
Glorious unveils GMMK Numpad
I absolutely hate keyboards with number pads. Why? Because I do not use the number pad -- I use the numbers on the top row of the keyboard. And so, having a number pad on my keyboard is simply wasteful. It causes the keyboard to be wider than necessary, taking up extra space on my desk. This is why I prefer tenkeyless keyboards.
Understandably, some people do prefer having a number pad. Wouldn't it be cool if number pads were simply always offered as a separate accessory? While dedicated number pads have been around for years, a new such gaming-focused product from Glorious might be the coolest ever. Called "GMMK Numpad," this macro pad connects via Bluetooth, but it can charge and connect using USB-C too. The mechanical pad even features a knob and slider. Best of all, it can be extensively configured by the user.

Why are enterprises overspending on the cloud?
Cloud services have grown exponentially in recent years, with businesses embracing the solutions to provide scalability, agility, and access to new applications. Most organizations have already embraced the cloud or are planning to do so -- and the increased movement of infrastructure to the cloud is described as “inevitable” by 95 percent of enterprises polled recently.
Despite this momentum, enterprises are growing frustrated with some limitations of cloud services and are starting to wonder if more can be achieved. Cloud is not always meeting businesses’ expectations, with inadequate management tools, issues with accessing data, and inflexible pricing plans often resulting in dissatisfied customers.

GitHub rival GitLab ditches plans to delete inactive repositories
GitLab recently announced plans that meant repositories that were part of its free tier would be erased after a year of inactivity. This led to complaints from users of the GitHub rival, saying that it was unfair and that the decision made no sense.
Having listened to the negative feedback, GitLab has now announced a change of heart. Inactive repositories will no longer be deleted when they have not been active for a while, but there will still be consequences for inactivity.

DuckDuckGo to block Microsoft tracking scripts after user uproar about recent revelations
DuckDuckGo likes to bill itself as a privacy-centric search engine and web browser, and it is hard to deny that it is more private than the likes of Google search and Chrome. But earlier this year, it came to light that there was an agreement in place between the company and Microsoft that meant the DuckDuckGo browser did not block all trackers from the maker of Windows 11.
When users learned that DuckDuckGo was granting a level of leniency to Microsoft there was an understandable backlash. Now the company has announced it is to offer "more privacy and transparency" after failing to meet users expectations, and will block Microsoft tracks -- most of the time.

Amazon sucks up Roomba for $1.7 billion
There are plenty of robot vacuum cleaners available to buy these days, but the best-known brand remains Roomba. I was lucky enough to test and review the first generation model Roomba vacuum cleaner in 2002 and I've been a big fan ever since.
Today, retail giant Amazon announces that it has entered into a definitive merger agreement to acquire Roomba creator iRobot. What will this mean for fans of its products?

Hybrid work needs to move on from pandemic-era tech
When the pandemic-inspired lockdowns hit in 2020, businesses rushed to established technologies like VPNs in order to support remote working.
But new research conducted by Gartner Peer Insights for Citrix Systems shows 96 percent of IT leaders think these technologies no longer cut it and are rethinking their approach.

Log4j and why it's not safe to relax yet [Q&A]
The Log4j vulnerability first hit the headlines in December last year. Since then we've heard less about it, but it hasn't gone away, like most vulnerabilities it has a long tail.
A recent report from the Cybersecurity Safety Review Board takes a comprehensive look at the vulnerability and what can be learned from it.
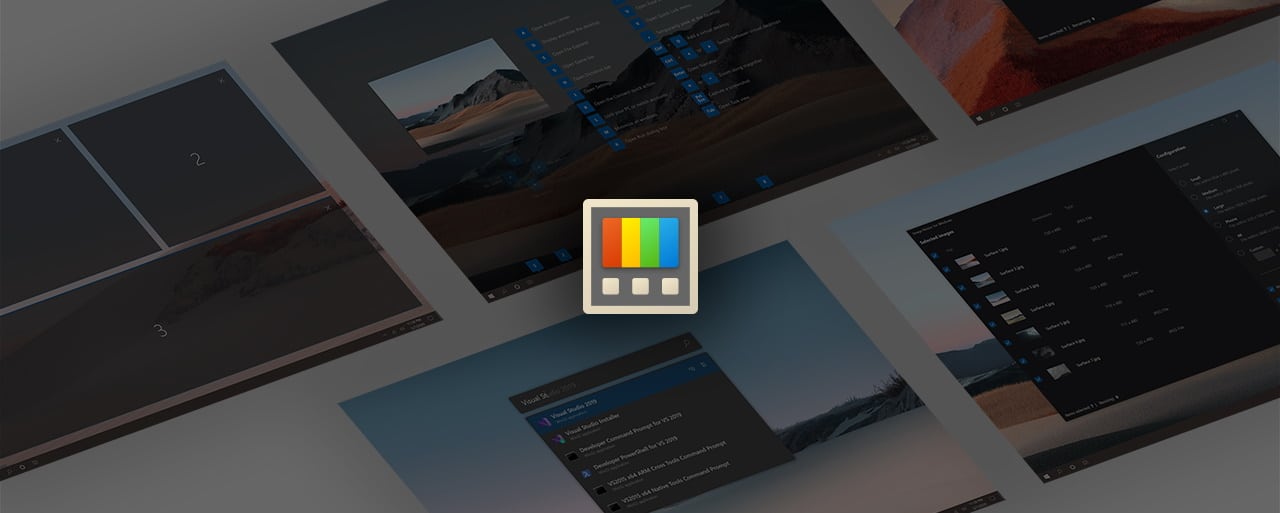
Microsoft launches PowerToys v0.61.1 as an important stability-fixing update
It is only a few days since Microsoft unleashed PowerToys v0.61.0 , bringing a slew of "quality of life improvements" to the much-loved collection of utilities. Now the company has released version 0.61.1 which will be of particular interest to Windows 11 users.
Despite lacking new features per se, PowerToys v0.61.1 remains an important release because of the issues that it addresses. Users might be longing for new features, but this development cycle is about improving what's already in place before more is added.

ADATA ACE 6400 DDR5 Limited Edition RAM is the cutest computer memory ever
Can computer memory be cute? No, seriously. Can it be? While it is easy to say no to that question -- I would have said no just yesterday -- some new RAM from ADATA has turned my world upside down. You see, we now actually live in a world where cute memory exists. Seriously.
Today, ADATA launches some new DDR5 memory called ACE 6400, and while it looks like nice RAM from a specifications perspective, it is also a bit plain and boring aesthetically. The memory features a generic silver-colored heat spreader. What is truly exciting, however, is the Limited Edition variant of the RAM as it features a super-cute design. As you can see, its heat spreader is adorned with friggin' colorful flowers. Heck, even the packaging is cute!

New Ubuntu Linux version tragically delayed by serious bug
Canonical is usually quite dependable when it comes to Ubuntu releases. When a new version of the Linux-based operating system is expected, it usually becomes available on time.
Sadly, Ubuntu 22.04.1 won't become available today as expected -- a huge gut-punch to the Linux community. Why is Canonical disappointing fans of the operating system? Well, it seems a serious bug has caused the tragic delay. This serious issue causes snaps not to run on computers that use the OEM install option.

Small businesses often left hanging by ransomware scourge
Ransomware is hitting small businesses hard. But most of the legislation, regulations, and headlines focus on large businesses. The math is simple -- large businesses impact many end-users, and they have lots of money to pay lobbyists, so they wind up stealing the show when it comes to ransomware. But what about the local print shop, deli, or accounting office? Even though small businesses are suffering from ransomware 70 percent more often than large businesses (according to the Cyber Edge 2022 Cyberthreat Report), government regulations haven’t changed to accommodate them.
The U.S. Justice Department recently released a strategic plan that will investigate 65 percent of all reported ransomware attacks by 2023, but there are a few problems with this. First, the Justice Department -- or anyone else for that matter -- has no accurate accounting of how many attacks are actually occurring. Because so many attacks go unreported, there isn’t a way to certify how many ransomware attacks happen each year. Second, even if we assign credibility to 65 percent of ransomware cases, how can we or the government use this information effectively to reduce attacks? Finally, what about unreported ransomware attacks (which account for most of the attacks) on 44 percent of the U.S.’s economy: small businesses?

Four ways IT leaders can disrupt public safety with new tech
Most industries, from education to manufacturing, are inundated with technical solutions. But there's one space you'd be surprised is still firmly in the 20th century: public safety. That's right, your cops and EMTs are running software that was cutting edge in the early 2000s. This means a few things for the IT industry.
First, it means these groups are facing a massive and necessary upgrade cycle. That translates into a significant opportunity for those interested in the first responder market.

The cyber threats and trends that will dominate going into 2023
It might still be a bit early to begin thinking about next year, but new research from Intel 471 analyzes recent and commonly used tactics, techniques and procedures (TTPs) that have been adopted by prominent threat actors.
It also looks at how these threats have affected enterprises, along with predictive intelligence assessments on threats that organizations should be prepared to thwart over the next year.

84 percent of companies have only basic cloud security capability
A large majority of companies are only at an entry level in terms of their cloud security capabilities according to a new study.
The research, carried out for cloud infrastructure security company Ermetic by Osterman Research, surveyed 326 organizations in North America with 500 or more employees and who spend a minimum of $1 million or more each year on cloud infrastructure.

Enterprise integration is key to business but few have a strategy
Most business leaders (57 percent) believe an enterprise integration strategy is critical to their organization, while 61 percent of CIOs and more than half of system architects and developers said a standardized, enterprise integration strategy is a top priority.
However, only seven percent of respondents have succeeded in implementing an enterprise integration strategy, according to a new study from Digibee, while 93 percent of decision-makers admit they have no formal integration strategy in place.
