
TCL's eye-friendly NXTPAPER 11 Android tablet now available for purchase
In an era where digital screens are as ubiquitous as the air we breathe, TCL Mobile is stepping up with a compelling proposition -- a tablet that's easy on the eyes without sacrificing performance. Enter the NXTPAPER 11, now hitting the digital shelves of TCL.com at a wallet-friendly $229.99.
TCL's NXTPAPER technology isn't just another incremental upgrade; it's a thoughtful response to our ever-increasing screen time. The NXTPAPER 11 tablet significantly cuts down harmful blue light exposure by up to 61 percent, a boon for the digital workforce and binge-watchers alike. With a matte finish and textured surface, this device ditches the glossy sheen of traditional tablets for an e-reader-like experience that's less taxing on the eyes.

IT pros worry about Kubernetes security
A new survey of 800 security and IT leaders from large organizations shows 76 percent of security and IT pros believe we are heading towards a cloud reckoning in terms of costs and security.
The study from Venafi finds that 84 percent believe Kubernetes will soon be the main platform used to develop all applications. But, three-quarters worry that the speed and complexity of Kubernetes and containers is creating new security blind spots.

Building an effective and insurable IoT security policy [Q&A]
As businesses look to manage their cybersecurity risk, many have turned to insurance to cover the financial implications of a successful breach.
However, insurers naturally want to limit their own exposure to risk and the small print of the policy may limit some claims. In particular this can apply to IoT devices which represent a major unprotected attack surface in corporate networks.

Get 'Sort Your Career Out: And Make More Money' (worth $14) for FREE
The best investment you can make is in yourself and your career.
Sort Your Career Out is your go-to guide for building a career that you love. Dream jobs don't just come along: you need to make them happen. And this is the book that will show you how, from creating the ultimate career strategy to getting paid what you're really worth. (Hint: It's not just about changing the font on your resume!)
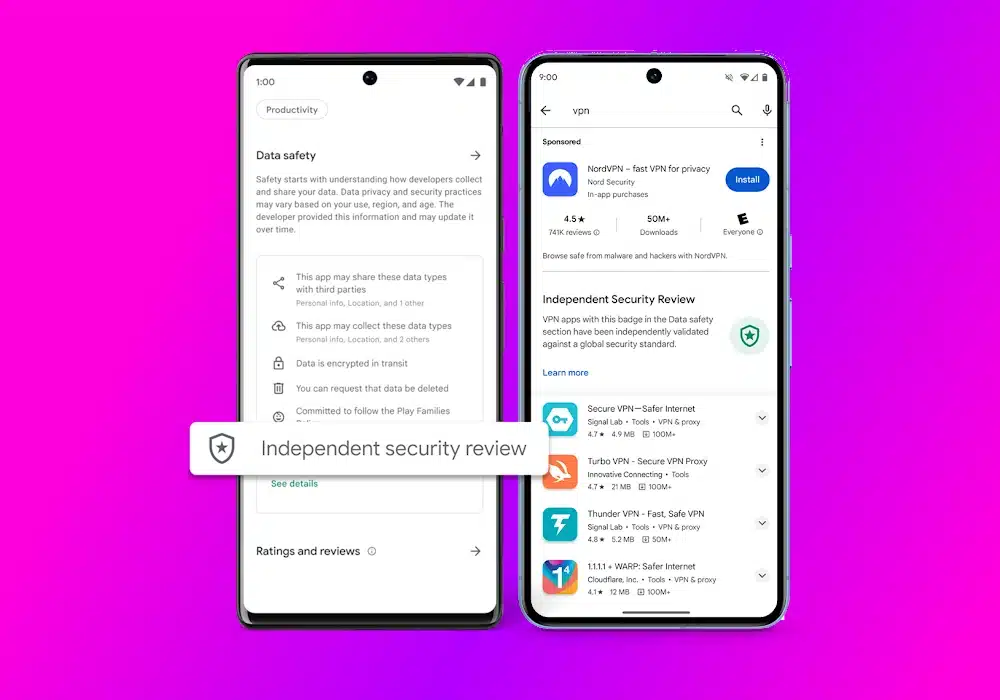
Google has a quixotic plan to make it easier to choose a safe and reliable VPN
If you're in the market for a VPN, you're not short of choice. In fact the sheer number of VPN apps out there can be quite overwhelming, and it's a situation that is hardly improved by the existence of a seemingly endless number of fake tools.
So Google has come up with something of a solution -- albeit one that is only going to be of help to Android users. The company is looking to make Google Play a safer place to inhabit, and as part of this it is going to be highlighting VPN apps that have been independently audited so users know they can be trusted. The likes of NordVPN, Express VPN and Google's own Google One are among the first to get the seal of approval.

Microsoft is killing off three Windows services because of security concerns
It is usually the case that new versions of Windows see the arrival of new features and options, but Microsoft is also known to take things away. This month, Microsoft has taken the decision to deprecate three features and services, including WebDAV, in Windows 10 and Windows 11.
Also for the chop are the Remote Mailslots protocol and the Computer Browser service. The reason for killing off the trio is security, with age meaning that there are now far better options available.
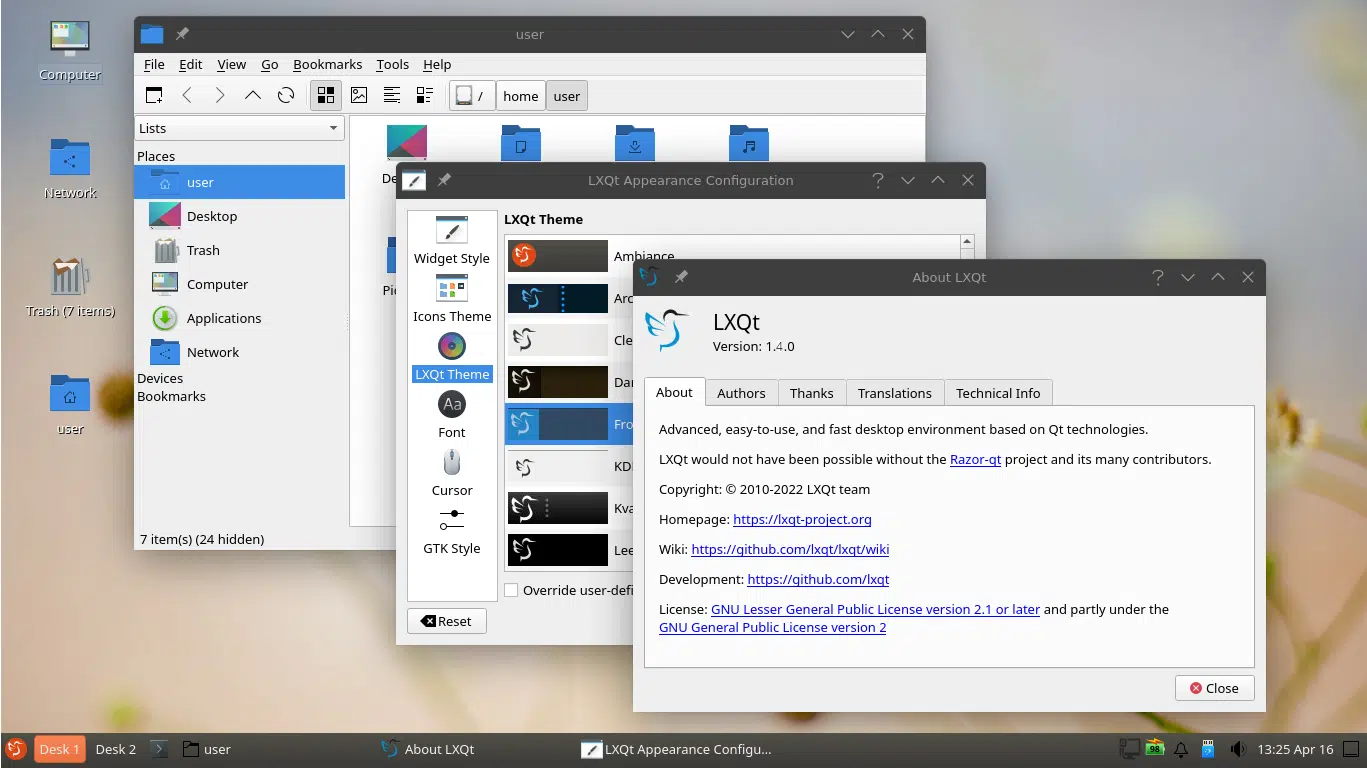
LXQt 1.4.0 lightweight Qt Linux desktop environment is here
The LXQt team has officially unveiled LXQt 1.4.0, marking a significant step forward for the “Lightweight Qt Desktop Environment.” This release underscores the team's commitment to providing a sleek yet powerful user interface.
At the heart of this release is the transition to Qt 5.15, the final Long-Term Support (LTS) version of Qt5. This change sets the foundation for the upcoming journey towards Qt6, with the LXQt team expressing a robust resolve to embrace Qt6 in the subsequent release, even if it necessitates a delay.
Three ways AI is changing the private equity game
Financial market participants, including banks, insurance companies, pension funds, and hedge funds, are all actively exploring ways to leverage artificial intelligence (AI), and private equity (PE) firms are no exception.
Three areas that are showing a significant return on investment (ROI) for AI among PE firms are deal flow, investment pre-screening, and risk intelligence, because it’s these areas where AI is helping them shift their window to act earlier than their peers. The private companies that PE firms invest in are simply far less transparent than public ones: There’s just not as much information about them, and the information that exists is generally much harder to get.

Three E-signature adoption trends that may surprise you
It’s well documented that the pandemic supercharged digital transformation speeds for countless organizations and disrupted how we work, live, and transact.
In the shift from ink to e-signatures across industries, I have witnessed three important yet somewhat under-the-radar adoption trends that support the recent IDC findings that 86 percent of IT decision-makers say that they have invested in e-signature software in the past year and 85 percent plan to do so in the next 12-18 months.

Get 'SAFe for DevOps Practitioners' (worth $37.99) for FREE
Product development and release faces overlapping challenges due to the combined pressure of delivering high-quality products in shorter time-to-market cycles, along with maintaining proper operation and ensuring security in a complex high-tech environment.
This calls for new ways of overcoming these challenges from design to development, to release, and beyond. SAFe for DevOps Practitioners helps you use a DevOps approach with the Scaled Agile Framework and details how value streams help you resolve these challenges using examples and use cases.

Delayed: Windows 11 23H2 is not available via the Media Creation Tool because Microsoft is busy with 'size optimization'
Microsoft recently made Windows 11 23H2 available to those who are willing to seek it out, with an automatic roll out due shortly. The company has also released Windows 11 23H2 (or Windows 11 2023 Update) as an ISO image so it is possible to create installation media manually.
But for anyone who has been hoping to use Microsoft's Media Creation Tool to create installation media automatically is in for some disappointment. The availability of Windows 11 23H2 though this route has been delayed.

Transcend unveils 5600MT/s DDR5 memory
Transcend has unveiled its new series of industrial-grade DDR5 5600 DRAM modules, which will soon be available for purchase here. Aligning with JEDEC standards, these advanced modules are packed with essential features like low power consumption, high speeds, minimal latency, and outstanding durability. They are designed to significantly enhance the capabilities of today's data centers, AI servers, network and communication systems, and more.
At the core of Transcend's DDR5 DRAM modules are major-grade DRAM chips, pushing the speed to an impressive up to 5600 MT/s. The design includes two independent 32-bit channels which substantially broaden the bandwidth, leading to improved memory access efficiency and shorter loading times for users. DDR5's standout feature is its low operating voltage of 1.1V, which is instrumental in cutting down overall power wastage. This feature is further enriched by an on-board power management IC (PMIC) that smartly regulates power distribution, enhancing energy conversion and elevating overall energy efficiency.

Leveraging AIOps to keep pace with cloud-native complexity
Companies have massively increased their cloud infrastructure investment in the relentless pursuit of innovation. Cloud-native apps, hybrid clouds, microservices, and serverless all enable companies to serve their customers with greater agility -- and at greater scale -- than ever before.
But the rapid adoption of these technologies has also created distributed cloud environments that are immensely difficult to understand and monitor with conventional observability tools.

Connected cars -- Safety gained or safety lost?
Connected technology is everywhere and influences every part of our lives. On average, there are nine connected devices in every UK household, and according to the UK Department of Culture, Media, and Sport. This is estimated to grow to twenty-four billion connected devices by 2050.
While connected devices provide a range of benefits, there are now growing concerns around the data they are collecting, and the subsequent loss of consumer privacy. One very real example is the recent announcement from the California Privacy Protection Agency (CPPA), which advised that its enforcement division will review the data privacy practices of connected vehicle manufacturers, stating that they are "connected computers on wheels" and should be treated as such.

Introducing Apple Declarative Device Management: A comprehensive guide for Mac administrators
As a Mac administrator, managing a fleet of Apple devices across your organization requires consistent practices and robust security measures. With numerous system services and background tasks to oversee, maintaining uniform configurations and safeguarding organizational data are formidable challenges.
Apple has introduced a powerful new Declarative Device Management (DDM) approach to address these challenges. This update to the Mobile Device Management (MDM) protocol represents a paradigm shift in device management, offering an efficient and secure means of administering macOS devices. DDM enables tamper-resistant configurations and facilitates simplified monitoring of system services and background tasks. Declarative status reports allow administrators to know about a device's current state.


