
How to check if your Facebook data was shared with Cambridge Analytica
The Cambridge Analytica data scandal has rocked Facebook, and users have been left wondering whether or not their personal data was involved. The social network said that it would be notifying people if they had been affected, but it is also possible to manually check.
Facebook has set up a help page that can be used to determine whether your personal data was shared with Cambridge Analytica, and you can check this if you have not yet seen a notification in your news feed.

Privacy: Avast launches Chromium-based Secure Browser
The far-reaching tentacles of the likes of Google and Facebook have focused people's attention on online privacy, but for anyone looking to retain a modicum of confidentiality it can be hard to know what to do. There are VPN tools, but these are not for everyone, for anyone looking for a quick solution, Avast Secure Browser could be the answer.
This new Chromium-based browser is billed as being "private, fast, and secure" and it's designed to address the misconceptions many people have about privacy and security online. The browser is a renamed and updated version of SafeZone.

Today Facebook will notify 87 million users that their data was the subject of data breach
Initially thought to affect 50 million accounts, it later transpired that as many as 87 million Facebook users were affected by the Cambridge Analytica data harvesting scandal. Today, the social network is due to send a message to those whose data was involved.
While the bulk of affected users -- around 70 million -- live in the US, there are also significant numbers in Europe, Facebook's message is said to be "detailed" and will appear in news feeds at some point today.

Facebook secretly deleted messages Mark Zuckerberg sent on Messenger
As if trust in Facebook could not drop any further, it has come to light that the social network deleted messages sent by Mark Zuckerberg from the recipients' Messenger inboxes. The deletions only applied to Zuckerberg's messages, leaving the other side of the conversation intact -- a feature not available to the average Messenger user.
Facebook did not operate transparently in deleting the messages, as it made no announcement either publicly, or to those involved in the conversations. When confronted about the matter, Facebook said that the deletions were carried out because of "corporate security".

Privacy: Facebook will roll out GDPR controls to the whole world, not just Europe
Mark Zuckerberg has laid out Facebook's plans for the future in a conference call with reporters. In it, he said that the social network now planned to bring GDPR-style privacy controls to all of its users, not just those in Europe for whom there will soon be a legal obligation to do so. The new legislation grants people more rights to access the data companies store about them, and demand it be deleted.
The Facebook chief had previously said that non-European users would only be getting access to new options that were "in [the] spirit" of GDPR, but the backlash the social network has faced recently with privacy controversies seems to have forced Zuckerberg's hand.

Facebook users in Europe will soon have better privacy protection than those in the US
In a few weeks, privacy is set to improve for Facebook users -- at least this is the case for people in Europe. May 25 sees the implementation of General Data Protection Regulation (GDPR), and it means that European users will have the right to not only request details of the information stored about them, but also the right to demand its deletion.
While this will be a legal obligation within Europe, it would have been the perfect opportunity for Facebook to extend the same rights to its users around the world. But it's not going to. Mark Zuckerberg has confirmed that GDPR-style privacy protection is not going to be extended to the US and other parts of the world.
Facebook launches bulk app removal tool in response to privacy concerns
Facebook has long been embroiled in controversies about privacy, but things have been particularly bad in recent weeks. The Cambridge Analytica scandal has put the spotlight firmly on privacy on the social network and -- having already made its privacy tools more accessible -- Facebook has now created a tool to quickly remove apps from profiles in bulk.
It's a very simple idea, but one that will be warmly welcomed by those who have been concerned about the Facebook apps they have installed, but have felt put off by the idea of doing anything about it because of the arduous nature of tinkering with them one by one.

Grindr was sharing users' location and HIV status with third parties
Last week there was an outcry after it was revealed that it was relatively simple to determine the location of Grindr users because of a security flaw. The company has now also admitted that it shared information from users' profiles with third parties -- specifically the analytics companies Apptimize and Localytics -- including their HIV status.
Grindr was quick to point out that, firstly, the information was sent via HTTPS, secondly, that the data was not sold to the analytics companies (it was provided free of charge) and, thirdly, that the data was public anyway. All three of these points will come as little comfort to Grindr users, but the company has said that it will now stop the practice of sharing HIV-related information.

Apple releases iOS 11.3 with a massive focus on privacy
Ahead of GDPR in Europe, Apple has released iOS 11.3, complete with a selection of privacy-focused tools. But while privacy is at the heart of the release, it is far from being the end of the story.
The recent Facebook scandal has focused attention on privacy, and this is something Apple will be more than happy to capitalize upon, bringing GDPR-prompted tools to the world -- not just Europe. But iOS 11.3 also includes an extensive changelog with a range of fixes and updates.

79 percent of healthcare pros worried about the security of their personal data
According to new research, 79 percent of healthcare professionals say they are concerned about the cyber security of their own healthcare information.
At the same time, 68 percent believe their organizations are doing enough to protect patient privacy and personal information from cyber attackers.

Security issues in gay dating app Grindr exposed users' locations
Two security issues have been discovered in Grindr, the gay dating app, which could reveal the location of users even if they opted to keep this information private. There are concerns that the privacy compromise could lead to harassment of Grindr users.
Trevor Faden created a site called C*ckBlocked (that's the actual name, we're not being prudish and getting out our censorship pens) which was designed to give Grindr users the chance to see who had blocked them. By exploiting a security loophole similar to the one exposed in the recent Facebook/Cambridge Analytica scandal, Faden's site was able to access a wealth of private data including deleted photos and user locations.
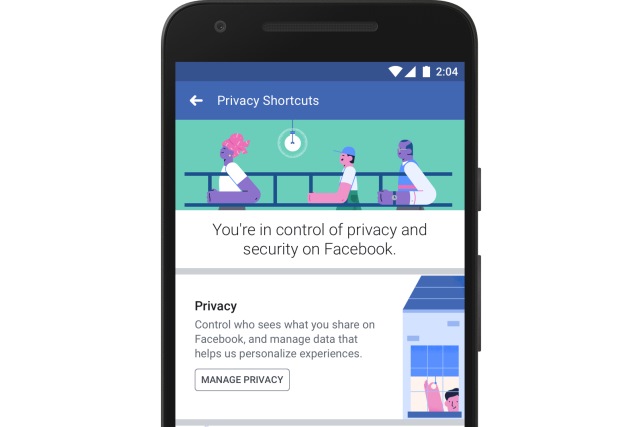
Facebook makes its privacy settings easier to find -- including the option to delete your Facebook data
In the wake of the Cambridge Analytica scandal and revelations about call and text logging, Facebook simply could not have got away with doing nothing. Mark Zuckerberg has hardly prostrated himself in front of users in his various recent interviews, but today Facebook announces a series of changes to privacy settings.
The social network is making it easier to find and use privacy settings, and providing users with information about how to delete the data Facebook stores about them.

Nearly a third of tech workers are ready to #DeleteFacebook
The fallout from the Cambridge Analytica fiasco has done a great deal of damage to not only Facebook's reputation, but also its finances. In the short term, the social network can afford to take a hit on share prices, but in the longer term there is the trust of users to regain.
A survey conducted in the wake of the #DeleteFacebook campaign that followed revelations about the data breach and the logging of Android users' calls and texts, found that a surprising number of tech workers were ready to delete their Facebook accounts. 31 percent backed the #DeleteFacebook campaign, including 50 percent of Microsoft workers, and 38 percent of Google workers.

Mozilla's Facebook Container extension keeps your Firefox browsing isolated from Facebook
Facebook has been completely inescapable in the news over the last couple of weeks, and there are increasing concerns that the social network is all but inescapable online generally. In the wake of recent privacy concerns about Facebook, Mozilla -- already petitioning for Mark Zuckerberg to do more -- has launched a new extension for Firefox that helps to keep your browsing private.
Called "Facebook Container", the add-on has been designed to make it much harder for Facebook to track your web browsing when you're not using the social network.

Mark Zuckerberg refuses to answer UK questions about Facebook privacy
Following the privacy scandal surrounding Cambridge Analytica's use of data from Facebook users, the social network has been under extreme pressure to answer questions from individuals, lawmakers, companies and governments around the world about not only what went wrong, but what will be done to prevent it from happening again.
The British parliament was among those seeking to probe Facebook about the breach of privacy, but Mark Zuckerburg has said that he will not appear before a committee to face questions. Instead, he intends to send either chief technology officer Mike Schroepfer, or chief product officer Chris Cox.
