
Download Debian Linux 10.10 'Buster' now
Windows 11 may be the name of the upcoming version of Microsoft's desktop operating system, but that doesn't mean there's anything wrong with the number ten. For instance, one of the most popular Linux distributions, Debian, currently sits at version 10 (Code-named "Buster").
Actually, taking the number ten even further, Debian 10.10 is now available for download. Yes, this is the tenth point release of the tenth version of the wildly popular operating system. Those that believe in numerology may see significance in this versioning. Current Debian users should update their packages immediately, as 10.10 is chock full of important bug fixes and security updates.

iPhones have a weird Wi-Fi bug
A security researcher has discovered a strange iPhone bug that breaks wireless internet connectivity.
Self-proclaimed reverse engineer Carl Schou found that simply connecting to a network with an SSID containing particular characters "permanently disabled" his iPhone's Wi-Fi functionality. Although Apple is yet to acknowledge that there is a problem, it has been tested and confirmed by many users.

Microsoft fights back against Windows 11 leak
Just a few days ago -- before it has even been officially announced -- Windows 11 leaked online and remains available to download from numerous sites. The Windows 11 ISO torrent spread like wildfire, and now Microsoft is fighting back.
The company has issued a slew of DMCA takedown notices to various sites it says are distributing "a leaked copy of the unreleased Windows 11". Unsurprisingly, an article entitled "How to Download and Install Windows 11 Right Now" caught the eyes of Microsoft lawyers.

Microsoft releases KB5003690 update to boost game performance and fix blurry text in Windows 10
Windows Insiders are among the first to get fixes for various issues with Windows 10 as Microsoft releases KB5003690 to address, among other things, problems with blurry text.
The KB5003690 update (Windows 10 build 19043.1081) is now available for anyone signed up for the Beta or Release Preview channels running Windows 10 21H1. Other fixes in this significant update include addressing poor game performance after installing KB5000842 or later.

Silicon Power launches Superior Gaming microSDXC card for mobile gamers
Every once in a while, a manufacturer will release a memory card that is branded for gaming. Consumers often wonder if there is anything different about these cards that will truly benefit gamers. The answer is largely no. A storage card that is designed for gaming is really just marketing hype. Sorry, but it's true.
With all of that said, today, Silicon Power launches what it calls a "Superior Gaming" microSDXC card. While it is intended to be used for the Nintendo Switch, it should also be a good choice for mobile gamers using an Android phone or tablet. The card will, of course, also work with any device that uses such a card, including Raspberry Pi, drones, digital cameras, and more.

Digital transformation: 5 steps your company must take to succeed instead of survive
COVID-19 has changed the way companies think about digital transformation because it has accelerated the need to increase business connectivity while operating from decentralized settings.
Chief Technology Officers (CTOs) have been tasked with keeping their places of business at the forefront of the latest tech innovations. In a recent Gartner survey, 47 percent of respondents said their CTO is dedicated to modernizing core technology infrastructure in order to spur innovation.

Why IT needs smarter cloud security
For IT and security professionals, the job of keeping the enterprise secure is becoming an ever more complex proposition. In addition to the fact that distributed working looks set to become a permanent feature, keeping up with a raft of emerging new technologies while dealing with the rising tide of cyber threats means there is a growing number of tasks to keep on top of.
With time and resources in short supply, gaining full visibility of data from across the entire security stack will be key to achieving better and more comprehensive threat detection. But maintaining robust policies and controls also depends on adopting technology that is able to adapt quickly and self-learn from user behaviors.

Edward Snowden: The untold story of how one patriotic American exposed NSA surveillance
Edward Snowden might not yet be a historical figure, but he certainly is a hero. He is the whistleblower of all whistleblowers, the American who blew the lid off of Washington's spying on private citizens. But Snowden’s leak revealed that it’s not just the U.S. government that is spying on virtually every American -- big American telecommunications companies are also helping them to spy as well.
Snowden’s upbringing is largely uneventful. His maternal grandfather was a Coast Guard rear admiral and his father was also an officer in the Coast Guard. His mother was a U.S. District Court clerk. His parents divorced around the time that he would have graduated high school in 2001, but Snowden is a high school dropout. After a nine-month absence due to mononucleosis, he simply took the GED exam and then began taking community college classes. Despite a lack of a bachelor’s degree, he worked at a master’s online from the University of Liverpool.

2021 cybercrime and protecting your data
2020 was a difficult year all around. Many organizations are still adjusting to the new landscape while trying to plan for the future. Cybercrime was at its prime in 2020 with global costs climbing as high as $1 trillion, according to CSIS research. Unfortunately, with the pandemic dragging on and an extremely drained remote workforce that still needs to be secured, there is every chance that cybercrime will be an even bigger headache in the months ahead.
Numerous aspects are aligning to create even more dangerous situations. Organizations that fail to identify and address these impending hazards will be at risk from increased cyber-attacks and data breaches. But these types of imminent disaster can be averted with the right plans. By aligning security efforts with business goals, redesigning infrastructure, and looking at new technologies, organizations can build resilience while setting themselves up for future success.

How to preserve consumer trust amid new data privacy regulations
Following the passing of Virginia’s Consumer Data Protection Act and the Washington Privacy Act currently making its way through the legislature, states across the country are working to expand consumer rights over their personal data. As rights requests emerge for enterprises affected by current and future data privacy regulations, businesses cannot trust the person making the request is who they claim to be. With fraud escalating as cybercriminals are taking advantage of online-only operations amid the COVID-19 pandemic, enterprises need to ensure they can authenticate users making rights requests to avoid the devastating repercussions of handing personal data to fraudsters.
This article will discuss new considerations for enterprises amid new state privacy regulations to keep data secured and out of cybercriminals’ reach.
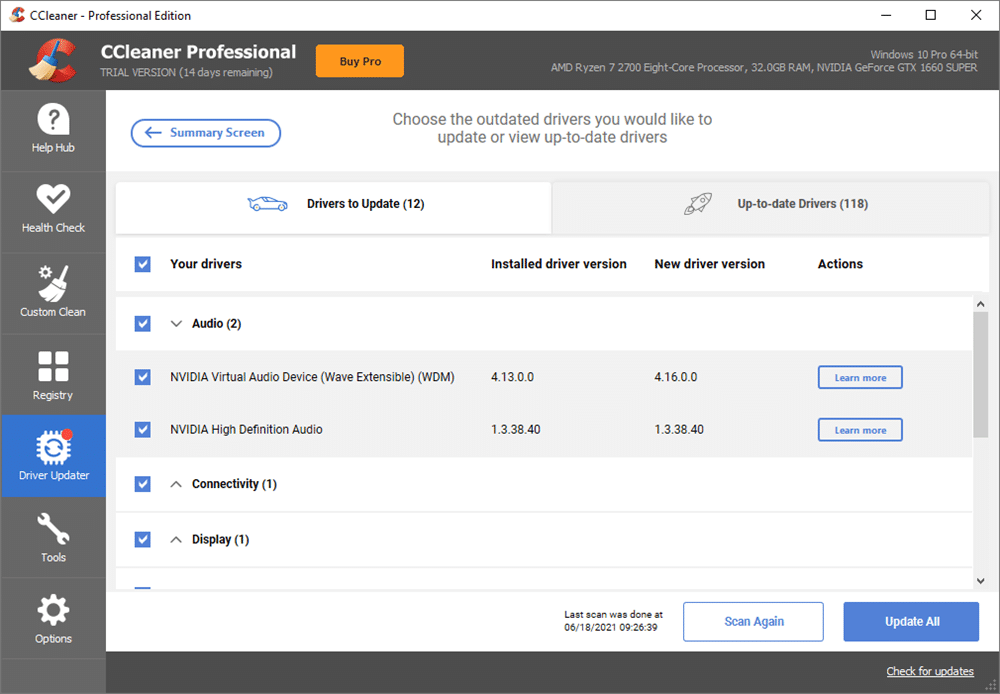
CCleaner 5.82 adds a driver updater to its formidable arsenal of maintenance tools -- save 30% on a Pro license now!
For years, millions of PC users have trusted CCleaner to keep their computers clean and running smoothly. Now Piriform has added a major new feature to the tool’s impressive roster with its latest release, CCleaner Professional 5.82.
That feature is a full driver updater tool, enabling users to check their computer for out-of-date drivers, plus apply updates quickly and easily.
Best Windows 10 apps this week
Four-hundred-forty-three in a series. Welcome to this week's overview of the best apps, games and extensions released for Windows 10 on the Microsoft Store in the past seven days.
Microsoft's upcoming Windows 11 operating system leaked online this week. You can download the wallpapers of the operating system already, in case you are interested.

Why open banking apps must stay secure to earn consumer trust [Q&A]
Traditional banks are realizing that they must develop more user-friendly open banking apps if they're not to lose customers to fintech startups.
But it's critical that these apps gain the trust of consumers if open banking is to succeed. We spoke to Jasen Meece, CEO of Cloudentity to discuss how financial services companies can ensure their open banking apps and partners adhere to compliance standards and protect consumer’s personal data.

Microsoft has stopped offering Windows 7 drivers via Windows Update
There have been many reasons to move away from the now-ancient Windows 7 for some time, and now there is another one. Microsoft will no longer offer driver updates via Windows Update for this version of the operating system.
The change comes a year and a half after support for Windows 7 came to an end, and also the expiry of the SHA-1 Trusted Root Certificate Authority for Windows 7 SP1, Windows Server 2008, Windows Server 2008 R2 last month. It is a slightly different story for anyone signed up for an Extended Security Update (ESU) program, however.

When will Windows 11 be released, and will it be free?
It is now less than a week until Microsoft officially tells us about Windows 11. The announcement is scheduled for June 24 and this is when the company will reveal all. The operating system may have already leaked, but there are still many questions we need answers to.
While this week's leak gave us a chance to see many of the new features that Microsoft has introduced as well as the new look, there are two key questions that people are asking. Firstly, when will Windows 11 be released? Secondly, will Windows 11 be a free upgrade?



