
Newegg now accepting Bitcoin payments from Canadians
Bitcoin and other cryptocurrencies have experienced monumental rises -- and falls -- over the last year. In other words, it made some folks really rich, but others weren’t so lucky -- depending on the timing of the investment.
If you are still holding onto some Bitcoin, there are plenty of retailers that will accept it as a payment option. Popular computer and accessory seller Newegg even takes it, but only from those in the USA. Today this changes, as the company announces it will now accept Bitcoin from Canadian customers too using the BitPay platform.
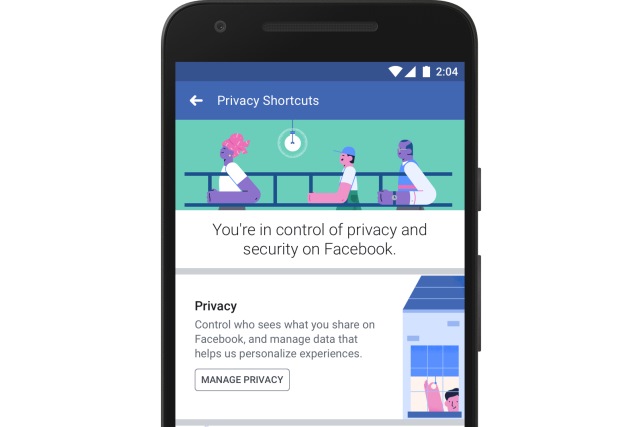
Facebook makes its privacy settings easier to find -- including the option to delete your Facebook data
In the wake of the Cambridge Analytica scandal and revelations about call and text logging, Facebook simply could not have got away with doing nothing. Mark Zuckerberg has hardly prostrated himself in front of users in his various recent interviews, but today Facebook announces a series of changes to privacy settings.
The social network is making it easier to find and use privacy settings, and providing users with information about how to delete the data Facebook stores about them.

More than half of organizations suffer mobile attacks
Over half (57 percent) of organizations suspect their mobile workers have been hacked, or caused a mobile security issue, in the last 12 months according to a new study.
The study by mobile connectivity specialist iPass shows that public Wi-Fi is the most common source of incidents, with 81 percent of respondents saying they had seen Wi-Fi related security incidents in the last year.

Logitech G PRO Gaming Headset is ready for PC, PlayStation 4, Xbox One, and Switch
Playing games online with other people is all the rage these days, and with that comes voice-based trash-talking. Insults over voice chat has become a huge part of the online gaming experience. The best way to participate in such behavior is with a gaming headset. Negativity aside, a headset can also help you to communicate with teammates to plan offenses.
Today, Logitech unveils its latest such product -- the G PRO Gaming Headset. This headset is designed for both professional eSports players and amateur gamers alike. Despite its professional branding, it is surprisingly affordable. The microphone is removable, which is great for privacy, but also lets the headset be used just as headphones so you won't look dorky wearing them out of the house. Logitech is even including replaceable faux suede leather earpads in case you don't like the more traditional "leatherette" pads.

Meltdown patches from Microsoft made Windows 7 and Windows Server 2008 less secure
If you're running Windows 7 and you've not yet installed the March updates, now is very much the time to do so. It turns out that the Meltdown patches released in January and February actually opened up a security hole in both Windows 7 and Windows Server 2008 R2.
A Swedish security researcher found that the patches changed access permissions for kernel memory, making it possible for anyone to read from and write to user processes, gain admin rights and modify data in memory.

This is the OnePlus 6
With the OnePlus 5T now officially out of stock -- and not being replenished -- in the US, coupled with the time of year, it should come as little surprise that there's a new OnePlus handset around the corner.
There have been various rumors about the OnePlus 6 over the last few months, and now serial leaker Evan Blass gives us our first glimpse at what the phone actually looks like. There are two questions that many people will have: does it have an iPhone X-style notch, and does it have a headphone jack? The leaked photo goes some way to answering them. (Update: there is now an official image of the OnePlus 6 available.)

Google buys Tenor -- the animated GIF service, not Luciano Pavarotti
Google is a rather innovative company. Sometimes it creates excellent products and services in-house, and other times, it uses its billions of dollars to buy other companies. In other words, it isn't a stranger to bolstering its portfolio through acquisition. For instance, the search giant bought Nest, giving it a jump-start in the smart home market.
Today, Google announces its latest acquisition -- Tenor. Wait, did Google buy the deceased Luciano Pavarotti? No, it didn't buy a tenor, it bought the Tenor -- the animated GIF hosting service. If you are not familiar, Tenor is a service that allows users to search for and insert GIFs. It is a great way to enhance text-based communications -- arguably superior to emoji.

Universal Media Server 7 adds Movies and TV Show library options, improves scanning performance
The Universal Media Server Project has released Universal Media Server 7.0.0, a major new release of its open-source, cross-platform media server for Windows, Mac and Linux computers.
The server, which works with a wide range of UPNP/DLNA-compatible devices from mobiles to smart TVs, adds support for filtering content into movie and TV show libraries. It also promises massively improved folder-scanning times along with quicker browsing of Media Folders.

Logitech Crayon and Rugged Combo 2 enhance the iPad (2018) experience
Today is a huge day for Apple fans — a new iPad! The company's latest tablet is extremely affordable at $329, and schools can get a $30 discount, bringing the price to just $299.
What makes this low-cost education-focused iPad so special is its Apple Pencil support -- something that was previously limited to "Pro" iPad devices. The problem? The Apple Pencil can be a bit too difficult for small hands to manage. To solve for this, Logitech has created the "Crayon" -- a writing device that is compatible with the new iPad. Best of all, it is more affordable than Apple’s offering at just $49.99!

Google Play Movies & TV now lets you search for shows across a range of streaming apps
There are so many streaming apps and services to choose from, it can be hard to know where to look when you want to watch something. With its latest update to Google Play Movies & TV, Google may just have come up with the answer for Android users.
The update means that when you search for a show within the app, you'll be told which app or service you can use to watch it -- regardless of whether you're a subscriber or not. In all, there's support for over 20 services -- including the likes of Hulu, HBO, ABC and Showtime -- but, for the moment at least, Netflix is not available.

Microsoft releases Windows 10 Spring Creators Update Build 17133 to the Fast ring
We're edging ever closer to the release of the Windows 10 Spring Creators Update, due out next month. It's believed we're at the RTM phase now, but Microsoft will still be issuing updates to Insiders.
Today, Build 17133 arrives for those on the Fast ring, and just like in Build 17128, which came out late last week, it’s missing the watermark at the lower right-hand corner of the desktop. Always a sign that we’re nearly ready for the final release.

Nearly a third of tech workers are ready to #DeleteFacebook
The fallout from the Cambridge Analytica fiasco has done a great deal of damage to not only Facebook's reputation, but also its finances. In the short term, the social network can afford to take a hit on share prices, but in the longer term there is the trust of users to regain.
A survey conducted in the wake of the #DeleteFacebook campaign that followed revelations about the data breach and the logging of Android users' calls and texts, found that a surprising number of tech workers were ready to delete their Facebook accounts. 31 percent backed the #DeleteFacebook campaign, including 50 percent of Microsoft workers, and 38 percent of Google workers.
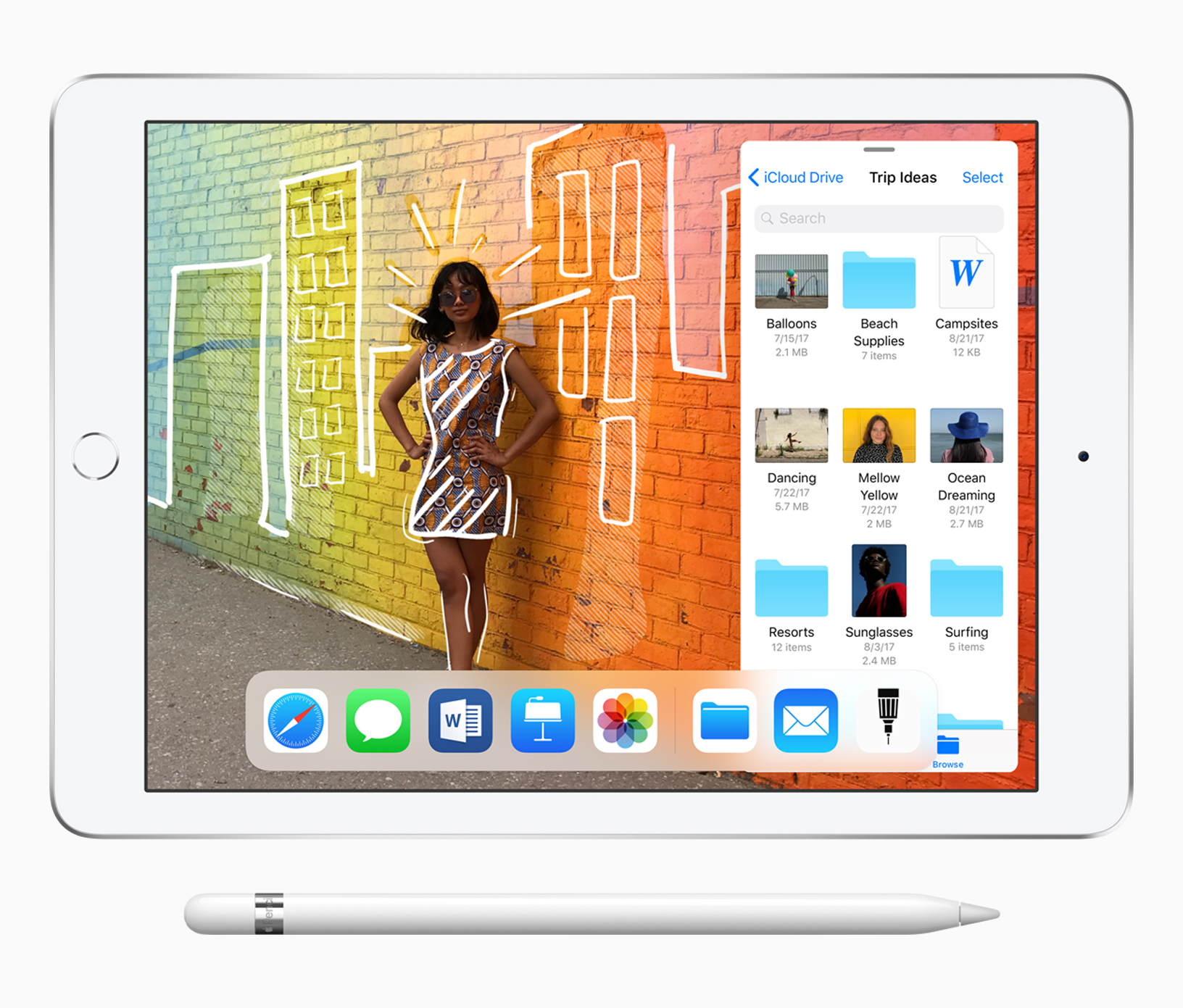
Apple unveils its most affordable iPad yet, with Pencil support
Apple has today been hosting an education-focused event at the Lane Tech College Prep High School in Chicago, and as expected it has taken the wraps off a brand new iPad. The new device is designed to take on Google’s Chromebooks in the classroom, but will no doubt find an appreciative audience outside of the education system.
The new 9.7in iPad, Apple’s most affordable, works with the Apple Pencil, the first non-Pro device to do so. Pages, Keynote, and Numbers have all been updated with Pencil support too.

Intel contributes code to open source edge computing project
The rise of IoT devices is pushing more systems towards an edge computing model in order to handle the data created more effectively.
While several open source projects exist to help solve pieces of the edge puzzle, no single project currently meets the need for a complete edge infrastructure solution.

New asset management platform lets businesses see and secure devices
One of the basic problems businesses face in preventing attacks is effective discovery and identification of their technology assets.
This is made worse by the growth of BYOD and Internet of Things devices. Israel-based Axonius is looking to solve this problem with the launch of its Cybersecurity Asset Management Platform to enable customers to see and secure all their devices.
