
Lexar unveils two new USB card readers
If you are into digital photography, picking a camera is only part of the equation -- you also need to buy a storage card. Nowadays, this is most likely going to be an SD card, but there are cameras that use other types, such as microSD and CompactFlash. If your computer doesn't have an integrated card reader, you may need to get a USB variant -- that is probably the easiest and fastest way to transfer the photos.
Over on Amazon, there are lots of USB card reader models to be had, but many of them are by unknown brands with questionable quality. Trust me, you don't want to corrupt or damage your card because you bought a cheap reader -- your photos are worth more than that. Instead, you should stick to a reputable brand. Today, one such brand, Lexar, unveils two new readers -- one is a 2-in-1 model, while the other is 3-in-1. Neither are revolutionary, but they look to be well-designed and are reasonably priced.
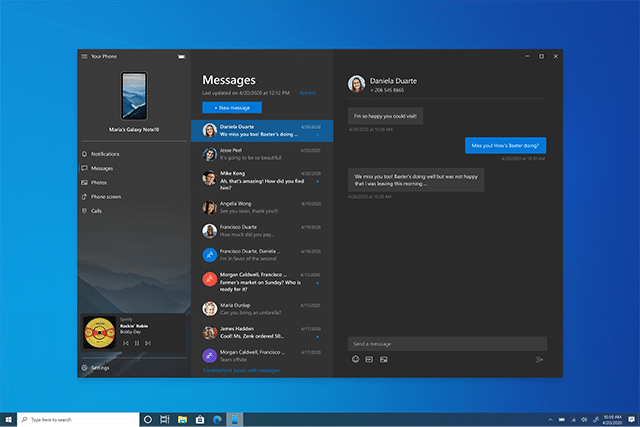
Microsoft's Your Phone app now lets you control music on your Android device directly in Windows 10
If you're a Windows 10 user, and you have a supported Android phone, then Microsoft's Your Phone is a great app to have as it bridges the gap between your different devices.
Microsoft has added a number of new features to the app over time, making it ever more useful, and today it announces it's adding the ability to control your Android music and audio apps using it. In other words, you can access and control the audio apps playing from your phone directly in Windows. Your songs will remain in sync between your phone and PC, and you can switch between multiple sources in the player too.

Evolution of privacy protection over the coming years
The war over data privacy has been raging for 25 years and is far from over. Large corporations, states and criminal networks are improving tracking tools, trying to dictate their own rules, and control and manage people's need to protect their personal data. The issue of privacy is getting unbelievable traction on different levels, including the GDPR (General Data Protection Regulation) and CCPA (California Consumer Privacy Act).
The value of personal data is constantly increasing, as it's getting harder to collect, and the possibilities of making money on it are endless. Will users ever be able to decide for themselves what information they are willing to share? To address this question, let's move away from individual cases and look at how privacy protection technologies in general will develop in the coming years.

Microsoft releases Windows 10 Insider Build 19619 to the Fast ring
If you’re feeling a little bored in lockdown, here’s Microsoft with a new Windows 10 build to entertain Insiders on the Fast ring.
Well, 'entertain' might be pushing it as there’s nothing too exciting in this new build. It’s mostly just fixes.
Why payroll security is even more essential now remote work is the norm
The COVID-19 pandemic is changing the way people work and do business. As governments worldwide impose compulsory community quarantines and lockdowns, many are turning to the internet to continue operating their businesses or doing their jobs. Teleworking is becoming the new normal with everyone expected to observe physical distancing to avoid the pandemic spreading.
Among other systems, payroll is one of the workflows worth examining amidst the changes brought about by the pandemic. As companies adopt remote work arrangements to avoid complete operational shutdown, those that have been manually processing their payroll need to find ways to adjust to the new situation.

Google Meet is now free for everyone, making it a viable alternative to Zoom
It's only a few days since Facebook launched Messenger Room to serve as an alternative to video conferencing service Zoom. Now Google is getting in on the action, making is own video meeting tool available for free.
Google Meet has been opened up to everyone with a Google account -- previously only people with a paid-for G Suite account were able to start calls. From now until September meetings of any length involving up to 100 people are completely free, but at the end of September some restrictions will be introduced.

Clumio adds Microsoft 365 protection to its SaaS enterprise backup solution
Enterprises and their data are vulnerable, perhaps more so than ever right now, with COVID related phishing scams booming.
Backup specialist Clumio is adding Microsoft 365 to its secure backup as a service offering, providing organizations running Microsoft 365 with a globally consolidated data protection service.

Four things every enterprise needs to consider to emerge healthy
The technology industry has always moved quickly, but COVID-19 is putting companies’ flexibility and adaptability to the test. Although employees are increasingly working remotely, few organizations were prepared to go 100 percent virtual within the matter of a week or two while attempting to understand what life in a pandemic looks like.
As the shock and awe of self-isolating practices and quarantines wears off, there are some things enterprises need to consider in order to not just remain in business but ultimately emerge "healthy."

Tax season is on, so are the scammers
The Better Business Bureau (BBB) recently issued a statement confirming that it is the busiest time of the year not only for the IRS, but also for bad actors trying to scam their way into people’s tax refunds. According to the BBB, the earlier you file your taxes, the lesser the chances of someone stealing your identity and claiming your tax returns. Unfortunately, a high percentage of everyone filing leave it for the last moment -- which will be July 15 this year -- and these are precisely the people scammers are targeting.
During tax season, many Americans wait on hefty refunds from the government. According to a survey done by NerdWallet, more than two out of five people said they prefer to overpay their taxes and get a refund. When scaled up to a national level, this means that the IRS is currently issuing refunds to staggering 80 million people. With major data leaks observed over the previous years, we’ve seen that scammers can quickly complete the puzzle of a person’s identity and get access to their cash. So, what are the top tax scams going on at the moment?

Remote 2.0: Virtually closing the gap in IT training and sales
Nothing will entirely replace meeting face-to-face, particularly when it comes to IT training and sales. After all, you’re dealing with complex solutions in precise applications. That requires seeing a product in action, demonstrated in real-world scenarios and hands-on test drives.
With the arrival of COVID-19, in-person meetings, events, user groups and training sessions ground to a halt, impacting IT education and sales. While other industries immediately sought to move employees onto basic conferencing platforms like Zoom or WebEx, those in tech had more sophisticated needs, closer to remote 2.0 in comparison. Foremost, training and sales teams have to effectively deliver user and prospect experiences that can transcend today’s physical limitations, turn heads and improve the bottom line. The following are some areas to focus on to elevate your game and bridge the in-person/virtual gap.

Remote operation changes the working day
The shift to working from home has had a major impact on people's lives, but one of the unexpected effects is how it has changed the working day.
New research from digital experience management company Aternity shows that in the Northeast and West regions of the US the working day starts and ends between 30 and 60 minutes later for remote workers compared to those in offices.

macOS Image Capture bug can fill up hard drives with empty data
A bug has been discovered in the Image Capture app that's part of macOS. The app is used to import photos and videos from other devices.
The bug kicks in when importing images from an iPhone or iPad, and it can result in a hard drive being filled up with empty data.

TEAMGROUP puts RGB lighting into a USB flash drive -- because why not?
RGB makes everything better, right? Keyboards, mice, RAM, and more — all are improved by the beautiful lighting effects. As far as I’m concerned, RGB lighting should be in everything. Hell, I’d be happy to have an RGB toilet bowl!
And now, RGB fans have yet another product to gush over — a USB flash drive. Yes, TEAMGROUP has managed to cram RGB into a thumb drive, and it is actually more than just cosmetic. Called “T-FORCE SPARK RGB,” the drive’s lighting color changes to tell the user the available storage capacity. For instance, the light will be blue when the drive is less than 81% full. When storage is between 81% and 92%, the color changes to yellow, and when 93% and above, it turns red. Cool, huh?

Bugcrowd seeks to disrupt the pen test market with new service
Traditional penetration testing solutions often fail to provide the rapid, reliable and fully integrated security testing that fits with businesses' go-to-market timelines.
Crowdsourced security company Bugcrowd is looking to change this with the launch of its Classic Pen Test, powered by the Bugcrowd platform and focused on providing customers with on-demand access to methodology-driven pen testing at a fixed price.

Fedora 32 Linux-based operating system available for download with GNOME 3.36
The Fedora operating system may be named after a hat, but I consider it more similar to an old, worn-in, pair of sneakers. It may not be the trendiest or flashiest Linux distro, but it is comfortable as hell. Sure, Manjaro and MX Linux may be what the "cool kids" are using these days, but Fedora remains the reliable Linux distribution that is always there for you -- fast, stable, and focused on open source. An old comfortable shoe.
Today, Fedora 32 becomes available for download. It comes with GNOME 3.36 which you can read more about here. If you don't like GNOME, it isn't the end of the world -- you can instead choose KDE Plasma, Cinnamon, MATE, and more. There is even a special ARM variant of Fedora 32 that will work with Raspberry Pi devices.



