
How to thwart spear phishing attacks
Many of the recent, large data breaches such as Target, Anthem, and Sony started with a sophisticated spear phishing attack: an email targeted at specific individuals within a corporation that is engineered to look legitimate and fool even tech-savvy users. The email either has a malware-laced attachment or a malicious link that when opened installs malware in order to attempt to gain system access and steal data.
Unfortunately, since stealing data is lucrative nowadays, these spear phishing attacks are often very sophisticated and hard to spot since they have been composed with considerable effort and target only a small number of individuals. The emails look legitimate so regular spam filters cannot identify them and not all anti-malware engines will always be able to detect the malware in the attachment. So what can companies do to protect themselves against spear phishing attacks?

How to choose an operating system for a virtual private server
Internet technologies have penetrated into all areas of our life and changed it dramatically. With their help, people are able to implement most of their activities from reading favorite books and newspapers, communicating with each other, playing online games to booking tickets and buying particular products and services through their desktops, smart phones and tablets. As the number of online users has increased, plenty of different businessmen and even large companies and corporations have decided to move their ventures into Internet to get additional revenues. This technique appeared to be one of the most effective and lucrative, as it allows to find new customer segments and promote business projects in a short period of time.
Currently, the online business environment is full of various websites, which try to attract client's attention by a pleasant look, useful customer services and loyalty programs. However, website owners forget that a significant part of future success depends on a hosting plan they use for their online business activity. The more powerful your server is, the more high-speed and accessible your website will be, what will help you build strong relationships with your visitors for many years to come.

How to get 100GB of free OneDrive storage worldwide
You can easily increase the amount of storage that's available with your OneDrive for free. Bonus space can be unlocked by referring the service to your friends and enabling the auto camera upload feature in the mobile apps. The most that you can get though is 20 GB. Those of us who have been using the service from the early days also get a loyalty bonus of 10 GB. But maybe that's still not enough.
As you may know, Microsoft has recently started to give Bing Rewards users the option to unlock a further 100 GB of free OneDrive storage. The catch? Only folks using the service in US have been welcome. However, now you can get the same treatment worldwide. Here's how.

How to breathe new life into an old PC [Beginner’s guide]
With today’s rapid pace of technological change and consumer-centric culture it’s easy to throw out your laptop or PC as soon as a shinier, flashier model comes along. The problem is: there’s always a faster, more up-to-date version waiting just around the corner.
However, you can save the environment, and your bank balance, from taking any extra strain by following these tips to get some extra life out of an older computer.

Did the NSA spy on you and pass information to GCHQ in the UK? Here's how to find out
It is just about impossible to be an internet user without being aware of the surveillance that has been carried out by the NSA; cheers for the tip, Mr Snowden. While it was the NSA's activities that hit the headlines, governments in other countries used -- and continue to use -- similar surveillance techniques and even share information between each other.
We already know that GCHQ believes that online privacy has never been an absolute right, but this does not change the fact that data sharing between the NSA and GCHQ was illegal before December. Now Privacy International, one of the organizations opposed to such spying, has launched a campaign to help people find out if GCHQ illegally received information about them from the NSA.
How to automatically bypass Windows 10's login screen
Like every version of Windows before it, Windows 10 has its share of standout features, and a few niggles here and there. If you're working with the Technical Preview, you may have seen our earlier guide to removing the desktop watermark. But this is not the only thing that can be irritating, you may be frustrated by the requirement to enter your password to login every time you power up.
As with previous versions of Windows, you can configure Windows 10 so that you are logged into your account automatically. This is great if you are the only person using your computer as it shaves valuable seconds off the startup process. If you're sick of typing your password, here's how to bypass Windows 10's login screen and log into your account automatically.
How to remove the build number watermark from Windows 10's desktop
Hundreds of thousands of people around the world are currently running Windows 10 Technical Preview ahead of the official launch. While it's fun to try out a pre-release of the upcoming operating system it does mean having to put up with a few problems here and there, as well as the occasional niggle.
One thing that irks many Technical Preview users is the fact that the current build number is emblazoned on the desktop. It doesn’t really get in the way, but it looks kind of ugly. If you'd like to get rid of this unsightly watermark, there's no need to tinker with the registry or hack files by hand -- there's a nifty tool that will take care of it for you.
![Doxing: what it is, and how to avoid it happening to you [infographic]](https://betanews.com/wp-content/uploads/2015/01/what_is_doxing.jpg)
Doxing: what it is, and how to avoid it happening to you [infographic]
There are many potential dangers to using the internet, and most people are familiar with the idea of identity theft, unauthorized access to online accounts and the like. But there's another hazard which has come to prominence recently: doxing. The idea is not new, having its roots back in the 90s, but there have been numerous high profile cases of celebrities who have fallen victim to "document dropping".
This involves releasing personal information about someone to the internet -- information that could be embarrassing, personally revealing, or something that the victim would just rather keep to themselves. Interestingly, doxing is not necessarily illegal, but that doesn't mean that the ramifications are not far-reaching.

How to remove embarrassing photos from social networks
Sharing photos and videos online has never been easier. Internet access is available practically anywhere and everywhere, and interconnected wearable and portable devices with photo and video recording options are omnipresent.
In such a world, getting the wrong material posted online can become a huge problem, especially for teenagers unaware of the consequences.
How to install Windows 10 January Build (9926) on Oracle VirtualBox
Microsoft has just released the latest build of Windows 10. New features and changes include a more polished Start menu, Cortana on the desktop, new Settings, Photos, Maps and Xbox apps, and the ability to connect to wireless audio and video. As with the previous builds, this is a very early version of the OS, so you wouldn’t be advised to run it as your main operating system, and while you could set it to dual boot, running it in a virtualized environment is probably a more sensible idea.
The process is very simple -- all you need is a copy of Oracle VM VirtualBox and a Windows 10 Technical Preview ISO. Microsoft updated the latter earlier today.
How to disable Google Chrome's profile switcher button
If you've joined the beta channel for Google Chrome you'll have seen the browser's profile switcher some time ago. For anyone who has decided to stick with the stable channel it may just have appeared. But what's the point? Nestling in the upper right hand corner of the browser window next to your tabs, you'll see a button with your name on it.
This is not to serve as a name reminder to the forgetful, but to show which Chrome profile you’re signed into. If you've set up more than one profile you can use the menu to switch between them with ease, but if -- like most people -- you only use one, it's a waste of space and looks rather ugly. Here's how to remove the pesky profile switcher button from Chrome.

Here's how to smuggle 94 iPhones into China (not)
A man has been arrested for attempting to smuggle 94 iPhones into China by strapping all of them to his body.
Custom officers at Futian Port on the Chinese border were alerted to some suspicious activity when they noticed that the individual had a "weird walking posture, joint stiffness and muscle tension".
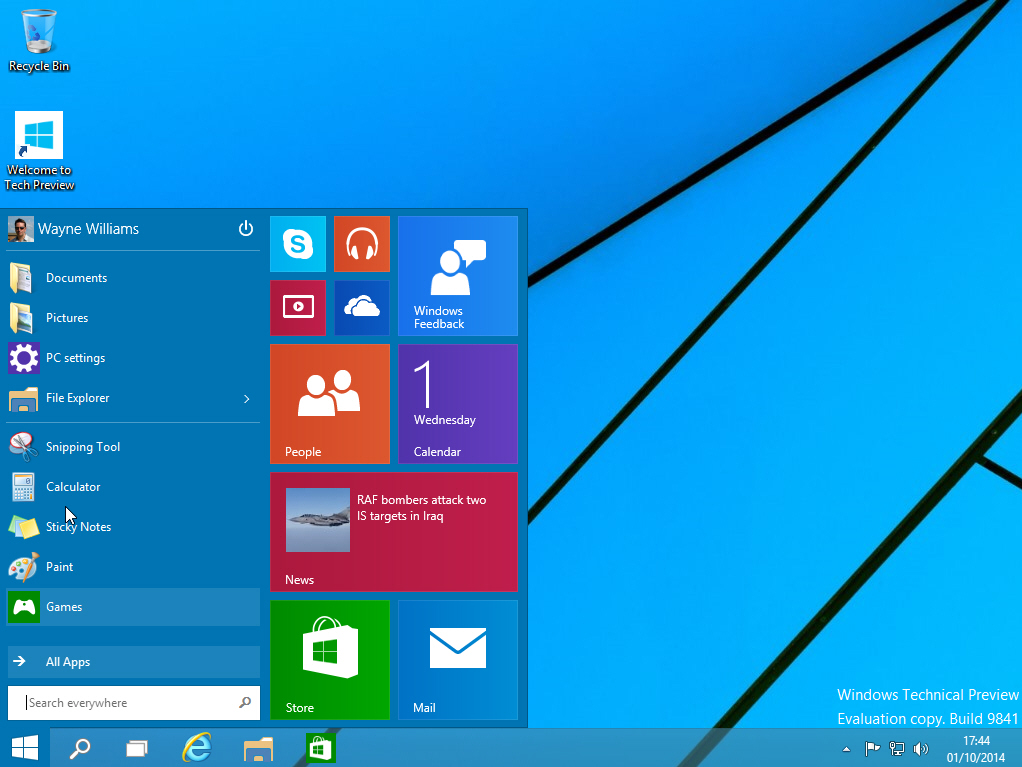
How to install Windows 10 Insider Preview on Oracle VirtualBox
Microsoft has just released the Technical Preview of Windows 10. It’s a very early build, so you wouldn’t be advised to run it as your main operating system, and while you could set it to dual boot, running it in a virtualized environment is probably a better idea.
The process is very simple -- all you need is a copy of Oracle VM VirtualBox and the Windows 10 Technical Preview ISO.

How to design wearables that consumers actually want
What new wearable devices will be unveiled in 2015? As I write, developers and designers are hunkered down building the next generation of gadgets. It’s an exciting time with the wearables market still at its infancy, yet poised for tremendous growth -- with the value expected to hit $12.6 billion by 2018 according to Business Insider. The big question is: which devices and apps will have staying power?
We’ve seen a slew of wearables launched over the past 18 months promising to transform how we live. From smart watches to smart glasses, the development game is on to see just how intelligent these devices can be.

How to use Microsoft's recovery images for Surface and Surface Pro
If you're thinking of starting afresh with your Surface or Surface Pro in the New Year, Microsoft just made your life a little easier. The company has just released a series of recovery images for Surface devices that can be downloaded and used to restore the Windows tablet to the state it was in when you first bought it.
As this restore feature is something that's built in by default, you might be wondering what the value of these recovery images is. Well, there's always the possibility that your existing recovery image is corrupt, or you may even have freed up some space by wiping it out. Now you can get it back.
