




