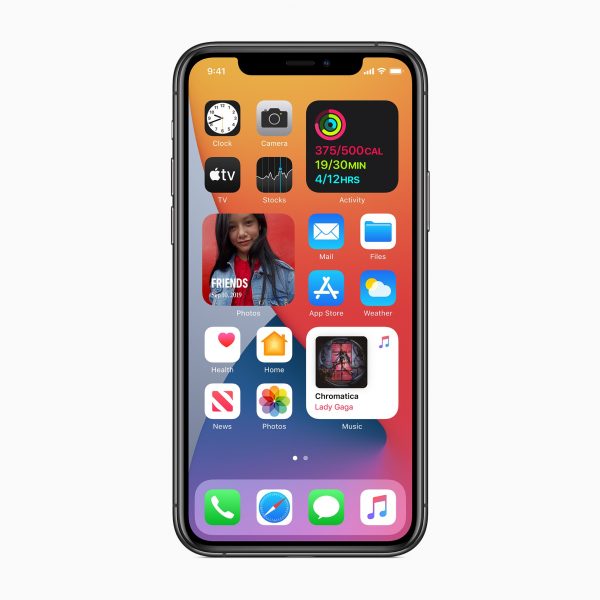
Apple reveals iOS 14 -- here's what's new
Apple's WWDC 2020 event was held virtually, open to everyone around the world to view for free. Among the many announcements to come from the event was iOS 14 -- and there's a lot to look forward to for iPhone owners.
What can you expect? Major improvements and changes are being introduced to the home screen and the way app pages work, and widgets are getting a serious overhaul. Siri sees a number of improvements, as does messaging. There's also an entire new type of apps called App Clips. Let's take a closer look.

US taxpayers think filing returns online is risky -- but they do it anyway
Thanks to the COVID-19 pandemic and extended tax filing deadline for 2020 its likely that people will be submitting their returns over a longer period this year.
New research from information security company Shred-it shows that most Americans file their tax returns online, even though many believe this puts them at greater risk of fraud.

Adobe Flash Player dies this year and you'll be told to uninstall it
Adobe Flash Player has been a blight on the internet for more years than most people care to think about, but its days are finally numbered.
We've known for a number of years that the software is reaching end of life (EOL) at the end of this year, and Adobe will stop distributing it after this date. But Adobe is going further, and will soon start to prompt people to uninstall Flash Player from their computers.
How to deregister your phone number from Google RCS chat
With absolutely zero fanfare, Google has rolled out a system that lets you turn off RCS chat features to help avoid problems such as missing messages.
The simple form that has appeared online is very similar to the one used by Apple. The online system can be used even if you do not have your previous phone with you, so you can deregister your phone number from your computer.

How to watch Apple's virtual WWDC 2020 for free -- iOS 14 and new hardware expected
Later today, Apple will host its first virtual Worldwide Developers Conference. Due to the coronavirus pandemic, WWDC 2020 is an online-only event, and you can tune in to see all of the new announcements.
Things kick off at 10:00 AM PDT with a special event keynote speech from company CEO Tim Cook. As ever, we don't know for sure what will be revealed at the event, but we can expect to learn about iOS 14, WatchOS 7 and macOS 10.16, as well a new hardware including Arm-based Macs.

HUAWEI launches AMD variant of the MateBook 13, but there’s a huge catch
I’m a huge fan of AMD desktop processors and GPUs, but the company’s mobile chips? Not so much. Don’t get me wrong, there have been some decent AMD-powered laptops over the years, but historically, Intel processors have been the best for notebooks.
Until recently, that is. AMD’s new mobile Ryzen 4000 processors have received universal acclaim thanks to impressive performance and long battery life. The new Ryzen mobile chips are a legit alternative to Intel.

Microsoft pushes new Edge browser to Windows 8 and the unsupported Windows 7
Having already started to push the Chromium-based version of Edge to Windows 10 users, Microsoft is now doing the same for older versions of Windows.
With the KB4567409 update, Microsoft is bringing the new version of Edge not only to people who are still using Windows 8.1, but also those who are still on Windows 7 -- which is interesting because Windows 7 is no longer supported.

The hidden value of historic communications in email security
Very rarely in life is certainty guaranteed. Almost every decision we make is made imperfectly, without complete knowledge and based on a gut-checked risk assessment. When it comes to protecting your organization from phishing attacks, this still rings true. Yet, most email security providers still see through a black-and-white lens and act in terms of absolute certainty. As a result, they effectively protect against the known bad, but let unfamiliar threats slip right through.
Employees at every level of your company are making hundreds of email decisions every day -- open this, delete that, respond to this, leave that for tomorrow. With so much inbox noise, a potential phishing email can infiltrate easily -- and can impact an entire organization profoundly.

Cloud computing in Europe: Speculations on EU cloud tech in post-pandemic era
We see the European market today as the hottest area of the global cloud in a pivotal moment. While US cloud giants battle for world domination, China is building its "Great Cloud," Russia is testing its sovereign internet, and Europe is busy creating its own digital sovereignty.
The EU recently declared a massive digital transformation for its economy in the next decade where cloud and AI technologies will play an essential role. So what exactly can we expect from the European cloud industry in the short term?
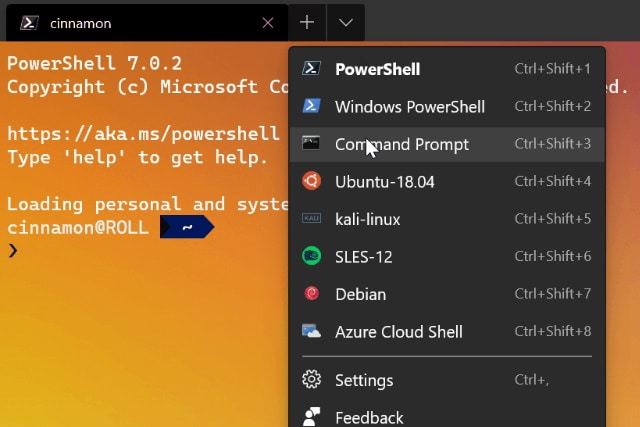
Microsoft releases Windows Terminal Preview 1.1 and it's packed with new features
It's only a month since Microsoft released the first completed version of Windows Terminal and just a week since the company published its roadmap for Terminal 2.0. Starting the journey towards version 2, a preview version Windows Terminal 1.1 is now available.
While this is only a x.1 version increase, Microsoft has actually added quite a lot to the utility with this update. In keeping with Microsoft's release schedule, assuming no problems crop up, all of the features found in this preview release will migrate to the main release version next month. So what is there to look forward to? Highlights include the ability to rename tabs, and support for a new batch of command line arguments.
Best Windows 10 apps this week
Three-hundred-and-ninety-one in a series. Welcome to this week's overview of the best apps, games and extensions released for Windows 10 on the Microsoft Store in the past seven days.
Microsoft's latest feature update for Windows 10, Windows 10 version 2004, has quite a few bugs. The company announced plans to change the names of the Windows Insider channels from "ring" to "channel" to better reflect the expected release quality of each channel.

Australian government targeted by 'state-sponsored' cyber attacks
Australia's Prime Minister, Scott Morrison says the country's government and institutions are being targeted by sophisticated cyber attacks.
The attacks are said to be against all levels of governments as well as services and businesses. Although identified as a state-based attack there is no official comment on who might be behind it. Morrison says it's believed to be a state attack, "...because of the scale and nature of the targeting and the trade craft used."

Microsoft issues another (potentially problematic) fix for printer problems in Windows 10
Two recent updates for Windows 10 introduced printer problems for some users. After investigating the issues caused by KB4560960 and KB4557957, the company issued an out-of-band update for some versions of Windows 10.
Now the company has issued another update for the problem, this time for people who have Windows 10 version 2004 -- or Window 10 May 2020 Update. While this patch may fix printing problems, Microsoft warns that it may introduce problems of its own.

Facebook removes Nazi Trump ads while Twitter flags up 'racist baby' tweet
The Trump administration has been dealt a double blow on social media after Twitter flagged a tweet from the president as "manipulated media" and Facebook remove election ads that featured a Nazi symbol and called for Antifa to be declared a terrorist organization.
On Twitter, Trump retweeted a video labelled as depicting a "racist baby" and made to look like a CNN news clip. In the case of Facebook, an ad that violated the company's policies against organized hate was taken down.

Firefox Private Network VPN renamed to Mozilla VPN and priced at $5 per month
VPNs can be wonderful for protecting a user's privacy, but they are not infallible. For instance, while they can hide your activity from your ISP or an unsecured Wi-Fi network, the VPN company can potentially see everything you do. With that said, you'd better be very smart about selecting a VPN provider. Rule number one: Never trust a "free" VPN or one that offers a pay-once "lifetime" subscription, as you simply can't trust their business models to protect your privacy. Instead, splurge a bit and go with a reputable company that requires periodic payments and promises not to keep any logs. Do your homework, folks.
Mozilla is a company that I trust more than some others (I trust no person or company 100 percent, however!) thanks to its respectable data privacy principles. That is why I surf the web with Firefox whenever I can. That company has been beta-testing a VPN service of its own called "Firefox Private Network VPN". Yeah, that name stinks as it is too wordy. Thankfully, the company has wisely decided to rename it to the much cleaner "Mozilla VPN." In addition, we learn how much the VPN service will eventually cost -- $4.99 a month.



