
Now you can merge Fortnite accounts
If you have played Fortnite on different consoles, you've very probably asked how you go about merging accounts so you can access all of your Vbucks and collectibles in one place.
Fortnite's initially messy approach to cross-platform gaming meant that many people ended up creating two (or more) accounts in order to be able to play with their friends. Epic Games dramatically improved cross-platform compatibility, but gamers who created multiple accounts were not able to share all of the weapons, currency and other goods collected between these accounts. Now this has changed.

Number of DDoS attacks falls but sophistication improves
2018 saw a decline of 13 percent in the overall number of DDoS attacks when compared to the previous year, but cybercriminals are turning to longer, more sophisticated, mixed and HTTP flood attack techniques.
This is revealed in Kaspersky Lab's DDoS Q4 2018 Intelligence Report, which also shows the average attack duration has grown. Compared with the beginning of the year, the average length of attacks has more than doubled -- from 95 minutes in Q1 to 218 minutes in Q4 2018.

Microsoft brags Surface in 20 new markets -- fails to say which [Updated]
Microsoft's Surface computers are pretty good machines -- if you like Windows 10, that is. A bit pricey, yes, but overall, they offer a quality experience. True, they are often a bit buggy, but Microsoft is usually pretty good about fixing them with various driver and firmware updates.
Today, Microsoft brags that Surface Pro 6, Surface Laptop 2, and Surface Studio 2 are now available in 20 new markets. Wow! Impressive, right? Actually, who friggin' knows if that is big news or not. You see, the Windows-maker is mum on what the new markets actually are. Maybe the list is a bunch of tiny countries with small populations, so the company is trying to bury that aspect. Who knows why Microsoft does what it does anymore. But yeah, 20 new markets!

Trakt tardily notifies users of data breach that took place over four years ago
Users of Trakt -- a service for "scrobbling", or tracking the movies and TV shows you watch in the likes of Plex and Kodi -- have received emails from the company notifying them of a data breach that took place way back in 2014.
Trakt says that although the security breach took place over four years ago, it only recently discovered it. The company says that an investigation is underway, but that it believes a "PHP exploit was used to capture data", including users' emails, usernames, encrypted passwords, names and locations.

Germany bans Facebook from combining user data collected from Instagram and WhatsApp
The German cartel office, the Bundeskartellamt, has imposed new restrictions on how Facebook processes the data it gathers about users of Instagram, Facebook and WhatsApp.
Germany's antitrust watchdog has hit the social network with a ban on combining user data it gathers from different sources, unless it has explicit consent from users. While Facebook is still free to gather data about Instagram users and WhatsApp users, this data cannot be automatically combined with data gathered via a users' Facebook account.

Microsoft continues to beat Google in battle of the enterprise apps
A new survey from identity platform Okta shows that 67 percent of knowledge workers prefer Microsoft Word over Google Docs, while only 15 percent report the opposite.
Another 16 percent identify Google Docs as a top-three most frustrating app. When it comes to email, 49 percent prefer Microsoft Outlook over Gmail, while 35 percent report the opposite.
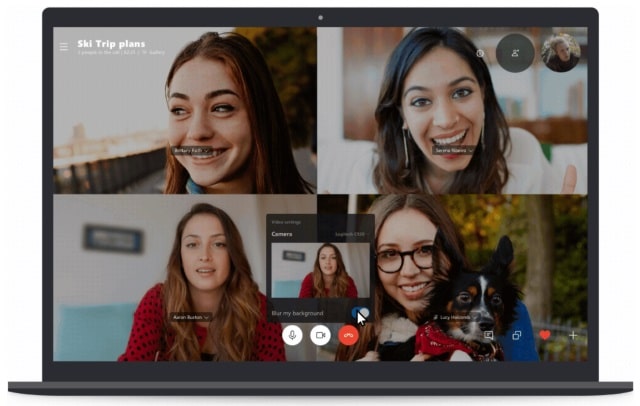
Microsoft brings AI-powered background blurring to Skype
A few months after adding background blurring to its Teams tool, Microsoft has brought the same option to Skype on the desktop.
The feature serves two purposes. Firstly it helps to focus attention on the person that is speaking, but secondly -- and perhaps more importantly -- it hides any untidiness (or secrets) that may be going on behind the speaker. It's another push from Microsoft to move people away from Skype Classic to Skype 8.

Flickr extends deadline, gives free users longer to download their photos
Under Yahoo, Flickr gave free users a whopping 1TB of storage for their photos, but new owner SmugMug was never going to be as generous. Three months ago the site announced its free plan would be changing, and non-paying users would be limited to storing a maximum of 1,000 photos online.
The cutoff for users to download their images or risk losing them forever was yesterday, February 5, but there’s some good news for anyone who failed to take action prior to then, as well as those who found themselves struggling to complete the export by the deadline as a result of Flickr only allowing 500 images to be saved at a time.

TP-Link unveils RE220 AC750 Wi-Fi Range Extender
Mesh networking is very popular these days, and for good reason -- its use of several access points makes it possible to blanket a home in Wi-Fi. The problem? If you already have a good router, it would be foolish to replace it entirely with a mesh system -- that would be a costly affair. Instead, if you need to deliver wireless access to a dead zone in your home, you should opt for a range extender. They are fairly inexpensive, and best of all, will work with your current router.
Today, TP-Link unveils its latest range extender -- the RE220. This little dual-band 802.11ac access point simply plugs into a power outlet. Then, with the help of a smartphone app, you can configure it to connect to your router. Also cool? It has a gigabit Ethernet port, so it can do double-duty as a wireless adapter for an internet-connected device that doesn't have Wi-Fi -- such as a desktop computer. Performance aside, it also has a striking white design with a gray crisscross pattern.

Failover clustering in the Azure cloud: Understanding the options
A number of options are available for providing high availability protection for applications running in the Azure cloud. Some of these options are cloud-based services. Some are in the operating system or application software. And some are purpose-built by third-parties. The numerous permutations and combinations available can make it extraordinarily difficult to choose the best and most cost-effective solution for each application.
In general, failover clusters are the best option for assuring high availability. Historically, failover clusters were relatively easy to configure and test in the enterprise datacenter using shared storage and standard features built into Windows Server. But in the Azure and other public clouds, there is no shared storage. This creates a need to find other options for running mission-critical applications in a public or hybrid cloud environment. This article examines the options available for providing high availability (HA) for applications running within the Azure cloud. Special emphasis is given to SQL Server as a particularly popular application for Azure.
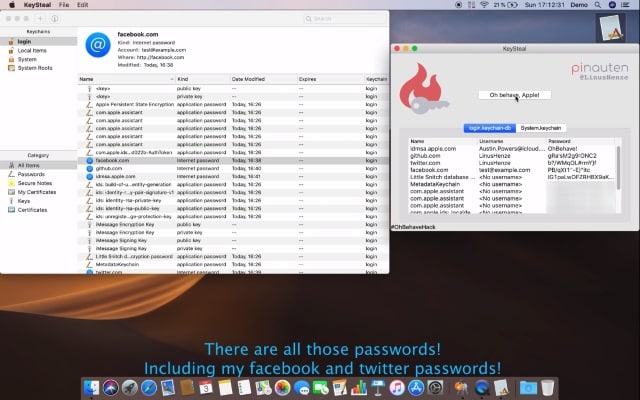
KeySteal: huge macOS vulnerability can be exploited to reveal keychain passwords
A disgruntled security researcher has revealed a one-click exploit that takes advantage of a macOS vulnerability to reveal all of the passwords stored in a Mac's keychain.
Linus Henze developed an exploit tool called KeySteal that uses a 0-day bug to extract keychain passwords on macOS Mojave and older. He stresses that neither root access nor administrator privileges are required, and no password prompts are generated by the tool. Henze is not going to help Apple to fix the problem because the company does not offer a bug bounty program for macOS.

Airline e-ticketing systems put passenger data at risk
Airlines could be putting the personal data of their passengers at risk by using unencrypted links, according to a new report.
Researchers at security and data management company Wandera have uncovered a vulnerability affecting a number of e-ticketing systems that could allow third parties to view, and in some cases even change, a user's flight booking details, or print their boarding passes.

Two-thirds of organizations bypass IT for digital transformation projects
According to a new report released by The Economist Intelligence Unit and sponsored by BMC software, 66 percent of organizations bypass IT when buying new technologies for digital transformation.
But despite this, 43 percent of firms still hold IT accountable if something goes wrong with their digital transformation initiatives.

Microsoft announces Sport Red Special Edition Xbox One Wireless Controller
Special edition video game controllers aren't very special anymore. Look, they are still cool, but there are so many different styles and colors being released, it can be hard to get excited each time one is announced. Microsoft even offers the ability to create a custom controller with its neat Xbox Design Lab.
With all of that said, I find myself smitten with a new Xbox One controller. Called "Sport Red Special Edition," it should not surprise you to know it is red. It isn't merely a red paint job, however -- it has different shades of red for the thumb sticks and buttons. The D-pad is a metallic red, and the face features a beautiful design of black crossing lines that create a series of triangles. It's definitely a stunner.

The Notifications Widget for Google Photos, Hangouts Chat and Google+ dies in March
Google+ is nearing the end of the line, and ahead of this Google has announced that its Notifications Widget is also to be killed off.
The widget -- which appears in the upper right-hand corner of various Google products including Gmail -- lets users know when there are notifications for various services such as Google Photos, Hangouts Chat and Google+. But when March rolls around, you'll have to rely on alerts for individual services instead.



