
New endpoint protection platform aims to stop targeted attacks
Increasingly attacks against businesses and government organizations are targeted against a specific entity.
The latest platform from endpoint protection specialist Endgame uses enhanced attack mapping and automated guidance to empower users of any skill level to stop even the most aggressive attacks.

SJCAM SJ6 Legend action camera review
Of all the action cameras that I have used, the SJCAM SJ5000X Elite is probably the one I liked the most. The video quality was top-notch, it was well made and it also got lots of updates. The SJ6 Legend has replaced it, but does it live up to its predecessor?
The new action camera is similar in terms of specs, but thanks to some key changes it makes for a much more interesting proposition. But how does it perform? I've tested the SJ6 Legend to find out.

More than seven billion records exposed in 2017 data breaches
The first three quarters of 2017 have seen 3,833 breaches reported, exposing over seven billion records, according to a new report.
But the study by Risk Based Security reveals that 78.5 percent of all records exposed came from just five breaches. Compared to the same period in 2016, the number of reported breaches is up 18.2 percent and the number of exposed records is up 305 percent.

Twitter lets everyone send 280-character tweets -- and infuriates with maddening circle icon
After a few weeks of testing with a limited number of users, Twitter is rolling out 280-character tweets to (nearly) everyone -- but says that very few of the testers reached this limit.
With the 140-character limit, says Twitter, just 9 percent of tweets hit the upper limit; with 280 characters to play with, this drops to 1 percent. The increase has divided opinion on Twitter, but the company's decision to replace the simple character countdown -- to warn how much more you could type -- with a bizarre circular icon has been given a rather negative reception.

Opera 49 adds editable elements to its screen capture tool, rolls out VR headset support
Opera Software has unveiled Opera 49, the latest version of its Chromium-powered browser for Windows, Mac and Linux.
Opera 49’s headline new feature is a major update to its new snapshot tool, with editing features, a selfie mode and support for emoji. Elsewhere, the VR headset support previewed in the Developer release has also been included, along with a new 'easy setup' button offering convenient access to key settings.

Ubiquiti Labs unveils VPN-like AmpliFi Teleport to bypass location restrictions with Netflix, Hulu, and more
Ubiquiti Networks is a very respected company in the networking market. Its high-end hardware is used by many in the enterprise. Under its "Ubiquiti Labs" branding, however, the company recently entered the home consumer space with the "AmpliFi" mesh wireless router system. That product is exceptional -- my current recommended home router for anyone that will listen. It gets plenty of timely updates, looks beautiful, and offers both wonderful speed and coverage. Seriously, folks, it rocks.
Today, Ubiquiti Labs unveils its next home consumer product. Called "AmpliFi Teleport," it is a little box that promises to route your on-the-go internet traffic through your home router. The device plugs into the wall for power and connects to an access point using Wi-Fi or Ethernet. It creates an encrypted connection, making it operate sort of like a VPN, but that's not all. Your media services (Netflix, Hulu, MLB, etc.) will think you are at home when you aren't, so you can still access location restricted content. In other words, you won't get the dreaded message of "sorry, this is not available in your area," even if you are in a different state -- or country. It supplies access to the things connected to your home network too, such as smart devices that don't offer remote access.

SteelSeries launches 'Arctis 3 Bluetooth' gaming headset with simultaneous wired and wireless audio
Wireless headsets are my favorite, although wired variants are my favorite too. Is that sentence nonsensical and devoid of logic? Not really, but sort of. All kidding aside, it is totally possible that someone can prefer using a cable in one scenario, while opting to go wire-free in another. Case in point, when I am at home on my gaming PC, I prefer a wired headset. Why? Because I am sitting in a chair in front of a monitor -- having to charge a headset in that case is silly. When I am in my living room or on the go, however, being wireless has its perks -- no cables to get tangled or trip over.
Having a headset that can operate as both wired and wireless is nothing new, but today, SteelSeries unveils a new product that takes this idea to another level. The "Arctis 3 Bluetooth," as the headset is called, can process audio over both Bluetooth and hardwired connections simultaneously. I know what you are thinking -- why would you want that? On the surface, it seems crazy, but once you think about it, the concept is very smart. Best of all, it is based on the already well-received Arctis 3 wired headset.

The myth of cloud insecurity
It’s not exactly clear when the term "cloud" was first used to describe shared pools for configurable IT resources. However, it’s safe to say that it started creeping into our lexicon less than ten years ago.
Back then, the official definition of cloud was even less clear than it is today. Regardless of what the cloud actually was, this mysterious cloud entity was widely assumed to be unsafe.

Home tech gifts: Which products are topping consumer wish lists?
Our ongoing obsession with electronics shows no sign of cooling off, but consumers are showing an increased interest in connected devices, according to CES trends, market research from Parks Associates, and Amazon Wish List rankings. While gaming and mobile devices continue to be favorite gift items, many consumers are just beginning to embrace the idea of a smart home. As they do, smart and connected products are seeing a rise in popularity. Some consumers shop independently for smart products, while others seek to purchase easy-bundled solutions from home security companies and ISPs.
As consumers are creating wish lists for housewarming presents, wedding gifts, and holiday surprises, here are some items that are emerging as trends this season.

A guide for mastering endpoint management
Unified Endpoint Management (UEM) has emerged over the last couple of years as a new approach to help IT teams better manage a growing number of devices in an increasingly distributed work environment, by uniting traditional endpoint management and mobile device management (MDM). Yet successfully integrating the two commonly disparate approaches is easier said than done. In fact, many teams find themselves overwhelmed by the thought of figuring out where to even begin marrying both approaches, resulting in continued separate workflows and lingering inefficiencies.
For the modern enterprise looking to maintain both its security posture and digital relevancy, however, the impact of resisting UEM extends well beyond a missed opportunity for IT workflow optimization. By not deploying an effective UEM strategy, an organization is missing a critical step to comprehensively and uniformly securing its entire IT environment -- which includes an ever-growing web of network connected devices, including desktop computers, laptops, smartphones and tablets, as well as printers, projectors, BYOD devices, gateways and Internet of Things devices -- all of which are essential to employees’ daily work and, ultimately, business continuity and growth. For organizations looking to unite endpoint management and MDM workflows to optimize efficiency, security and digital enablement UEM has to offer, here are some key tips to keep in mind.

9th anniversary of Bitcoin: Is the war between cryptocurrencies and governments over?
The global real estate market is worth $217 trillion, and one-third of income-generating real estate transactions are cross-border. But cross-border real estate transactions are notoriously complicated and rife with delays and impediments inherent to antiquated property rights registrations systems. However, an American’s purchase of $60,000 apartment in Kiev may change everything.
In September, TechCrunch founder Michael Arrington remotely purchased a $60,000 apartment in Kiev in a deal that will change real estate forever.

Ethereum wallet vulnerability freezes hundreds of millions of dollars
Ethereum is a hugely promising blockchain technology which has really taken off this year, thanks in no small part to the backing of major companies like Microsoft, Intel and Cisco. It is also super valuable as a cryptocurrency, being worth around $28 billion, and a great platform for ICOs (Initial Coin Offerings).
So, many startups are now turning to Ethereum to raise money, and the way that they are doing it is through smart contracts. Only problem is, they are not bullet-proof, as a newly-uncovered vulnerability in a popular wallet puts hundreds of millions of dollars at risk.

Amazon makes Fire TV Stick available in over 100 countries
Not long after releasing the original Amazon Fire TV as a small set-top box, Amazon shrunk its player down into stick form. It's a small dongle that plugs directly into an HDMI port on your TV or monitor, or even an HDMI switch if you'd like to easily move between sources.
Now the retail giant is opening up the market for the Fire TV Stick to people around the globe, bringing entertainment to everyone.
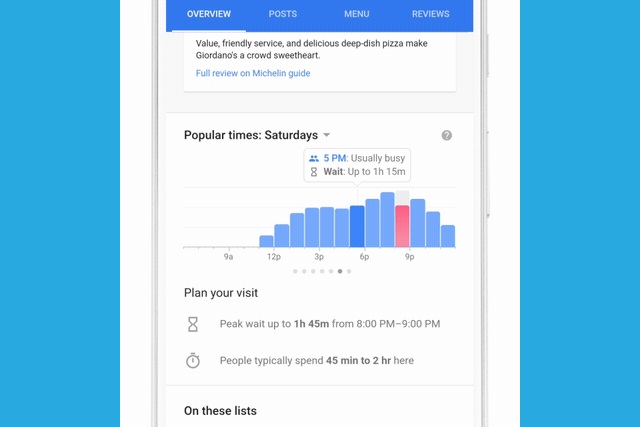
Google adds restaurant wait times to Search and Maps
Search for a restaurant using Google, and you're already told the times of day at which a particular place is busiest. But Google is about to make this information even more useful.
The fact that a restaurant is busy at 3PM on a Thursday afternoon doesn't necessarily mean you'll have to wait ages for service -- there may be more staff working, for instance. A new update to Google Search -- and Maps is to follow -- means you'll be able to see estimated wait times as well.

Public cloud and SaaS monitoring added to security operations platform
The use of SaaS applications and cloud infrastructure is becoming more widespread, but robust cyber security operations policies are often lacking for these environments.
The proliferation of these services has blurred the traditional security perimeter of the enterprise, creating a growing need to unify the security and operational policies of on-premises, SaaS and public cloud infrastructure to ensure visibility into systems and data.
