
Microsoft readies Windows 10 May 2020 Update (20H1) for release
We’re already halfway through April, so it should come as no surprise to you that the next big update for Windows 10, the May 2020 Update, is pretty much finished.
In preparation for its release, Microsoft has begun rolling it out to Insiders on the Release Preview ring for some last minute testing. The software giant believes that Build 19041.207 is the final flight, although that depends on whether Insiders find any major issues.

Samsung Galaxy Tab S6 Lite is a beautiful Android 10 tablet that comes with an S Pen
If you are an iPhone user, and you want a tablet, you should absolutely get an iPad. Why? Because not only do they share the same App Store (meaning you can often buy an app once and have it on both devices), but also, they can be linked so you get text messages and phone calls on the iPad. The problem? Most of the world uses Android smartphones -- not iPhone. Unfortunately, quality Android tablets are becoming increasingly more rare.
Thankfully, some companies are still making Android tablets consumers will actually want, and today, a new one is announced by Samsung. Called "Galaxy Tab S6 Lite," the tablet runs Android 10 and comes with an S Pen included. This device is designed with a focus on media consumption, so it has a big beautiful display and dual AKG-tuned speakers with Dolby Atmos 3D surround sound. It even comes with complimentary access to YouTube Premium for four months.
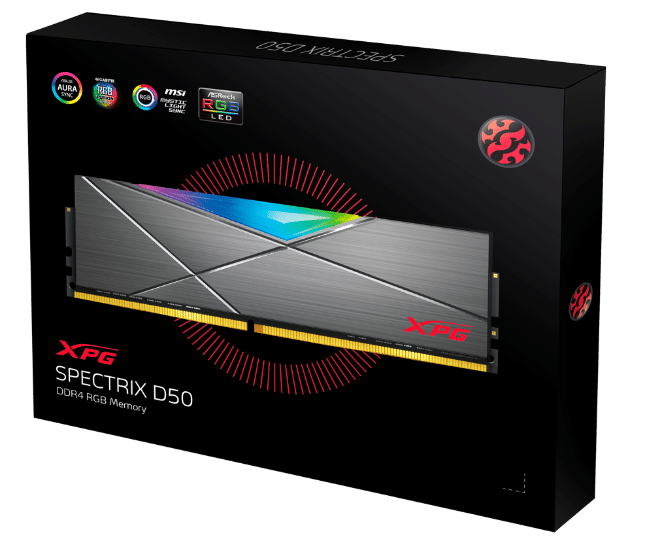
ADATA announces XPG SPECTRIX D50 DDR4 RGB gaming RAM
RGB lighting rules -- it's a fact. It has the ability to make a great product even better. True, some people decry the inclusion of RGB in so many products nowadays, but to them I say, either buy a different product or simply turn the lighting off! You see, many of these products allow you to turn off the lighting effects entirely, so there is really no downside.
Today, ADATA announces its latest memory, and yes, it features RGB lighting! Called "SPECTRIX D50," these DDR4 modules carry the company's XPG branding, meaning they are intended for gaming. With that said, even non-gamers can enjoy the performance and good looks of these sticks.

IT leaders still keen to innovate and invest despite uncertainty
Research into the buying intentions of IT decision makers in the UK has revealed that, despite many organizations (55 percent) putting their buying on hold, 38 percent are still reviewing their digital needs and progressing buying decisions.
The study of 100 top IT decision makers, conducted earlier this month by data-driven consultancy Resonance, finds 67 percent of those actively seeking solutions have increased their urgency to implement them.

Facebook will let you know if you've been reading nonsense about coronavirus
As the world struggles to deal with the coronavirus pandemic, there is another battle taking place online -- the battle against misinformation. Well-aware that its platform is being used to spread false and misleading information about the disease, Facebook is taking action to try to stem the flow.
The social media giant, like other technology companies, has already taken steps to ensure people have access to reliable information, but now it is going further. Facebook will now retroactively alert people who have interacted with "harmful misinformation about COVID-19".

Looking ahead to the cybersecurity challenges of 2022
Just in case you didn't have enough to worry about at the moment, the Information Security Forum has published its Threat Horizon 2022 report, looking ahead to the cyber challenges of the next two years.
Balancing today's realities with forecasts that push the limits of thinking, the report highlights nine major threats, broken down into three themes, that organizations can expect to face as a result of developments in technology.

'Fraud guides' account for almost half of material for sale on dark web markets
Digital risk protection company Terbium Labs has released a trend report on the stolen and fraudulent data of three of the largest multi-good dark web marketplaces, which finds that fraud guides account for 49 percent of the data being sold.
Personal data lags some way behind at at 15.6 percent, followed by non-financial accounts and credentials (12.2 percent), financial accounts and credentials (8.2 percent), fraud tools and templates (eight percent) and payment cards (seven percent).

TikTok bans under-16s from sending and receiving direct messages and introduces new parental control options
TikTok has introduced a raft of new safety measures designed to protect younger users. As well as introducing new options that give parents even more control over their children's account, the company is also implementing a complete ban on direct messaging for those under the age of 16.
The changes are being tenuously linked to the coronavirus pandemic, with TikTok saying that the spread of COVID-19 has accelerated the flow of families moving to the platform for entertainment. The company says that it is adding new parental control features to help ensure a safer experience for users.
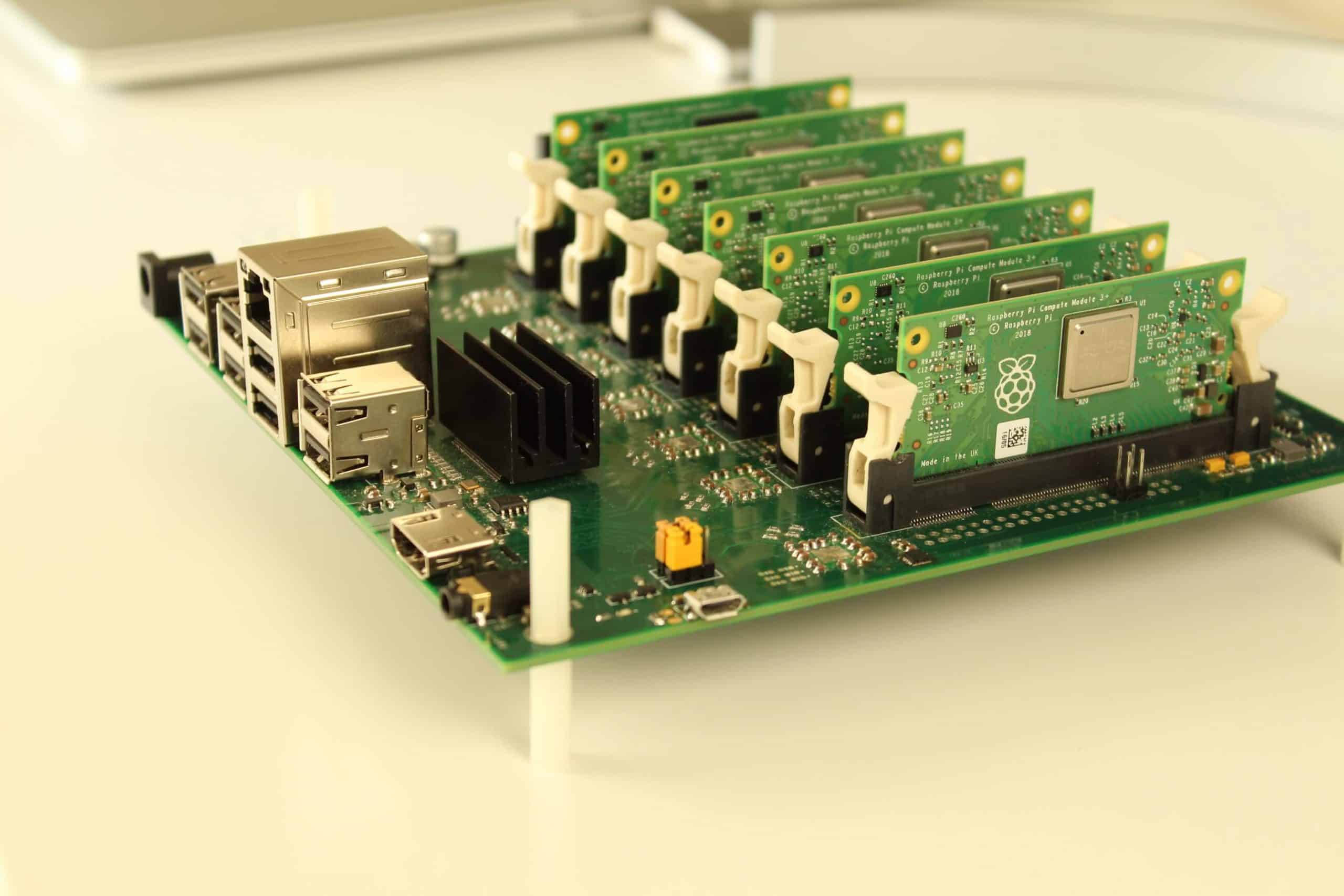
The Raspberry Pi-based server that could transform edge computing
Cloud servers, you might think, are big expensive pieces of kit. But you’d be wrong, at least where the Turing Pi project is concerned.
This mini ITX format board costing under $200 allows seven Raspberry Pi systems to be combined into a desktop Kubernetes cluster that's smaller than a sheet of A4 paper.

Apple thinks the new iPhone SE is worth much less than a quartet of Mac Pro wheels
Apple is not a company readily associated with low prices, and its hardware is always markedly more expensive than something comparable from other companies.
Over the years we've become used to Apple phones, tablets, desktop computers and laptops (typically) being relatively expensive -- but where the company really stands out is with the pricing of its accessories. Take the newly announced iPhone SE, for instance. With a starting price of $399, Apple values the phone less than a set of wheels for a Mac Pro, and only marginally more than a set of feet for the same computer.

New tools help automate container security
Containerization is increasingly popular, but its adoption presents challenges when it comes to vulnerability management and protection.
DevOps security specialist NeuVector is launching new features for its platform aimed at enterprise teams.

Zoom releases software update to improve passwords, protect meeting IDs and secure cloud recordings
Zoom has been forced to take a long, hard look at its security and privacy in recent weeks. The company has not only put a pause on new features, it is focusing instead on making existing options more secure.
In an update to the software, Zoom has taken steps to improve the security of passwords, as well as introducing random IDs for meetings. The company has also enhanced password protection for meeting recordings stored in the cloud, and added other key security features.

Hackers are selling two serious Zoom zero-day vulnerabilities for $500,000
Both the Windows and macOS versions of Zoom have critical, unpatched security vulnerabilities that could be exploited by hackers to target users and spy on calls and meetings.
Security experts say -- despite not having seen the actual code for the exploits -- that the Windows version of Zoom is affected by an RCE (Remote Code Execution) described as being "perfect for industrial espionage". The zero-days have been offered for sale for $500,000.

deepin Linux 20 Beta ready for download
Some unfortunate people are so obsessed with COVID-19 coming from China that they forget all the positive things that come from the country, such as almost everything we buy in the USA. Yes, folks, many of the great products we enjoy daily, such as clothing and electronics, come from China, and it is important to remember that. Look, we are all humans, and borders are man-made -- there is no room for xenophobia in the world.
Most importantly, our friends in China have brought us one of the best desktop Linux distributions on the planet -- the Debian-based deepin. The Chinese developers have been teasing the upcoming deepin 20, and the DDE (deepin desktop environment) looks absolutely amazing. Today, I am excited to say we can all begin testing the operating system, as deepin 20 Beta is finally here!

You can buy the revolutionary Apple Magic Keyboard with trackpad right now
Last month, Apple did something consumers have long wished for -- it made the iPad a proper laptop. You see, the company announced an all-new iPad Pro and associated Apple Magic Keyboard. With the iPadOS 13.4 operating system, Apple's tablet finally gets proper trackpad support, and wouldn't ya know it, the aforementioned keyboard has an integrated trackpad. So, yeah, the iPad now functions as an actual laptop.
There was one problem, sadly, that was very much not like Apple. For whatever reason, the company began selling the new iPad Pro before the Magic Keyboard with trackpad was ready. And so, consumers have not been able to properly trial this new laptop experience, instead relying on Bluetooth mice and trackpads to try it out. Well, I am happy to say, beginning today you can finally buy the Apple Magic Keyboard!
