
HTC Vive VR gets a significant price cut
Most consumers are either unfamiliar with VR headsets or not interested in owning one. Part of the problem, at least with devices like HTC Vive VR, is the high price, which is hard to justify when we're talking about a technology in its infancy.
However, as the barrier of entry is lowered, VR headsets will become more appealing to a larger number of consumers. HTC is aware of this, which is why it's given the Vive VR a major price cut.

Barclays lets businesses view banking data in real-time
Small businesses struggling to keep track of all their data as they grow have been given a helping hand thanks to a new tool from Barclays.
Designed for SMEs experiencing a surge in growth, SmartBusiness Dashboard offers a place for companies to view all real-time banking data and information about their business in one place.

Intel's new 8th-gen Core processors promise massive performance gains
Intel today unveils a new generation of Core processors, promising a massive performance improvement over the Kaby Lake range announced nearly a year ago.
Just how big of a gain can you expect? Intel says that the 8th-gen Core line is up to 40 percent faster over the previous generation. Compared to a "five-year-old machine," however, the difference is even more substantial, delivering a boost in performance of up to 200 percent.

Get 'Successful Time Management For Dummies, 2nd Edition' ($12 value) FREE for a limited time
If you always feel like there's not enough time in the day to get everything accomplished -- and we certainly do! -- this is the resource that can help change your workday and your life.
Filled with insights into how the most successful people manage distractions, fight procrastination, and optimize their workspace, Successful Time Management For Dummies, 2nd Edition provides an in-depth look at the specific steps you can use to take back those precious hours and minutes to make more of your workday and your leisure time.

How network segmentation can help contain cyber attacks
Cyber crime continues to be a major problem globally and companies are seeking new ways of combating it.
However, there are some older technologies that remain an effective defense. One of these is network segmentation, and network security specialist Tufin Technologies has produced an infographic explaining how segmentation works and how it can help keep organizations secure from today’s sophisticated cyber attacks.

Online abusers face stiffer penalties as social media hate crime will be treated as seriously as face-to-face offenses
Online hate crimes are to be treated as seriously as abuse offenses committed offline as the UK's Crown Prosecution Service (CPS) aims to crack down on abuse and harassment on the likes of Facebook and Twitter. New policies covering hate crime relating to race, religion disability, sexuality -- including, for the first time, specific bisexual hate crimes -- will lead to harsher sentences for offenders.
Alison Saunders, director of public prosecutions, wants to do more to fight online abuse because of the risk of it escalating into the sort of extremist hate seen in relation to events in Charlottesville. She says that abuse of all kind, and on all platforms, should be treated with equal severity.

Data leak exposes 1.8 million US voters' private information
A supplier of US voting machines has confirmed a major data leak that has seen the details of more than 1.8 million voters in the state of Illinois exposed.
The leaked data includes full names, addresses, dates of birth, social security numbers (albeit partial), as well as party affiliations. In some cases even ID numbers and driver license numbers were exposed.

Plex backtracks on controversial privacy policy change
Last week Plex upset a large portion of its userbase by announcing a change to its privacy policy. The change, which was due to take effect in late September, meant that it would not be possible to opt out of data collection.
After a serious backlash, the company has changed its mind, backtracking on the privacy policy update, saying that it recognized the concerns raised by users. The company insists that it was not trying to sneak the policy change by users and that it had no intention of selling data. Importantly, however, users are still going to be able to opt out of playback data collection if they want.

Watch Microsoft's Xbox One X Gamescom presentation here!
Later on today you will be able to learn everything you could possible want to know about the Xbox One X. Microsoft is holding a press conference at Gamescom in Germany and you can watch it here, live.
The presentation kicks off at 12:00PM PT / 3:00PM EST / 8:00PM BT / 9:00PM CET, and Microsoft has already made it clear that pre-order details will be revealed.

Microsoft leaks upcoming Xbox One S Minecraft Limited Edition
At GamesCon later today, we're going to hear about Microsoft's Xbox One X but it's looking as though there's also going to be some news about the Xbox One S.
Microsoft accidentally -- probably -- posted about an Xbox One S Minecraft Limited Edition on the Minecraft Facebook page. The video included a link to the pre-order page for the console.

Amazon hands out $5 credits after accidentally making Echo Dot available free of charge
Anyone shopping for an Amazon Echo Dot a couple of days ago may have spotted that the online retail giant was making its second-generation assistant available free of charge.
But the old adage "if it seems too good to be true, it probably is" turned out to be completely accurate. The $49.99 "Audible Promo" discount that led to the device being reduced in price to $0 was a SNAFU -- but Amazon is going to make up for it.

Plex updates its privacy policy -- and now you can't opt out of data collection [UPDATED]
Plex -- the much-loved media server software -- has updated its privacy policy, and people are not happy with the changes. Included among the changes is a notification that future features may collect and share details about what you're streaming.
Usage statistics are collected by many companies -- including Plex -- to improve products; moving forward users will not be able to opt out of this data collection. Needless to say, Plex users are more than a little upset.

Facebook will protect your privacy... when you're dead
Facebook won't -- usually -- hand over your private messages to anyone after you die. The social network has used a new blogging series called Hard Questions to reveal just how it handles deaths of its users.
The site's director of global policy management, Monika Bickert, says that Facebook aims to not only be sensitive, but also to respect the wishes of the deceased. After death, accounts are memorialized by default, but everyone is also free to create a "legacy contact" who will be able to mange their account in the event of their death. But Facebook is, it says, also keen to protect the privacy of survivors.
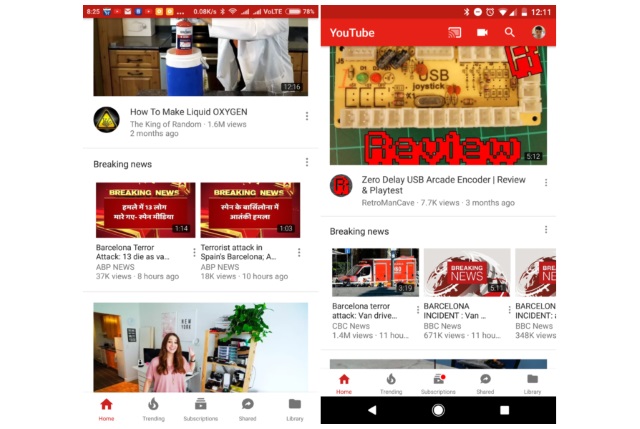
YouTube introduces a breaking news section
To make it easier for people to access up to date information about what is going on the world, YouTube is adding a "Breaking News" section to its website and mobile apps.
The new section takes the form of an additional video carousel, and it provides access to new stories from a number of sources. At the moment, not all users are seeing the Breaking News carousel, and Google has not made an official announcement about it, but it does seem to be spreading out at the moment.

Hackers share HBO social media passwords and threaten to leak Game of Thrones S07E07
A few days ago, HBO's latest humiliation was to have its social media accounts taken over by hackers, and the bad news just keeps on coming for the network. The "Mr Smith group" behind the huge data breach that has seen endless Game of Thrones leaks contacted Mashable with the login details for many HBO social media accounts.
On top of this, the group is also threatening to release Game of Thrones S07E07 -- but considering the number of episodes that have leaked from this season, this was to be expected.



