The Internet Archive to set up Canadian mirror to stay out of Trump's reach

Many people are concerned about just what Donald Trump might do when he becomes president in 2017, and some of the biggest concerns lie in the fields of technology and the internet. Worried about what the arrival of President Trump could mean, the Internet Archive is collecting donations to fund a Canadian mirror of the site.
The Internet Archive of Canada will lie outside of the jurisdiction of the US government and is being built based on the idea that "lots of copies keep stuff safe". Currently based in San Francisco, a blog post by the Internet Archive makes reference to fears about greater online restrictions that could be put in place by the US.
The Church Committee calls on Obama for leniency for Snowden if not a pardon

The calls for Edward Snowden to be pardoned by President Obama before Donald Trump takes office have been getting louder. But while many would like to see him given a get-out-of-jail-free card, there is a growing recognition that this simply might not happen.
The latest call in support of Snowden comes from the Church Committee (nothing to do with the church, rather the United States Senate Select Committee to Study Governmental Operations with Respect to Intelligence Activities, responsible for investigating illegal CIA activity in the 1970s). In a letter to the out-going president, 15 former members of the committee say that while it is open to debate whether Snowden's actions "merit a pardon, they surely do counsel for leniency".
Automatically map the network drives you need with Network Drive Control

Set up your own home network and you can have Explorer automatically map any remote drives you like, whenever you log on. Connect to another network, though, and Explorer will still try to connect to the drives that aren’t there, along with drives for work, school, or whatever else you might have set up.
Network Drive Control can help by checking a network as you log on, and only mapping the drives you need for that environment.
Deutsche Telekom hack affects 900,000 customers

German telecommunications giant and T-Mobile parent company Deutsche Telekom was the victim of a cyber-attack over the weekend, which left some 900,000 users affected, the company confirms in a blog post.
This weekend, a hacker (or more likely, hackers) infiltrated the company, and tried to infect users' home routers with malware. Deutsche Telekom said its network was not affected "at any time".
It is terrifyingly easy to bypass BitLocker in Windows 10

The BitLocker feature of Windows is supposed to offer a degree of peace of mind that files are going to be secure -- but one expert points out that a simple key combo is all it takes to bypass the security feature.
A bug has been discovered in the way Windows 10 handles a Feature Update -- the installation of a new build of the operating system. By taking advantage of the bug, it is possible to access a Command Prompt and gain unrestricted access to the contents of the hard drive.
Apple will not approve updates and new apps during winter holidays
The winter holidays are fast approaching and, just like other workers, many folks in the tech industry are looking forward to their vacation days. But, before employees can celebrate and unwind, companies have to adjust their schedule accordingly and prepare their customers for the limited (or lack of) office hours.
Apple announces its schedule today, advising developers to submit their updates and new apps for approval in time, to avoid any delays and inconveniences.
The cloud can be a driving force for your startup

Amazon Web Services (AWS) turned ten earlier this year and posted some pretty impressive figures to go with it (which have continued to impress in subsequent quarters). The public cloud provider revealed it is on course to generate more than $10bn in 2016, which highlights the success of the public cloud.
Organizations from all over the world are tapping into this success, but could it also be the driving force behind successful start-ups? If so, what can enterprises learn from start-ups flourishing in the cloud?
Google successfully uses machine learning to detect diabetic retinopathy

Diabetes is a hell of a disease. While many people view it as nothing more than the inability to eat sweets, it is actually much more devastating than just that. If untreated, having high glucose levels can wreak havoc on a patient's body -- these folks can go blind, have limbs amputated, or worst of all, die.
Diabetic eye disease is caused by retinopathy. Affected diabetics can have small tears inside the eye, causing bleeding. Over time, they can lose vision, and ultimately, they can go blind. Luckily, Google has been trying to use machine learning to detect diabetic retinopathy. Guess what? The search giant has seen much success. Not only are the computers able to detect the disease at the same level as ophthalmologists, but Google is actually slightly better!
Mitigating the risks of third-party access to your data

If your office was broken into, you would fear what the intruders might take. Being so concerned about the possibility, you fit all the right locks and alarms and have good door and window security. However, do all the service providers that access your office do the same? If they’re not as security conscious, and they get broken into, the intruders could get hold of the access card or key to your office and then they’re in.
It would be galling because, despite having done all the right things to protect your company’s assets, your defenses were still breached. There was a weakness but it wasn’t your security. You gave a vendor the means to access your business to do you a service, and that access was exploited by someone with the skills to take advantage of their weak security.
You can now play classic arcade games in Facebook Messenger -- Here's how

You’ve been able to play basic games in Facebook Messenger for a while -- things like chess, soccer and basketball -- but from now you’ll be able to play classic arcade games too.
So, if in a middle of a chat with a friend you’re suddenly overcome with the need to challenge them to a game of Pac-Man, Galaga, Space Invaders, Puzzle Bobble, or Track & Field, you can.
The Snooper's Charter is now law, giving the UK some of the most extensive, invasive and draconian web surveillance powers in the world

The Investigatory Powers Act 2016, the Snooper's Charter, legalized spying: call it what you will, the UK now officially has some of the most extreme internet surveillance powers in the world. The Investigatory Powers Bill was today given royal assent, meaning it has now passed into law.
Unsurprisingly, there have been huge protests from privacy groups, and an online petition against the new powers has already gained more than 136,000 signatures. The Investigatory Powers Act 2016 not only requires ISPs to store records of their customers' browsing history, but also make this data available to dozens of government agencies, and even permits state hacking of phones and computers.
Plagued by Apple Calendar spam? Here's how to stop it
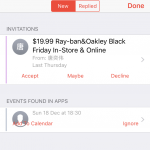
Recently a lot of people have been complaining about spam calendar invitations in iOS, and it’s something I’ve experienced too -- particularly on Black Friday. "$19.99 Ray-ban&Oakley Black Friday In-Store & Online" said one unwelcome invitation.
While you can easily decline these invites, that’s not the greatest idea because -- just like responding to a spam email -- it has the side effect of telling a spammer that your account is active. Thankfully, there is an easy way to stop them.
Digital transformation is top strategic priority for half of execs

Digital transformation is at the top of the strategic agenda for enterprises, and half of executives surveyed believe the next two years will be critical for their organizations.
These are among the findings of a new report by Forbes Insights, in association with Hitachi Data Systems, which surveyed 573 senior executives worldwide as well as holding one-on-one conversations with top executives.
Sophisticated social engineering attacks target hotel chains

In the run up to one of the hospitality industry's busiest periods, cyber criminals are targeting hotel chains with a series of targeted attacks.
Cyber security company Trustwave has investigated the attacks, which combine social engineering with sophisticated malware, against a number of its clients in the past month.
TeamViewer 12 brings up to 20x file transfer speeds

TeamViewer has just released TeamViewer 12, the latest edition of its popular remote control package. Major performance improvements include up to 20x faster file transfers, and frame rates of up to 60 fps.
Connection settings can automatically adapt to network connections, giving you the best possible quality at all times.
Most Commented Stories
© 1998-2024 BetaNews, Inc. All Rights Reserved. Privacy Policy - Cookie Policy.