
The problems facing chief information officers
With technologies like cloud systems and big data increasingly in demand the role of the chief information officer (CIO) is evolving and throwing up new problems all the time.
Enterprise search company Lucidworks has produced an infographic looking at the changes most affecting CIOs and what can be done to embrace them.
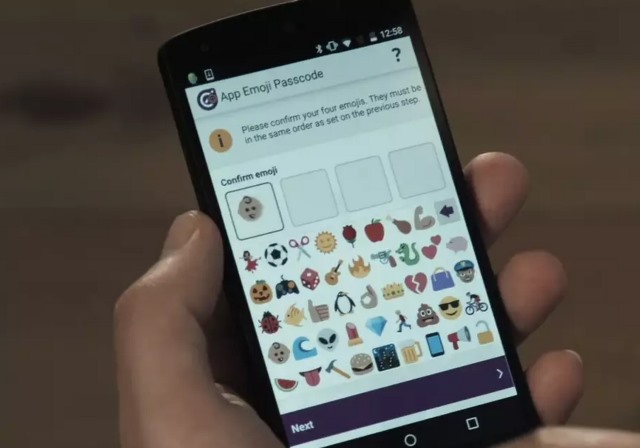
Emoji could be used for your next PIN
The humble PIN is a common way to secure access to accounts, but it has one major problem -- it is, usually, limited to using the digits 0-9. A UK firm thinks it may have come up with a better solution: emoji-based PINs.
Intelligent Environments' Emoji Passcode system can be used to secure accounts with ideograms. The company argues that Emoji passcodes are not only easier to remember than number-based alternatives, but also more secure. This is thanks to the fact that there is a pool of 44 Emoji to choose from, and research also suggests people find it easier to remember images.

Download images from a Twitter account with dhIMG Twitter
It’s easy to browse the images on a Twitter account. Saving them is more of a challenge. Even the right-click menu may not have a "Save Image As" option.
DhIMG Twitter is a tiny free tool for Windows which avoids all these hassles by directly downloading the images (but not the videos) for a named account.

Five into one will go -- ARCTIC Smart Charger 8000 [Review]
Most of today's gadgets seem to use USB for charging their batteries so you inevitably end up with a whole stack of cables and the mains power adapters to go with them.
If you're looking to simplify things the Smart Charger 8000 from Swiss company ARCTIC may be the solution. It's a little box with five USB ports that allows you to charge a number of devices at the same time. It intelligently detects the devices connected to it in order to provide the best charging speed for each one.

Privacy concerns stand against wearable adoption
As more wearable devices continue to enter into the market and into our lives, questions are being raised as to how vulnerable this may be making us when it comes to potential security and privacy risks.
Smartphones already have the capacity to hold a large quantity of data about us as individuals and wearable technology is likely to work in a similar way -- with fitness trackers able to store information about our health, for example, or the routes taken during exercise sessions.

Manjaro Linux 0.8.13 is here
If you are a Linux desktop user, you probably have a favorite distribution. Sticking to one distro is a good option, as it is generally less stressful and easier to master. With that said, however, some people are distro hoppers; constantly trying new Linux-based operating systems. This can be fun too, but the downside is that you are in a constant state of change -- a solid foundation has its benefits.
There are pros and cons to both practices, but I would suggest a happy medium; stick with the operating system you love, but try other ones -- on the side -- to remain knowledgeable on the state of the Linux community. One such distro I suggest trying -- on a VM or separate partition -- is Manjaro. Hell, if you like the Arch-based OS, you may just commit to it full time. Today, the newest version, 0.8.13, sees release, featuring two of the best desktop environments -- XFCE 4.12 and KDE Plasma 5.3.1.

Snowden files hacked by China and Russia
UK secret services say that the encrypted files Edward Snowden held from his time working at the NSA have been accessed by intelligence agencies in China and Russia. The Sunday Times reports that the top secret files have been hacked meaning that British and American spies could be identified and located.
Wanted by US authorities, Snowden has been in hiding for some time now. It is believed that the time he spent seeking refuge in Hong Kong and Moscow may have given security official the opportunity to access the data he held. Although the data was protected, it is thought that the encryption was hacked, and US and UK intelligence services have been "forced to intervene and lift their agents from operations to prevent them from being identified and killed".
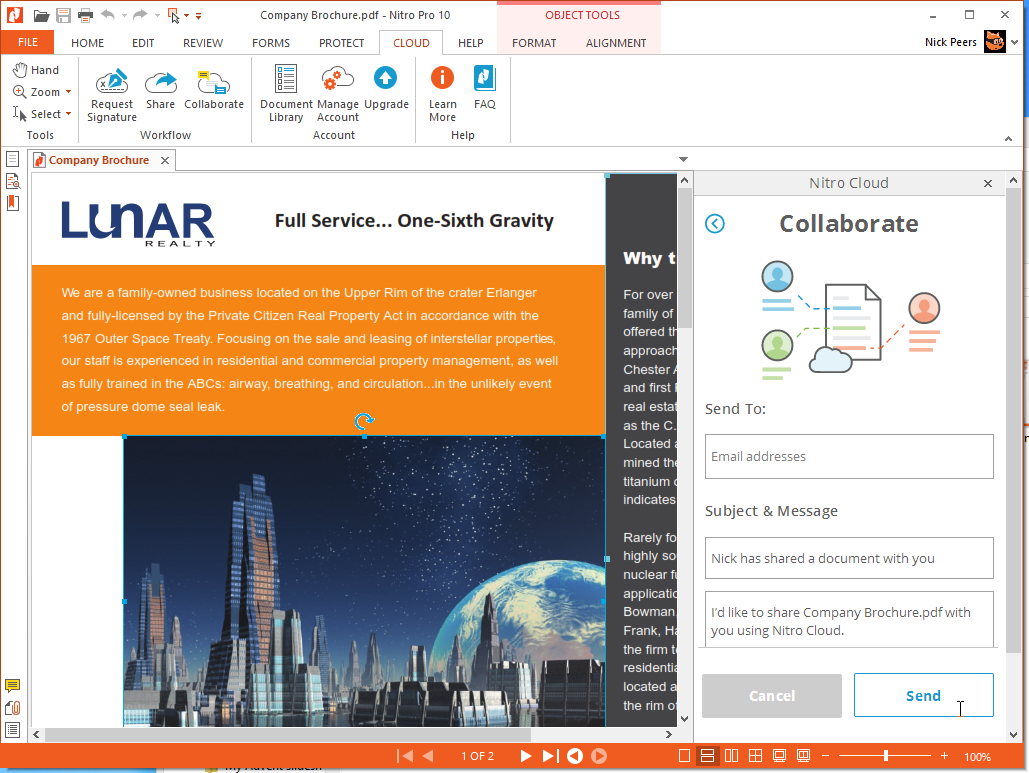
Nitro Pro 10 [Review]
Nitro Pro has been the budget alternative to Adobe’s expensive Acrobat PDF conversion and editing tool for a number of years now.
It’s been 18 months since Nitro Pro 9.0 was released, which added a smattering of minor new tools and refinements, and version 10 continues in the same vein, unveiling a handful of new tools, some useful improvements and the promise of better performance -- up to 40% faster in fact.

Disney's IT troubles go beyond H-1Bs
Disney has been in the news recently for firing its Orlando-based IT staff, replacing them with H-1B workers primarily from India, and making severance payments to those displaced workers dependent on the outgoing workers training their foreign replacements. I regret not jumping on this story earlier because I heard about it back in March, but an IT friend in Orlando (not from Disney) said it was old news so I didn’t follow-up. Well now I am following with what will eventually be three columns not just about this particular event but what it says about the US computer industry, which is not good.
First we need some context for this Disney event -- context that has not been provided in any of the accounts I have read so far. What we’re observing is a multi-step process.
How to sideload apps in Windows 10
The sideloading of apps is something that most people associate with smartphones and tablets. If you want to install unofficial apps on your iPhone, Android, or Windows Phone handset, there are things you can do to make this possible. The same is true with Windows 10 assuming you are using build 10122 or newer.
If you want to be able to install apps that are not featured in the Store, all you need to do is enable Developer Mode. As the name would suggest, this is something that will be of particular interest to developers as it makes it possible for them to test out their own apps before they hit the store, but there's nothing to stop anyone from enabling the mode to take advantage of the same feature. Here's what you need to do.
Wikimedia secures connections with HTTPS encryption by default
There is a movement calling for the encryption of all web traffic. The cause of this could be laid at Edward Snowden's door, but there's no getting away from the fact that in recent years there is an increased interest in security and privacy. To this end, Wikimedia has announced that it is now using HTTPS to encrypt all of its traffic -- including that to Wikipedia.
We've already seen the US government embrace HTTPS, and companies like Google and Facebook are making it easier to control privacy settings. Apple has hit out at companies that fail to do enough to protect users' privacy, and Wiki media is taking the extra step of also implementing HSTS, just days after Microsoft announced that this would be supported by Internet Explorer 11 under Windows 7 and 8.1.

Amazon publishes opaque transparency report
Post-Snowden there is great interest in just what involvement the government has with technology firms. There are frequent requests from government agencies for information about users and the likes of Google, Snapchat, and even the NSA itself have all released transparency reports that reveal, in broad strokes, the number of requests for data they have received.
Amazon is the latest company to release a transparency report -- although the term really should be used in the loosest possible sense. The report includes scant details about the number of subpoenas, search warrants, court orders, and national security requests received in the first five months of 2015. The report is so vague as to be virtually meaningless.

Facebook factors in article view times to personalize news feeds
Facebook today announced that it is making another change to the way it determines which stories are displayed in News Feeds. As well as factoring in how many people have liked or commented on a story, the social network will now also take into account how long people spend reading individual articles.
But it's not quite as simple as saying that stories people spend a while looking at are the most popular. Some lengthy visits are the fault of slow connections, for example. Equally, it is not safe to assume that only heavily liked and commented articles are the most read -- there are some stories that do not lend themselves to liking and commenting. Today's change aims to strike a balance between different weightings.

Google announces YouTube Gaming -- puts Amazon's Twitch in crosshairs
Playing video games is a very fun hobby. Hell, for some people, playing them is a job; yes, professional competitive gaming is a real thing. You know what else is cool? Watching other people play. While it was an absurd notion years ago, nowadays, people enjoy being spectators to another person's gameplay. I watch Pewdiepie, like, every day.
The most famous platform for streaming gameplay is Twitch, which is why Amazon bought the service for a ton of cheddar. Not to be outdone, however, Google today announces its own streaming service for gamers -- the unimaginatively named YouTube Gaming. While I do not expect a mass exodus from Twitch, Amazon's service will certainly lose some of its luster as a result. Interestingly, it will be run by former pro-gamer, Ryan Wyatt -- aka Fwiz -- most widely known as the former love interest of Justine Ezarik -- aka iJustine.

Uber puts passengers at risk with a flawed driver-approval process
Uber, the San Francisco-based private taxi firm, is putting its passengers in grave danger. The company uses a computerized driver sign-up system that can be easily fooled into authorizing drives with fake insurance papers. The transport network exploded onto the scene a few years ago, and a whistleblower claims that it is all too easy to cheat the system making it possible for virtually anyone to sign up to be an Uber driver.
The vulnerability was found to have been exploited in London where there are around 15,000 Uber drivers in operation. The scam has been demonstrated by The Guardian who worked with a whistleblower to fraudulently sign up as a driver. It was achieved using fabricated insurance papers from a made up company with a fake letterhead.



