
Plugable launches UD-4VPD USB4 Dual HDMI Docking Station
Today, Plugable releases its all-new UD-4VPD USB4 Dual HDMI Docking Station. Offering high-resolution displays and 11 ports via a 40Gbps USB4 bandwidth, this docking station promises to supercharge your work setup.
The UD-4VPD, currently retailing for $199.95 on Amazon with a limited-time $15 discount coupon, is designed to enhance productivity with its impressive display resolution options. Using the latest chipsets, it supports dual HDMI displays up to 4K at 120Hz or a single 8K display at 60Hz, ensuring fluid and stunning visuals.

60 percent of consumers prefer a fintech app to an accountant
Fintech apps have simplified financial management to the point where 60 percent of people will now seek advice from personal finance tools before reaching out to financial professionals.
A new survey from Capterra makes gloomy reading for accountants as it finds 64 percent of fintech users feel that these tools have significantly reduced their reliance on financial advisors.
Businesses struggle to make decisions due to 'analysis paralysis'
In difficult economic times businesses need to make decisions quickly and data is a key part of enabling those choices.
But research from analytics cloud platform Alteryx shows enterprises are struggling to make timely, insight-driven decisions because of 'analysis paralysis' caused by issues around ownership of and access to data.

CORSAIR acquires Drop
CORSAIR has announced its acquisition of select assets from peripheral-maker Drop. Established in 2011, Drop (formerly known as Massdrop), mostly focuses on enthusiast products, such as customized "DIY" keyboards, aftermarket designer keycaps, and desktop accessories. Recently, Drop expanded its portfolio to include additional designer products for the desk and workspace, known as Battlestation products.
Drop's notable collaborations include officially licensed keycaps inspired by The Lord of The Rings and Marvel Infinity Saga, where the Drop community actively participated in voting for new color schemes and concepts.

Securing the oil and gas industry
The oil and gas sector remains a crucial pillar of the global economy, an industry that supports not only millions of jobs worldwide but also underpins essential energy provisions for homes, businesses, and transportation networks.
Yet, as digital technology continues to pervade this sector, oil and gas companies are increasingly being exposed to critical cyber threats. The industry's increasing dependence on digital systems has escalated the importance of robust cybersecurity strategies, presenting an array of unprecedented challenges.

Why SOCs need urgent modernization [Q&A]
Security Operations Centers (SOCs) aim to detect, investigate, remediate, and restore organizational systems to a fully functional, secure state, whether it's defending against insider threats, data exfiltration attempts, or malware attacks.
However, examining the daily issues faced by many SOCs reveals a concerning array of challenges that place increasing pressure on the work of SOCs and the dedicated professionals who manage them.
You should delete Windows 11 and install Ubuntu-based Linux Mint 21.2 'Victoria' now
Windows 11, the latest offering from Microsoft, fails to impress when compared to the exciting release of Linux Mint. Codenamed "Victoria," Linux Mint 21.2 is a long-term support release that guarantees extended support until 2027, ensuring its users stability and reliability. This version boasts a range of updated software, refinements, and new features that make it a far superior choice for desktop users.
Based on Ubuntu 22.04 and utilizing kernel 5.15, Linux Mint 21.2 offers three desktop environments to choose from: Cinnamon (5.8), MATE (1.26), and Xfce (4.18). The improvements in Linux Mint 21.2 are plentiful, addressing issues such as touchpad drivers, Wine installation enhancements, sound and microphone problems, and more.
XPG unveils low-profile LANCER BLADE DDR5 memory for gamers and enthusiasts
XPG, the gaming division of ADATA, has launched its new LANCER BLADE DDR5 and LANCER BLADE RGB DDR5 memory modules. These RAM products feature a low-profile heatsink design, making them ideal for small cases with limited space. This eliminates the need for motherboard assembly adjustments.
The XPG LANCER BLADE series are equipped with high-quality Hynix chips that ensure low latency and easy overclocking. Gamers can enjoy a hassle-free speed boost with just one-click overclocking, enhancing their gaming experience. The XPG LANCER BLADE series also supports Intel XMP 3.0 and AMD EXPO, making it compatible with the latest Intel and AMD platforms.

What a steal! How retailers can protect customer data from cybercriminals
Recent Salesforce research shows 52 percent of consumers expect their offers to be personalized. To create these tailored offerings and drive a seamless customer experience, retailers gather vast amounts of personally identifiable information (PII) -- from addresses to purchasing history and payment information. This makes them an irresistible -- and relatively low risk -- target for cybercriminals. As a result, data breaches within retail are increasingly common, even for major retailers -- as we saw earlier this year with the JD Sports Data Breach, which exposed the PII of around 10 million people.
To help protect consumers, governing bodies are putting increased pressure on companies to comply with data protection rules -- including the UK’s upcoming Data Protection and Digital Information Bill. Consumer trust is key when it comes to retail too. So, companies unable to protect their customer data not only risk enormous fines, but significant damage to their brand reputation. So, following recent high-profile retail breaches, how can brands protect their customers’ personal data?
Microsoft rolls out updated dark mode toting Paint app to more Windows 11 users
It is several weeks since Microsoft finally gave Windows Insiders on the Canary and Dev channels access to an updated version of its Paint app. Now the company is making the new edition of the beloved graphics tool available to more people.
The big news in this latest release is that, at long last, Paint supports dark mode. But there are other additions and improvements includes new keyboard shortcuts and a wider adoption of the Windows 11 look.

3 ways to adopt composable architecture that every technical leader should know
Digital transformation initiatives are keeping software developers on their toes, intensifying the need for digital platforms that unlock the vast amounts of data now available in the modern enterprise. Whether we’re talking about data that powers a project, a team, or an entire company, a data architecture that enables the agile and modular deployment of mission-critical systems and apps has become essential for keeping pace with the changing business landscape.
According to a PwC Pulse Survey, agility is a key priority for executives for 2023 -- and as such, software developers working on corporate initiatives such as websites, internal apps, data analytics, or SaaS offerings are prioritizing flexibility and scalability as they look for ways to leverage existing data stacks for building innovative, scalable platforms.
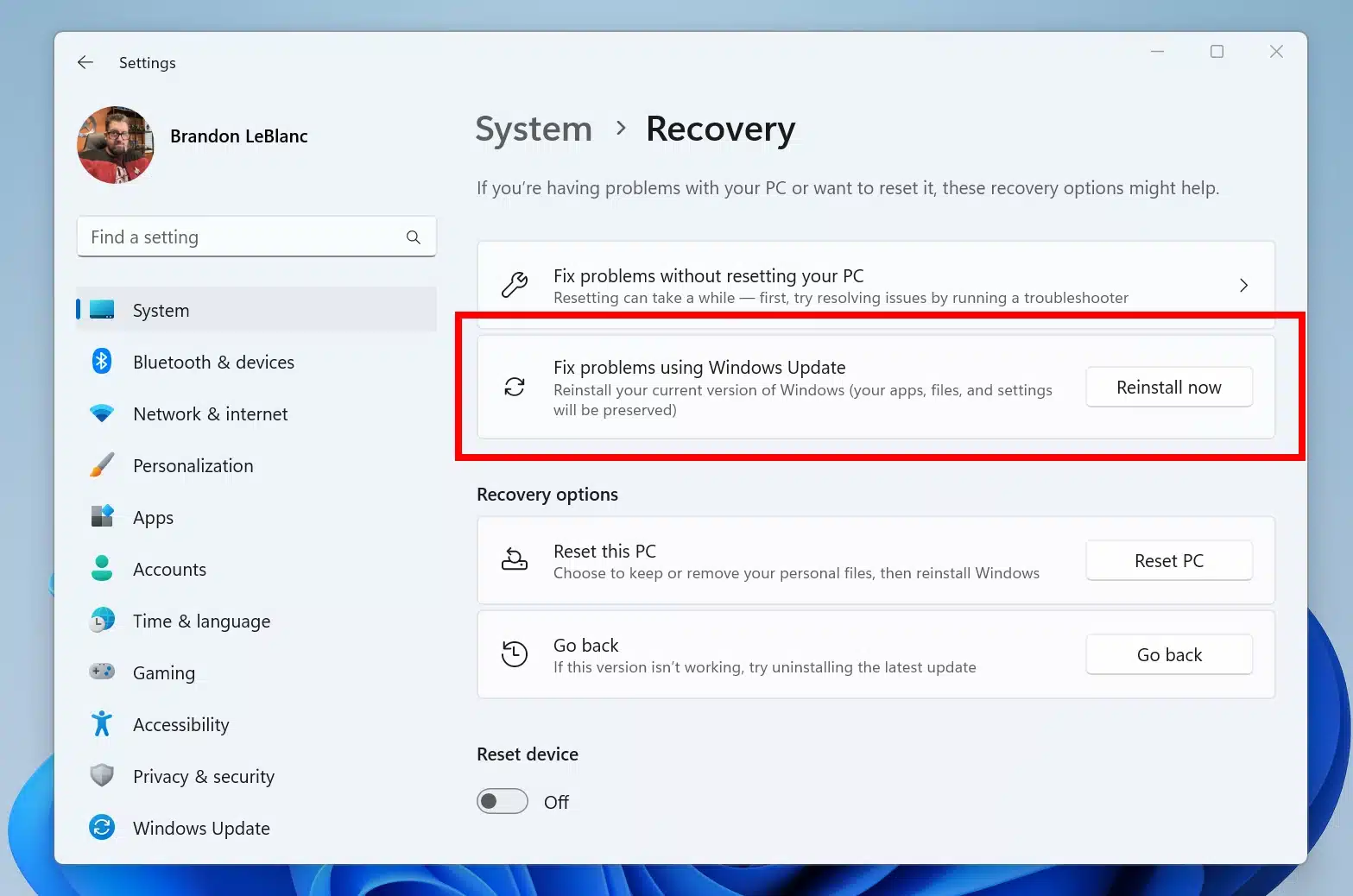
Microsoft is working on a new reinstall feature to let you fix Windows 11 without losing files, apps or settings
Windows 11 is getting a new recovery feature lets you repair with losing files, apps or settings. Microsoft is currently testing the "Fix problems using Windows Update" option in preview builds of Windows 11.
The feature is an alternative to completely reinstalling Windows 11 from scratch and having to reconfigure all of your software and settings. It is also more advanced than a typical in-place reinstallation of the operating system and is -- in theory, at least -- more likely to fix issues. Here's everything we know about the upcoming "Fix problems using Windows Update" recovery feature.

Debian 12-based MX Linux 23 'Libretto' achieves release candidate status
Friday is here, and if you were looking for something fun to do this weekend, I have some exciting news. You see, MX-23 RC1 is finally here and ready for us to test! It's like a breath of fresh air, blending the stability of Debian 12 "Bookworm" and MX repositories.
True to its roots, MX-23 sticks with sysVinit by default. But for those of us who like to have options, it still keeps systemd in the mix for installed systems. This RC1 release is more than just a polished version of the beta -- it brings a whole bunch of bug fixes, new wallpapers, themes, translations, and updated apps to the table.

Satechi Dual USB-C Hub enhances Microsoft Surface Pro 9 Windows 11 tablet
Tech accessory manufacturer Satechi is expanding the capabilities of Microsoft’s Surface Pro 9 with the all-new Dual USB-C Hub. Lightweight and compact, this portable device is designed for work on-the-go, weighing just 40 grams and measuring less than 4.5 inches.
Specifically designed to enhance the functionality of this Windows 11 tablet, the hub boasts six powerful ports, including a USB4 pass-through port supporting 100W power delivery, USB-C and USB-A 3.2 Gen 2 ports, an HDMI 2.0 port, and SD/microSD UHS-I card slots.

Microsoft reveals everything you need to know about Windows 11 23H2
The rollout of Windows 11's Moment 3 update may only just have made its way to most users, but Microsoft already has other updates in the pipeline. Coming up later this year is Windows 11 23H2. We've come to expect that this will not be an update that's packed with new features, but that's not to say that it is not significant -- expect to see the update enabling Windows Copilot as Windows 11 enters the AI era.
Microsoft has now revealed more information about the upcoming release, including the fact that it is scheduled to rollout to users in the fourth quarter of the year -- effectively making it Windows 11 23Q4. What's important, though, is that users have to prepare for the launch.



