
FBI investigates CIA leaks, Comey says 'There is no such thing as absolute privacy in America'
The FBI and CIA are working together on a joint investigation into the Vault 7 document cache published by WikiLeaks that supposedly reveals the CIA's hacking tools. Many of the companies mentioned in the documents for having exploitable vulnerabilities -- including Apple, the Linux Foundation, and Microsoft -- have spoken out about the leaks, but it has taken some time for the CIA itself to respond.
Speaking to the BBC, a CIA spokesperson said: "The American public should be deeply troubled by any Wikileaks disclosure designed to damage the intelligence community's ability to protect America against terrorists and other adversaries." FBI director James Comey has also spoken about the lack of privacy that now exists in the US.
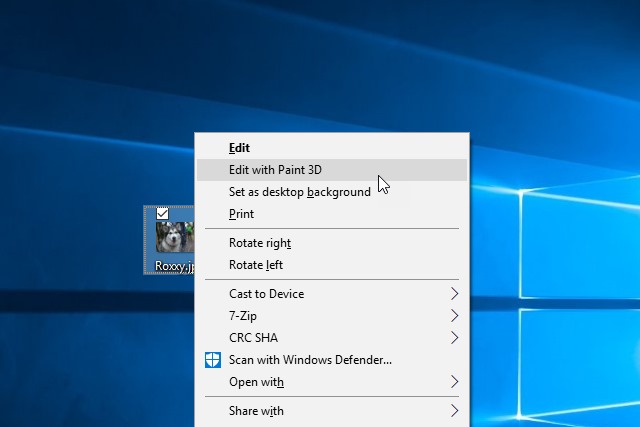
How to remove the 'Edit with Paint 3D' option from Windows 10 Creators Update context menus
If you've been an avid installer of Insider builds of Windows 10 (or you're reading this after the release of Windows 10 Creators Update) you'll no doubt be aware of Paint 3D. Microsoft's foray into 3D design is interesting, but it's certainly not for everyone.
In reality very few people are likely to actually make serious use of Paint 3D, but despite this Microsoft has chosen to throw an Edit with Paint 3D option into the context menu that appears when you right click on an image file. You probably don’t want or need this, so here's how to get rid of it.
Windows 10 Creators Update Preview Build 15051 for Mobile arrives on the Fast ring
With the Windows 10 Creators Update edging ever nearer to being ready for release, Microsoft is working hard to fix bugs and tidy things up.
Today sees a new build for Mobile (a new build for PC is expected in a day or so). Build 15051 offers a lot of changes, improvements and fixes including:

Enterprise data privacy challenges for 2017 -- and how to defend against them
If you’re not a data security professional, you may have missed the fact that January 28th was Data Privacy Day (also known as Data Protection Day, in Europe). Since 2007, Data Privacy Day has been designated as a day to raise awareness and promote privacy and data protection best practices.
As VP CSO for Zuora, I’m all for anything that raises awareness and promotes dialogue about data security -- but obviously I don’t just focus on data privacy once a year. For me, and my security colleagues, data privacy is an everyday concern. But the fact is that these days we’re seeing data privacy becoming an everyday concern for everyone. Whether it’s potentially hacked elections or IoT devices listening in on your family conversations, questions about data privacy -- and the implications of hacked data -- are becoming more pervasive and more concerning.

How IoT will impact the data center industry in 2017
The IoT (Internet of Things), is a network of devices connected to the Internet that gathers and transmits data. The ubiquitous adoption of smartphones, and the ability to connect to anyone, anywhere at any time, will have quite the impact on the data center industry in 2017. It is anticipated that more than 24 billion IoT devices will exist worldwide by 2020. These devices include everything from smartphones, to cars, to refrigerators. This increasing amount of data that is being produced by both consumers and providers will not only change our applications and devices, but also how data centers operate.
Below are three ways in which the IoT revolution will impact the data center industry in 2017:

Vault 7 fallout: Linux Foundation says it's "not surprising" Linux is targeted
In the wake of WikiLeaks' Vault 7 CIA leaks, Apple has been quick to point out that vulnerabilities mentioned in the documents have already been addressed. Microsoft and Samsung have said they are "looking into" things, and now the Linux Foundation has spoken out.
Nicko van Someren, Chief Technology Officer at The Linux Foundation says that while it is "not surprising" that Linux would find itself a target, the open source project has a very fast release cycle, meaning that kernel updates are released every few days to address issues that are found.

Hard Disk Sentinel 5.0 adds more test and repair tools
Veteran drive monitor Hard Disk Sentinel has just been updated to version 5.0, the first major release in more than a year.
The Professional build gets a new "Repair disk drive" method which scans for weak sectors and forces the hard drive to stabilize problems, or reallocate sectors if necessary.

Pyle launches Bluetooth Vertical Turntable
As a fan of Hip-Hop music, I spent a lot of my time as a young man digging through crates and collecting vinyl records. Many of my weekends were spent searching for gems in NYC at record stores such as Fat Beats and Beat Street -- it was a lot of fun. Today, I have probably over a thousand records -- many of which cannot be found on digital music services, meaning owning a record player is still a must.
Believe it or not, there are many modern turntables on the market nowadays, as the medium still has a big following. Today, Pyle releases an unusual model that plays the records vertically. While not the first player to do so, it is still out of the ordinary. In addition, it has a USB port for transferring the analog records to digital, plus Bluetooth for playing modern devices using the turntable's integrated speakers.

Microsoft reissues its infamous snooping patches for Windows 7 and 8.1
It’s good to keep Windows up to date, as it ensures you’re safe from the latest security threats, and you might benefit from other improvements. However, you shouldn’t always blindly install every patch that comes along.
Case in point are the infamous snooping patches KB2952664 (for Windows 7) and KB2976978 (for Windows 8.1), which today get yet another outing.

Consumer Reports to factor privacy and security into its technology reviews
There is much to consider when buying a piece of technology, but price and suitability tend to be at the top of most people's lists. In recent years, however, there has been an increased interest in privacy and security, and this is something that renown reviewer Consumer Reports is going to start taking into consideration.
Consumer Reports most recently hit the headlines for deciding not to recommend the new MacBook Pro (although it later changed its mind), and now the non-profit has teamed up with a number of privacy, security, and consumer rights organizations with a view to creating a new digital standard for products to live up to. The aim is to put data security and privacy first, just as many consumers are starting to do.

Check Point adds advanced security to the Google Cloud Platform
Businesses often have security concerns surrounding moving their data to the cloud. For users of the popular Google Cloud Platform, Check Point is offering additional security with the launch of a new product.
The release of vSEC for Google Cloud Platform delivers advanced security that is built for agile and scalable cloud environments.

WebCatalog runs your favorite web apps natively
WebCatalog is an open-source cross-platform tool which runs your favorite websites and services as native desktop applications.
A huge list of supported services includes Amazon, Basecamp, BBC iPlayer, Bing, Dropbox, Evernote, Facebook Messenger, Gmail (and just about every other Google app), iCloud, iCQ, OneDrive, Netflix, Outlook.com, Skype, Spotify, Twitter, WhatsApp, Wikipedia and more.

Generation Z finds products online but prefers to shop in-store
The Gen Z population -- those born between the late 1990s and the mid-2000s -- still value the in-store experience even though they're likely to search for products online.
This is among the findings of a study into shopping habits by retail analytics specialist Euclid Analytics. It reveals that this age group like to see, hold and try on products before buying and 28 percent of Gen Z shoppers want to engage with store associates while shopping, the most of any generation.

Microsoft shuts down So.cl social network
The So.cl experiment will soon be over, as Microsoft's Fuse Labs just announced that it will shut down the social network this month. Launched nearly five years ago, So.cl was meant to appeal to users wanting to share search queries and results.
So.cl seemed to be eyeing a very limited audience from the start, a belief confirmed over the years by the lack of any official figures from Microsoft about its userbase. Alexa puts So.cl's global ranking at just over 466,000 -- to put things into perspective, MySpace is currently in the 3,075th place.

Over 60 percent of organizations hit by ransomware in 2016
Ransomware continues to be a major problem, a new report reveals that more than 60 percent of organizations suffered some form of ransomware attack in 2016.
The good news is that 54 percent successfully retrieved their data without resorting to paying the ransom. These are among the findings of the fourth-annual Cyberthreat Defense Report from security research firm CyberEdge Group.


