Mageia 9 Release Candidate 1 (RC1) is shaping the future of Linux

Today, the developers behind Mageia 9 unveil the first release candidate (RC1) of the operating system, marking a significant milestone since the beta 2 release in May. The journey from the beta stage has been nothing short of impressive, as it includes efforts to rectify stubborn issues, roll out vital security fixes, and keep everything updated.
Mageia 9's standout features make it a robust choice for Linux users. Its powerful core built around the Kernel 6.4.3, combined with glib 2.36 and gcc 12.3.0, gives this release candidate a solid foundation. The rpm 4.18.0 packaging system ensures smooth software management.
Twitter could be about to undergo a huge rebrand as Elon Musk signals a desire to drop the bird logo
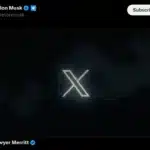
Since Elon Musk's arrival at Twitter, it has been difficult to keep track of the fast-paced changes. The latest signals from the billionaire owner indicate that even more dramatic changes are afoot -- including ditching the Twitter brand and all bird-related imagery.
In a series of tweets, Musk said "soon we shall bid adieu to the twitter brand and, gradually, all the birds". Indicating that the change could happen very quickly indeed, he added: "If a good enough X logo is posted tonight, we’ll make go live worldwide tomorrow".
When putting AI to work, remember: It's just a talented intern

Artificial intelligence (AI) models have been generating a lot of buzz as valuable tools for everything from cutting costs and improving revenues to how they can play an essential role in unified observability.
But for as much value as AI brings to the table, it’s important to remember that AI is the intern on your team. A brilliant intern, for sure -- smart, hard-working and quick as lightning -- but also a little too confident in its opinions, even when it’s completely wrong.
Why content federation represents the next evolution of the CMS

We live in a content economy. There are an estimated 200 million creators on the internet, and upwards of four billion social media users. If organizations want to tap into this burgeoning economy -- set to be worth over $24bn in the next four years -- they must expand their capabilities beyond serving customers basic text and images.
Consumers want connected digital experiences that draw from multiple content sources. However, many organizations risk being held back by their current CMS, as customization and integration challenges slow the creation of new or complex digital services at scale. The result? Innovation happens at the pace that back-end architects and developers want, not the speed the business demands. If organizations are to unlock full value from content, an alternative approach is needed. Enter content federation.
The official ChatGPT app for Android is just days away -- but you can pre-order now!
The popularity of OpenAI's ChatGPT led to a seemingly endless stream of fake mobile apps popping up in Google Play. Now, a couple of months after the official app was released for iOS, ChatGPT for Android is due to land in the coming days.
OpenAI has announced that the Android version of the ChatGPT app is launching in the last week of July, but the company has not revealed a precise date. If you want to be sure to get hold of the app as soon a possible, you can pre-register, and it will be installed the moment it is released.
Solidigm unveils D5-P5336 SSD with top capacity of 61.44TB

Today, we have some exciting news from Solidigm. You see, the company just unveiled its newest PCIe 4.0 x4 NVMe solid state drive -- the D5-P5336. It's not just any storage drive; this baby is a quad-level cell (QLC) SSD, designed especially for data centers.
What's really cool about the D5-P5336 is its epic storage capacity. We're talking starting from 7.68TB and skyrocketing to a mind-blowing 61.44TB! Picture this: you can cram six times more data into the same space compared to those old-school hard disk drive (HDD) arrays. That's some serious cost and space efficiency, right?
Five ways to reshape the customer-centric product development process

Building products quickly to meet customer needs is more important than ever, especially as customer expectations continue to evolve. According to a recent study from Zendesk, 70 percent of consumers spend more with companies that offer fluid, personalized, and seamless customer experiences. For IT leaders, it’s not sufficient to focus on building things as required, their first focus needs to be on building the right thing. This means establishing a customer-centric product development process that supports discovering what customers really need and bringing a valuable product to market that meets their needs.
The most effective way to bring customer-centric products to market is to develop them incrementally and iteratively, with experimentation to discover how to best fulfill customer needs and with fast feedback to improve the quality of the product.
How cybercriminals use ChatGPT for cyberattacks

Artificial intelligence (AI) chatbots like ChatGPT have become a tool for cybercriminals to enhance their phishing email attacks. These chatbots use large datasets of natural language and reinforcement learning to create typo-free and grammatically correct emails, giving the appearance of legitimacy to unsuspecting targets. This has raised concerns among cybersecurity leaders, with 72 percent admitting to being worried about AI being used to craft better phishing emails and campaigns.
Chatbots can help cybercriminals scale the production of advanced social engineering attacks, such as CEO fraud or business email compromise (BEC) attacks. Additionally, cybercriminals may use AI-powered chatbots to scrape personal or financial data from social media, create brand impersonation emails and websites, or even generate code for malware such as ransomware. In particular, without AI, creating malware is a specialized task that requires skilled cybercriminals. However, the use of chatbots could make it easier for non-specialists to do this, and we can also expect AI-generated outputs to improve over time.
Business IT model needs to change to cope with 'workquake'

A pandemic-induced shift to remote work, combined with relentless technological advances such as generative AI, has resulted in a 'workquake', causing a rapidly evolving landscape in which enterprises must adapt to new technologies, working practices, and business models without established procedures.
New research from Doherty Associates identifies a growing complexity avalanche for IT teams. Smaller teams, in particular, report an increase in the breadth and depth of tasks in addition to business-as-usual duties.
Open source supply chain attacks specifically target banking

Researchers at Checkmarx have detected several open-source software supply chain attacks that specifically target the banking sector.
These attacks use advanced techniques, including targeting specific components in web assets of the victim bank by attaching malicious functionalities to them. The attackers employed deceptive tactics such as creating fake LinkedIn profiles to appear credible and customized command and control centers for each target, exploiting legitimate services for illicit activities.
Best Windows apps this week

Five-hundred-and-fifty-two in a series. Welcome to this week's overview of the best apps, games and extensions released for Windows 10 and 11 on the Microsoft Store and elsewhere in the past seven days.
The upcoming Windows 11 version 23H2 feature update will be a smaller update that will install quickly on Windows 11 version 22H2 devices.
How AI and automation have helped adapt to changed customer behavior [Q&A]

We're continuing to feel the effects of the COVID-19 pandemic in many areas, not least in the impact that it’s had on consumer behavior.
In order to cope with the shift in the way that people interact with businesses many have turned to increased automation and use of AI. We spoke to Sateesh Seetharamiah, CEO of enterprise automation specialist Edgeverve, to find out more about these changes and what they mean for the longer term.
Microsoft Office has a brand new look

Microsoft recently unveiled a new default font for Microsoft 365 in the form of Aptos, and now the company has announced that Office is getting a visual refresh with a new default theme for Windows, macOS and Android users.
The theme is gradually rolling out, starting with Microsoft 365 insiders, and it is about more than just a new typeface. With a firm focus on accessibility, the new look means a change of color palette across all Office apps. There are plenty of other visual changes too, including increased line weights and new default styles in Word and Outlook.
Yamaha announces SR-B40A and SR-B30A Dolby Atmos sound bars

Today, Yamaha announces two new devices destined to delight audiophiles. The SR-B40A sound bar with a wireless subwoofer and the SR-B30A sound bar with built-in subwoofers are the newest additions to Yamaha's line of Dolby Atmos sound bars.
"The spike in Dolby Atmos usage, whether it's for movie nights, binge-watching favorite shows, enjoying music, or indulging in gaming sessions, has fundamentally changed the way we perceive home theater systems," states Alex Sadeghian, Director of Consumer Audio at Yamaha Corporation of America. "Our new B40 and B30 sound bars are designed to simplify the process of creating an immersive auditory environment that truly brings Dolby Atmos content to life."
AI solutions for IoT security: How Artificial Intelligence protects low-resource devices

IoT devices are created to perform specific functions, so their technical specs are naturally quite limited. They are unlike smartphones or tablet computers that come with powerful processors and large data storage. Putting traditional security mechanisms like encryption and intrusion detection systems on these devices is impractical. Installing full-fledged security solutions in them is out of the question, let alone AI-powered systems.
However, this does not mean that AI cannot be used to secure IoT devices or entire IoT ecosystems. Here’s a rundown of how AI solutions for IoT are harnessing the benefits of AI to protect IoT and other low-resource devices, including actuators, sensors, wearables, and microcontrollers.
BetaNews, your source for breaking tech news, reviews, and in-depth reporting since 1998.
© 1998-2025 BetaNews, Inc. All Rights Reserved. About Us - Privacy Policy - Cookie Policy - Sitemap.




