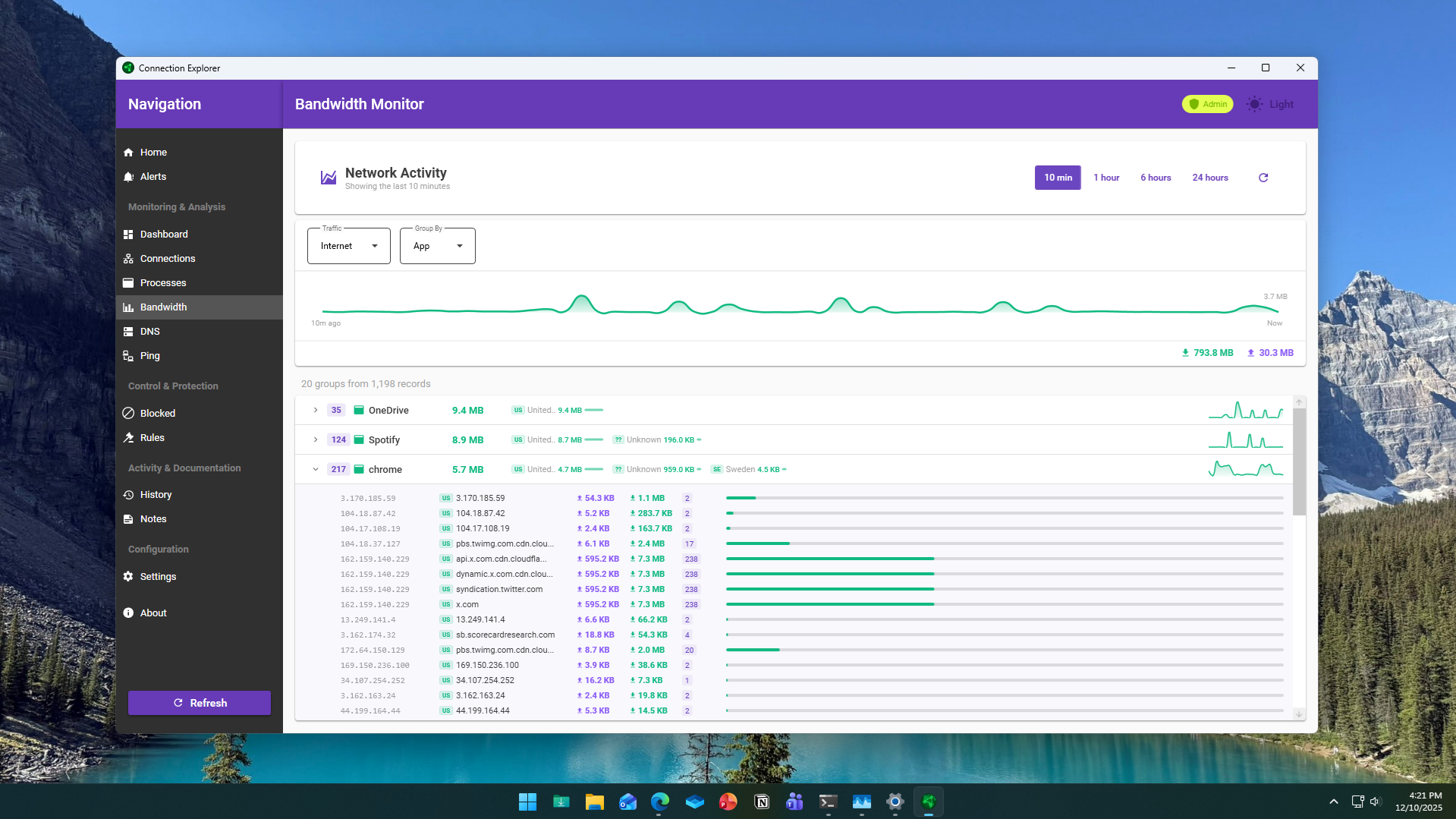
Connection Explorer update adds new ways to see where -- and why -- your PC is sending data
Stardock has released an updated beta of Connection Explorer, the Windows app it first launched a month ago that lets users can see and understand all of the network activity on their PCs. The new update adds additional ways to view bandwidth usage and connection history, giving users a better understanding of where the data is going and -- even more importantly -- why.
Connection Explorer shows every network connection a PC makes in real time and turns background activity into something readable. It allows users to see which apps and processes are communicating online and where those connections terminate.

AI and automation feed rise in holiday scams
The holiday season has long been a peak time for scammers as much as it has for retailers. But new research from Check Point Software reveals how AI and automation are fueling the biggest surge in holiday scams ever recorded.
The study shows over 33,500 Christmas-themed phishing emails flagged in just 14 days and over 10,000 fake social media advertisements being created daily. This is coupled with fake retail sites and social media giveaways surging around the globe.

How to install the new Kodi 21.3 Omega on Amazon Fire TV Stick (the easy way)
Kodi 21.3 Omega has just been released, bringing with it a range of fixes and improvements. It is the first update since January for the hugely popular home theater software, coming ahead of the launch of Kodi 22 Piers, which is expected to arrive early 2026.
For a lot of users, running Kodi on an Amazon Fire TV Stick (or Firestick as it’s better known) is the best way to enjoy the software and everything it has to offer, giving users access to a wide array of streaming services and media libraries.

Kodi 21.3 'Omega' has arrived and you should download it now!
The Kodi Foundation is still hard at work on Kodi 22 'Piers', with a second Alpha release expected soon. The team hasn’t forgotten Kodi 21 users however, and a new build for that branch has just arrived.
Kodi 21.2 'Omega' was released back in January, and now the Kodi Foundation has rolled out a new build, Kodi 21.3, with a raft of changes, fixes and improvements. This is what’s new:

Why silos restrict scale -- and what to do about it [Q&A]
Silos, you might think, are bit of a niche issue. They arise when old practices become entrenched, or when tools are only used by one part of the organization.
But Shannon Mason, chief strategy officer of Tempo Software, argues silos are actually a major roadblock to growth, agility, and strategic alignment. We spoke to her to find out about the hidden cost of silos and the concrete steps teams can take to break them down.

iRobot has filed for bankruptcy
iRobot Corp – perhaps most famous for its Roomba robot vacuum cleaners – has filed for bankruptcy. The company has proposed that control be handed over Shenzhen PICEA Robotics Co, its main Chinese supplier.
The Chapter 11 process comes after iRobot has been under increasing pressure from various tariffs, as well as competition from lower-cost rivals. There should be – at least initially – no disruption to the company’s operations, apps should continue to function as normal, and supplies are not expected to be impacted.
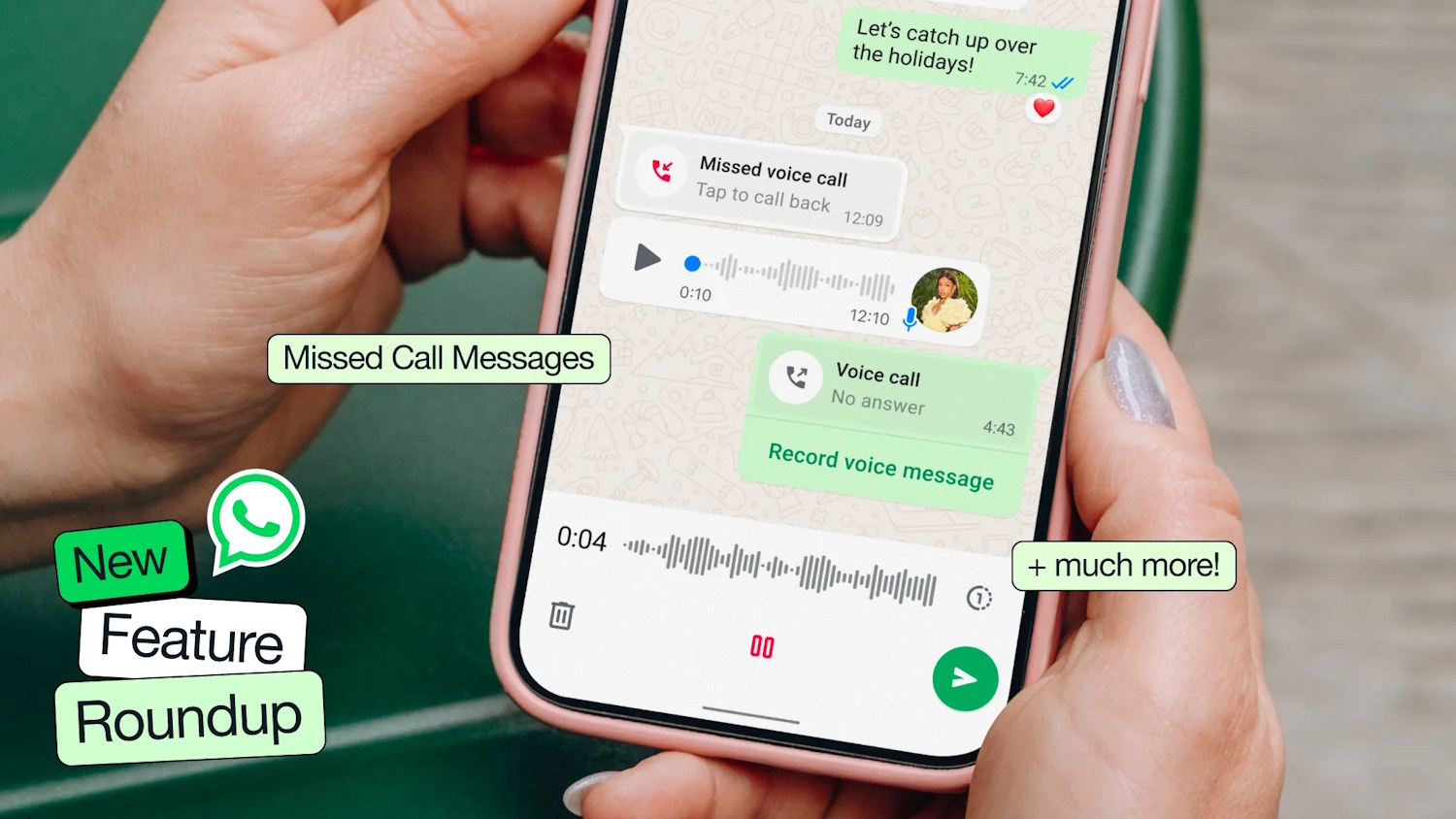
WhatsApp rolls out a sack full of new features for the holiday season
New tools are landing thick and fast in WhatsApp, with Meta announcing, “another bundle of features just in time for the holidays”. There is a lot to explore, but the highlight that is being pushed is the voicemail-like missed calls messages.
There are also changes to voice and video chats, including voice chat reactions and speaker spotlighting in group videos. In addition to genuinely useful updates, there are some additions which are just nice to have – such as new stickers on Status.

Your earbuds can now translate over 70 languages in real time with Gemini AI
Google is expanding the translation features in Search and its Translate app with new systems built on the Gemini AI model. The update introduces improved text translation and a beta version of live speech translation in headphones, giving users clearer and more natural results and bringing the experience closer to a real-world Babel Fish from The Hitchhiker’s Guide to the Galaxy.
The new text translation system uses Gemini 3 to handle idioms, slang, and local expressions with more context awareness. This lets the app produce translations that are closer to natural speech rather than direct word swaps.

Financial sector hit hard by breaches but ransomware seeks targets elsewhere
The banking, financial services and insurance (BFSI) sector has been the most targeted in 2025 accounting for 17.8 percent of all incidents (172 incidents out of 966) tracked in Cyble’s latest North American Threat Landscape Report.
The report describes a mature leak economy where a small cluster of prolific actors generate many listings, supported by a large ‘long tail’ of smaller sellers -- meaning BFSI data can be sourced by both major brokers and many opportunists.

Over a third of US adults now use AI every day
ChatGPT burst onto the scene just three years ago, but a new survey reveals that 34 percent of US adults now use AI platforms daily, and nearly half say they’re using them more than they were a year ago.
The survey, of over 1,000 from US adults, from Tinuiti shows that Gen Z and millennials are leading the AI charge. 67 percent of both groups use AI at least weekly. Platforms like ChatGPT, Google Gemini, Character AI, and Sora are carving out generational niches.

Most companies aren't measuring AI's environmental impact, new report shows
Companies are adopting AI quickly, but most still overlook the energy impact of the systems they use daily. New research suggests this gap is now large enough to affect electricity use in offices, data rooms and commercial buildings. Energy specialists say the problem could be turned into an opportunity -- if firms pay attention to how their AI tools work in practice.
The Thomson Reuters Foundation has published early findings from its AI Company Data Initiative, known as AICDI. The new study examines AI governance disclosures from 1,000 companies in 13 sectors. Built with UNESCO, it is described as the largest dataset that tracks how firms explain and oversee their use of AI.

Huawei's new Mate X7 foldable phone has a slimmer build, upgraded cameras and an improved hinge
Huawei has taken the wraps off its Mate X7 foldable phone at a new "Unfold the Moment" event in Dubai. The new device features a slimmer profile and a hinge system designed for repeated daily use. The Mate X7 comes in a nano fiber woven-style Brocade White finish, with vegan leather versions in Nebula Red and Black also available.
Huawei has made a number of improvements to its camera system, including the addition of new Ultra Lighting HDR Camera, an Ultra-Wide Camera and a Telephoto Macro Camera, as well as second generation True to Color Camera, which promises 43 percent better color accuracy. Video can be recorded at up to 17.5 EV HDR to capture brighter highlights and more shadow detail.

One in 25 digital identity checks flagged as fraudulent
Regulatory tightening across the EU and UK, including the EU’s new anti-money laundering package and platform-economy rules, as well as emerging age-assurance requirements around online safety, have pushed organizations to formalize identity checks at scale.
But identity verification provider Veriff has published its 2026 Identity Fraud Report, showing that 4.18 percent of all digital identity checks processed through its platform in 2025 were flagged as fraudulent – the equivalent of one in every 25 verification attempts across its global dataset.

How self-governing identity infrastructure can streamline policy enforcement [Q&A]
Managing identity is one of the more challenging cybersecurity tasks and can soak up a good deal of time and resources.
We spoke to Raz Rotenberg, co-founder and CEO of Fabrix Security, to discuss the rise of self-governing IAM systems that don’t just enforce policy -- but continuously adapt, reason, and remediate access in real time.

Microsoft massively expands the scope of its bounty program
Microsoft is just one of many technology firms that have a bounty program that offers financial rewards for anyone who discovers security flaws in its products and services. The company has just announced a huge expansion of the scheme so it even covers problems found in third party code.
Vice President of Engineering at Microsoft Security Response Center, Tom Gallagher, announced the broadened scope at Black Hat Europe. He stressed that “keeping our customers secure is our top priority”.
