Best Windows 10 apps this week
Four-hundred-and-eight in a series. Welcome to this week's overview of the best apps, games and extensions released for Windows 10 on the Microsoft Store in the past seven days.
Future versions of Microsoft's Windows 10 operating system may notify users when apps get added to the system's autostart; users may go directly to the startup apps section of the Settings app to manage these then.

How SASE is transforming enterprise network security [Q&A]
Securing enterprise networks used to be a matter of simply defending the perimeter, but in the new normal world of much higher levels of remote access, things have become more complicated.
One of the technologies being used increasingly by businesses is Secure Access Service Edge (SASE). We spoke to Mike Wood, chief marketing officer of Versa Networks, to discover more about SASE and what it can deliver.
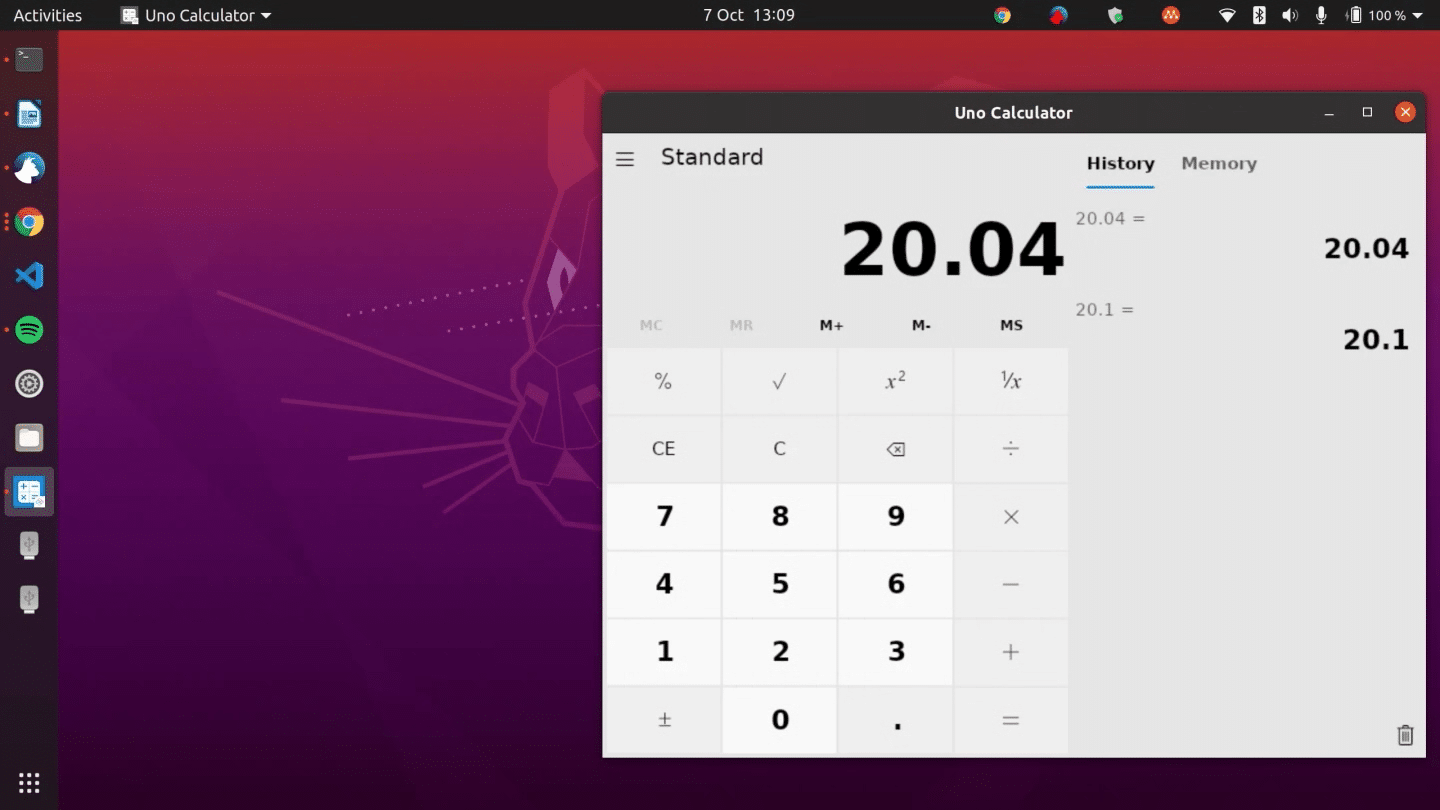
How to install Microsoft Windows Calculator on Linux
Microsoft is no longer an enemy of the Linux or Open Source communities. Believe it or not, the Windows-maker is an ally these days. Shocking, I know, but totally true. Linux is now built into Windows thanks to WSL, and Microsoft has several apps available for Linux.
The company has even made some of its apps open source as well. For instance, back in 2019, Microsoft released the source for Windows Calculator on GitHub. And now, that calculator app has been ported to Linux by Uno Platform. Best of all, its insanely easy to install as it is packaged in Snap format.

Why businesses need to maintain GDPR compliance during remote working [Q&A]
The General Data Protection Regulation (GDPR) came into force in the EU in May 2018 with the aim of giving individuals greater protection over how businesses use their data.
But the COVID-19 pandemic has thrown up new challenges and remaining compliant with the regulations in an age of remote working is one of them. We spoke to Brendan Kiely, managing director and co-founder of secure remote working specialist ThinScale Technology to discuss the implications of GDPR and the 'new normal'.

Macrium Reflect 7.3 resolves long-standing scheduling issues by debuting own Task Scheduler
Paramount Software UK has unveiled Macrium Reflect Free 7.3, a major new update of its Windows drive-imaging backup tool.
Version 7.3 unveils a new integrated task scheduler to address increasing frustration with problems scheduling backups using the previous system, which tied into the Windows Task Scheduler. Paid-for editions also gain improved protection against ransomware thanks to tweaks to the Macrium Image Guardian feature.

Cybersecurity pros embrace automation but younger staff worry about being replaced
New research from Exabeam reveals that while 88 percent of cybersecurity professionals believe automation will make their jobs easier, younger staffers are more concerned that the technology will replace their roles.
The 2020 Cybersecurity Salary, Skills and Stress Survey, an annual survey of security practitioners finds overall satisfaction levels continue a three-year positive trend, with 96 percent of respondents indicating they are happy with their role and responsibilities and 87 percent pleased with salary and earnings.

Logitech launches affordable Z407 Bluetooth 2.1 computer speakers
The speakers that are built into laptops or integrated into computer monitors have gotten much better over the years, but make no mistake, they still don't provide an optimal audio experience. Whether you are watching movies or listening to music, investing in superior speakers will certainly make your life much more enjoyable.
The great thing is, solid computer speakers don't have to break the bank either. Today, Logitech launches the Z407 Bluetooth 2.1 computer speaker system, and it is priced well under $100. What makes these particularly cool is that the two satellite speakers can be positioned horizontally or vertically, making them fit well on almost any desk.

Microsoft is foisting Office web apps on Edge users
Microsoft is no stranger to using Windows and other software to promote more of its own apps and services. The latest way the company is doing this is via Edge.
Accusations of using its products as an advertising tool or as a means of forcing products onto users are nothing new for the Windows maker, and the company's latest move with Edge does nothing to shake them off. The browser has been found to install Microsoft Office web apps without asking for permission.

Microsoft releases Windows 10 Build 20236 with the ability to change the refresh rate of your display
Windows Insiders on the Dev Channel get another new Windows 10 build to play with today.
Build 20236 adds the ability to change the refresh rate of a selected display by going to Settings > System > Display > Advanced display settings. The rates on offer will vary depending on what your hardware supports, but a higher refresh rate should deliver smoother motion.

Samsung launches PRO Plus and EVO Plus SD Cards
A digital camera without a storage card is like a car without gas -- pretty much useless. You need a memory card to store the photos and videos you take, and most cameras don't come with any onboard storage these days.
There are no shortage of SD cards (Amazon is littered with them), but you should always make sure you are purchasing one made by a reputable company. Don't recognize the brand? Don't buy it. You don't want to lose your valuable data when that cheap card dies prematurely.

Get 'Learn Microsoft Office 2019' ($17.99 value) FREE for a limited time
Learn Microsoft Office 2019 provides a comprehensive introduction to the latest versions of Microsoft Word, Excel, PowerPoint, Access, and Outlook. With the help of illustrated explanations, this Microsoft Office book will take you through the updated Office 2019 applications and guide you through implementing them using practical examples.
You'll start by exploring the Word 2019 interface and creating professional Word documents using elements such as citations and cover pages, tracking changes, and performing mail merge. You'll then learn how to create impressive PowerPoint presentations and advance to performing calculations and setting up workbooks in Excel 2019, along with discovering its data analysis features.

How to stay connected in the no-touch world of software sales
While the pandemic disrupted business, the great remote migration made believers out of many decision-makers. Despite having to implement sweeping changes very quickly, the long touted benefits of remote working proved real and it’s obvious many aspects will remain in place for good.
Software companies already had employees who were quite familiar with working remote and maintaining productivity. Yet, while these companies were generally in a better position to adapt to the "new normal," their sales teams were impacted just like those in any other industry -- perhaps even worse. After all, they deal with complex technology that traditionally has required a lot of face-to-face time to educate prospects. No-touch software sales is tricky business, particularly when prospects are accustomed to hands-on experiences and trials. That said, software companies need to rethink their strategies and procedures.

Revelations: Enterprise architecture in the wake of COVID-19
When COVID-19 unexpectedly shut down the country, enterprises were hit hard. Millions of workers went remote almost instantly. In the months since, we’ve learned a lot about our networks and how they respond to various stressors. With Google, Facebook and others announcing that employees won’t return to campus until at least July 2021, and as companies like Twitter and Square debut new policies that allow any employee to work from home permanently, post-pandemic, it is clear that remote work will be a fixture in business for some time to come. As such, issues in endpoint management will need to be addressed in order for networks to run efficiently.
To understand what’s happening with infrastructure today and how COVID-19 is prompting long-term changes, it’s important to first understand the past.

Businesses using product intelligence see stronger growth
One of the side effects of the pandemic has been to accelerate digital transformation efforts, but a lack of good product intelligence means many companies don't have the proper tools in place to understand and act on customer data.
New research from product intelligence platform Amplitude shows that 97 percent of businesses say improving the digital experience for users is a priority, but 71 percent say they don't know exactly where to start when it comes to understanding their users' behavior and 38 percent don't know what to do to improve their digital experience.

Akamai launches new API security tool
APIs have become an important mechanism in the modern web, allowing organizations to create powerful web and mobile experiences, using back end data and logic to create new and innovative offerings.
But in order to use them safely they need to be secured and that means understanding what APIs there are in your environment, what their function is and what their traffic profile looks like.



