
Wikileaks finds a business model
Within minutes of the electrons drying on my last column about the Wikileaks CIA document drop called Vault 7, Julian Assange came out with the novel idea that he and Wikileaks would assist big Internet companies with their technical responses to the obvious threats posed by all these government and third-party security hacks. After all, Wikileaks had so far published only documentation for the hacks, not the source code. There was still time! How noble of Assange and Wikileaks!
OR, Wikileaks has found a new business model. When organized crime offers assistance against a threat they effectively control it’s called a Protection Racket and is against the law pretty much everywhere.

Ubuntu Linux 17.04 'Zesty Zapus' Final Beta now available for download in multiple DE flavors
When someone is interested in trying a Linux-based desktop operating system for the first time, they often choose Ubuntu. This is a smart choice, as it is easy to use, well supported, and quite beautiful. Even if you don't like the Unity desktop environment, there are several other DEs, or flavors, from which to choose -- GNOME, KDE, and Xfce to name a few.
Today, the Final Beta of Ubuntu 17.04 'Zesty Zapus' becomes available for download. While it is never a good idea to run pre-release software on production machines, Canonical is claiming that it should be largely bug free at this point. In other words, if you understand the risks, it should be fairly safe. Home users aside, this is a good opportunity for administrators to conduct testing prior to the official release next month.

WikiLeaks' Dark Matter documents reveal CIA hacks for Macs and iPhones
It's only a couple of weeks since WikiLeaks unleashed the first batch of its Vault 7 CIA documents, revealing the agency's spying and hacking capabilities. Now the organization has released a second cache of files dubbed Dark Matter, and they show that the CIA has developed tools for hacking Apple products.
Bold and exciting names like Sonic Screwdriver, DerStarke, Triton and DarkSeaSkies are the monikers given to attack the firmware of MacBooks and iPhones. What's particularly interesting about the documents is that they appear to show that the CIA had the ability to exploit Apple hardware and software a full decade ago.

How to create your first Alexa skill
For the last couple of weeks, Graham, Marcel, Sinem and I, from Red Badger, have been experimenting with Amazon’s Alexa Echo Dot. An Electric Hockey Puck that uses voice recognition powered by Amazon Alexa voice assistant.
In this post, I’d like to explain how one goes about creating their first Alexa skill.

eBay now recommends mobile over token-based two-factor authentication -- should you switch?
Two factor authentication strikes the right balance between convenience and security, which is why so many services offer it nowadays. But its implementation differs. Many companies have SMS or app-based systems, others prefer tokens, and some offer both as an option.
eBay falls in the third category, allowing users to receive the security code for the second authentication stage via SMS or a token. However, the company is now recommending users switch to the former method, touting its convenience as the main reason to abandon the token. But, should you take the advice?

CORSAIR ONE Intel Kaby Lake-powered VR-Ready gaming PC is small, powerful, and pricey
If you are a PC gamer, there is a good chance that you enjoy building your own computers. After all, building them yourself guarantees that you select every single component that goes inside. Not only can you pick the parts from a performance perspective, but aesthetically too -- for some folks, looks matter.
While a self-built gaming rig can be rewarding, it can be an expensive headache too. If something goes wrong, you have to reach out to each component manufacturer for support and warranty purposes. Alternatively, when you buy a pre-built machine, you have a single company to contact. Today, PC component maker CORSAIR announces an all-new gaming computer series -- its first ever. Simply called "ONE," it is designed to be both svelte and powerful. The hardcore mini PC is rather pricey, however, as it starts at $1,800 -- there are several "PRO" variants which will increase the cost dramatically. Unfortunately for AMD fans, this is an Intel/NVIDIA-only affair.

US companies start to pull ads from Google and YouTube over extremist content controversy
Last week saw the start of a backlash against Google after advertisers voiced concern that their ads were appearing next to extremist content. The Guardian, the BBC and the British government were among the first to start to pull their ads from the network, and the trend has spread to the US.
AT&T and Verizon are among American companies that have now announced that they are boycotting YouTube by pulling their ads. After concerns about being associated with terrorist and other extremist content, an increasing number of big names are calling on Google to make guarantees about ad placement.

New generation of cyber highwaymen could threaten parcel drones
Robbing the mail has a long and dishonorable history dating back to the days of the stagecoach. But UK-based online parcel broker ParcelHero is warning that automated delivery drones and droids could see the rise of a new breed of high-tech highwaymen.
The development of devices that alter the drone or droid's instructions, or simply stop them dead, is seen as inevitable. With UK online retail sales now worth more than £130 billion a year, if deliveries are to become largely automated and just one percent of items are waylaid using new technology, that's over £1bn of goods stolen a year.

Apple: iCloud is safe, but your passwords may not be
A group of hackers that goes by the name Turkish Crime Family, claims to have access to hundreds of millions of iCloud accounts, and it wants Apple to pay $75,000 in Bitcoin or Ethereum or $100,000 in iTunes gift cards to delete the compromised credentials.
This may lead one to believe that the collective has managed to hack iCloud, but according to Apple there "have not been any breaches" in any of its systems. "The alleged list of email addresses and passwords appears to have been obtained from previously compromised third-party services."
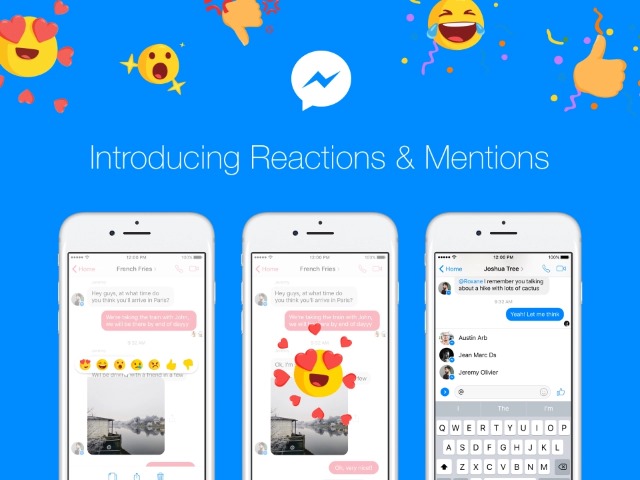
Facebook Messenger borrows from Slack with Reactions and mentions
Facebook is not shy about stealing features from other messaging tools, and it's usually Snapchat that is used as inspiration. With the latest update to Facebook Messenger, it's Slack that is being borrowed from.
Today Facebook Messenger gets two new features: Reactions and mentions. These work in very much the way you would expect, and Reactions make a successful transition from the Facebook newsfeed to Messenger after having made a brief appearance to a testing group recently.

Why ethical hacking is the top job of 2017
61 percent of UK businesses believe they will suffer from cyber crime in 2017, according to new research from Mimecast. These anxieties are justified: two thirds of large UK businesses were targeted by cyber criminals last year.
As the threat posed by cyber crime increases, businesses now invest more than ever in training, technology and skills -- global cyber spending is predicted to reach $1 trillion by 2021.
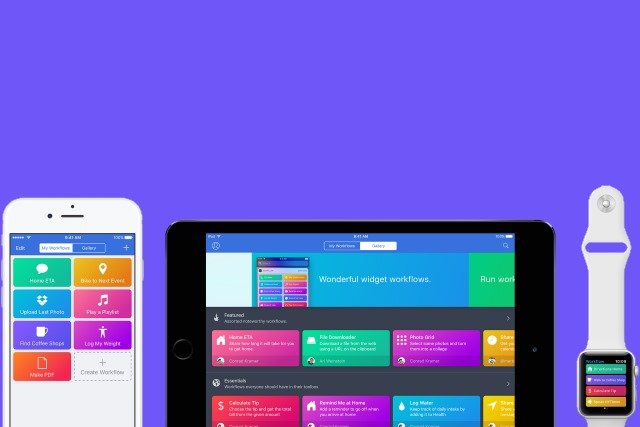
Apple buys automation tool Workflow, tweaks some features, and offers it to iOS users for free
Automation tools like IFTTT continue to be popular, and as if to prove this, Apple has just bought the iOS app Workflow. Working in a similar way to Automator for macOS, Workflow brings task-oriented automation to iPhone and iPad users.
There's good news to top off the acquisition revelation. Apple is not only keeping Workflow up and running rather than shutting it down, it's also hanging onto the original team of developers behind the app. Even better, Apple is making Workflow available free of charge, dropping the previous $2.99 price tag.
What challenges do Industrie 4.0 projects face?
Algorithms are at the heartbeat of Industrie 4.0 projects, according to Gartner, and that’s going to result in 30 percent of Industrie 4.0 projects sourcing algorithms from leading algorithm marketplaces by 2020.
That means a jump of less than five per cent, compared to what we currently have in the market.
New platform protects industrial IoT devices
Internet of Things devices are the latest threat vector that businesses have to deal with, introducing a potential extra weakness into corporate networks and leading experts to warn of increased risk.
To help guard against the threat, Mocana Corporation is introducing a new security platform designed to protect IoT devices and associated device-to-cloud communications.

Cobbler stores secret notes in an encrypted file
Cobbler is a tiny portable utility which stores plain text notes -- passwords, bank details, whatever you need to keep private -- in a secure and encrypted file.
Launch the program and you’re prompted for a master password. Enter something lengthy and secure, or press Ctrl+G to generate a strong passphrase for you, and a basic editor appears.



