
Windows 10 set to be the most widely installed version of Windows ever
Windows 10’s growth might have slowed quite dramatically in recent months, but never underestimate the power of free.
According to the latest prediction from Gartner, the new operating system is set to enjoy not only the fastest growth of any version of Windows, but is poised to become the most widely installed Microsoft OS ever, quickly overtaking both XP and Windows 7.
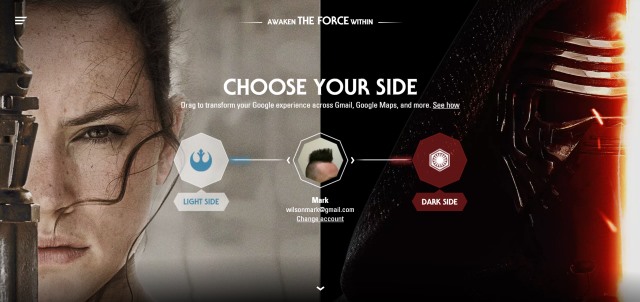
Awaken the Force! Choose the light side or dark to give Google a Star Wars makeover
Even if you're not a fan, it can't have escaped your attention that there's a new Star Wars movie coming out soon. Google is as excited as millions of fans are, and to celebrate Star Wars: Episode VII The Force Awakens it is giving you the chance to give Google apps and services a Star Wars makeover.
Choose to join the light side or the dark side, and Gmail, Google search, and more will be customized in a Star Wars style. Like the idea of being shown how to get to your destination by an X-Wing flying down the streets in Google Maps? Consider it done! But there's a lot more to look out for...

Is your website ready for Black Friday traffic?
Conventional wisdom has dictated for millennia that planning well in advance will put you in good stead for success. What this means for IT departments is to prepare for the worst -- and for online retailers that means November 27 and 30.
Black Friday and Cyber Monday are approaching fast and now is the time for IT professionals to ensure their IT infrastructure capacity will not leave them sitting on the side-lines.

Dear Satya Nadella, the pitiful Lumia 950 signals Microsoft should give up on mobile
Hey, Satya Nadella, you are doing a pretty good job at Microsoft. Windows 10 is a darn good desktop operating system, although you need to work on those confusing privacy settings, bro. Office 2016 is great too, as always, and your cross platform apps are wonderful. Hell, even Bing continues to get better.
We need to have a heart to heart about Windows 10 Mobile, otherwise known as the continuing of Windows Phone, though. Here's the thing -- nobody wants it. Other than some Microsoft fanboys and beat-writers like Paul Thurrott and Mary Jo Foley, it's about as wanted as diarrhea. Yes, Satya, I am comparing your mobile operating system to loose stools. While that sounds a bit extreme, it sadly actually isn't. It's time to give up on mobile. Free your fanboys from their mental prisons.

Toshiba Q300 480GB SATA SSD [Review]
If you are still running your operating system from a traditional hard drive, I want you to slap yourself in the face. Why? You are doing your computing wrong. Sure, a mechanical hard drive is great for storage, but your OS will absolutely fly with a solid state drive. While they used to be expensive, the prices have dropped so dramatically in recent years, there is no excuse not to upgrade. It has become a cliché, but an SSD is the best upgrade you can make.
Recently, I have been testing the Toshiba Q300 SSD. The particular model I have been using is 480GB. Keep in mind, capacity can impact performance, so your mileage may vary based on the size you pick. This is a SATA variant, so performance won't be mind-blowing, but with that said, SATA will remain the most-used connection type for the near future, and for folks upgrading older machines. Is the Q300 a smart choice?

Microsoft pulls the Windows 10 November Update [Updated]
Here’s an interesting story for the weekend -- it seems as if Microsoft has pulled the recently released November Update (aka Threshold 2) from both the Media Creation Tool and Windows Update.
That means if you don’t currently have the update on your Windows 10 device, you won’t be able to download it directly now.

Earn yourself spendable Bitwalking dollars with your daily perambulations
Ordinarily, if you want to receive money just for walking you'd need to do a sponsored walk -- and that money's supposed to go to charity -- or get yourself a job as a dog walker. But how does the idea of getting paid just for the walking you do each and every day sound? That's exactly what Bitwalking promises.
With a name clearly inspired by the Bitcoin cryptocurrency, Bitwalking works in a couple of ways. Walkers can earn 1 Bitwalking dollar (BW$) for every 10,000 steps they take, and these can be spent in an online store, or converted into cash. The system uses a smartphone to count steps, but there are also plans to produce a wristband.

Apple video explains how to use Apple Pay to pay for things... like apples
There's quite a lot of competition in the digital payment arena at the moment. Apple Pay is one of the latest to join the likes of Samsung Pay and Android Pay, and Apple is keen to demonstrate just how easy it is to use its payment system.
For many people, using a smartphone to pay for coffee is an intuitive process, but Apple wants to sell its service to more people. The company needs to break down any barriers that might be standing in the way of new users adopting Apple Pay, and this is the reason for the appearance of a video that serves as a 'how to' guide.

Microsoft shoots itself in the foot using AppComparison to lure Android users to Windows 10 Mobile
After the slightly disappointing launch of Windows 10 -- at least in terms of reception, if not in terms of numbers (well, it was free) -- Microsoft is now switching its focus to Windows 10 Mobile. The aim now is to try to capture Android and iPhone users, convincing them that a Windows-based smartphone is a smart move.
But there's the problem of apps. It's something that crops up time and time again. Microsoft simply doesn't have the support of mobile developers in the same way that other platforms do. Not that Microsoft would admit this of course. To try to convince people that the 'app gap' no longer exists, the company has released AppComparison for Android to show off how many of the apps you use are available for Windows 10 Mobile. The problem is, there are still lots that simply don't exist.

Samsung lays out its IoT SmartThings devices in new infographic
The Internet of Things, or IoT, is the latest rage with more products coming onto the market all the time. It's also become a bit of a target for hacking, though the problem is likely a bit exaggerated. We've recently looked at one of the newest offerings on the market from startup MivaTek, many other players are on the field and one of those is Samsung.
Samsung now has a line it calls SmartThings and it includes an array of products such as outlets, water sensors, security and much more.

Is Yahoo locking you out of your email account for using an ad blocker?
Yahoo has sparked controversy by preventing some users from accessing their email accounts if they have an ad blocker installed. It's something that seems to be restricted to the US at the moment, and Yahoo says it is testing out the block on a "small number of Yahoo Mail users".
Edward Snowden recently said that people have a duty to use an ad blocker, and it seems that nearly 20 percent of web users have followed his advice. Just like Google, Yahoo makes a large proportion of its income through advertising, but affected Yahoo Mail users feel that the company is holding their email accounts to ransom.

Speed up Windows 10 boot up with this simple tweak
Because I have a super-fast PC with a large SSD as the system drive, Windows 10 boots up really quickly for me. The days of waiting 5 minutes or so for Windows to get to a usable state -- as was sometimes the case in the past -- are long gone, thankfully.
But if you find Windows 10 is taking too long to boot up for you, there’s a setting you can apply which can speed things up significantly. Even if you have no complaints with how quickly Windows 10 loads, it’s still worth applying this (if it isn't on already) because it will make a difference.

Banking trojan Dyreza goes after Windows 10, Microsoft Edge users
The Dyreza banking trojan has (unfortunately) been updated, and now can target users sporting Windows 10 and its internet browser, Microsoft Edge.
The new version of the banking trojan was spotted and analyzed by EU-based security firm Heimdal Security, which claims that Dyreza will now also seek and find security products, terminating their underlying OS processes.

Get amazing music, games, movies, and apps for only ten cents each on Windows 10
Windows 10 is arguably a success. True, not everyone loves it, but many -- according to Microsoft -- have downloaded it. A huge benefit of having large adoption of the latest version of Microsoft's operating system, is that more people have access to the Windows Store. As a result, more and more quality apps, games, and other content should be made available in it.
To celebrate Windows 10, Microsoft is doing something incredible for its fans. Over the next ten days, the company will be selling music, games, movies, and apps for ten cents each. Yes, for a single dime, you can score some awesome stuff. Heck, you can't get much for such a little amount, nowadays.

Windows 10's privacy invading features aren't gone in Threshold 2
Since the launch of Windows 10, there have been various concerns relating to privacy. Some would dismiss this as little more than paranoia, but a lack of transparency about what was happening in the background broke a lot of people's trust. Many hoped that the release of the Threshold 2 update this month would address this, but in lots of cases it was actually a backward step.
In the RTM release of Windows 10, there was a service running in the background called Diagnostics Tracking Service (also known as DiagTrack), and people concerned about privacy -- who were in the know -- disabled it. In Threshold 2, this service is gone. A cause for celebration you might think; but think again. The service is still there, just under a different guise.
