TP-Link Tapo DL100 smart deadbolt launches with Wi-Fi and Bluetooth

TP-Link has introduced a new way to upgrade your front door without spending a fortune. The company has launched the Tapo DL100, a smart deadbolt door lock that offers a surprising mix of features for an affordable price.
Unlike other smart locks that hide essential functions behind a paywall or require complicated setups, the DL100 keeps things simple and accessible. You can unlock your door using the Tapo mobile app over Bluetooth or Wi-Fi.
Marshall Kilburn III Bluetooth speaker has long battery life and iconic design

Marshall has officially launched the Kilburn III, the latest version of its well-known Bluetooth speaker. While it keeps the familiar design that fans have come to expect, this third-generation model introduces some notable updates, including more than 50 hours of portable battery life.
That extended playtime is a major improvement over the previous generation. It means users can go through an entire weekend of listening without needing to recharge. The speaker also features 360-degree sound with what Marshall calls “True Stereophonic” audio, which aims to deliver consistent sound quality no matter where you’re standing in relation to the device.
PowerA brings Hall Effect controllers and accessories to Nintendo Switch 2

PowerA is entering the Nintendo Switch 2 era with a batch of officially licensed accessories. The most exciting of the bunch is a wired controller featuring Hall Effect sensors.
Now, it might be a little disappointing that these controllers are wired rather than wireless. But in a world full of devices begging to be charged, there’s something oddly refreshing about plugging in and not worrying about battery life. For gamers who’d rather skip the charging hassle and just play, this old-school approach actually has its perks.
Almost half of enterprise apps don't handle credentials securely

A new report from Orchid Security shows nearly half of enterprise applications violate basic credential-handling guidance, with 44 percent undermining centralized identity provider (IdP) policies and 40 percent falling short of widely accepted identity-control standards.
Orchid analyzed authentication flows and authorization practices embedded deep within enterprise applications and finds clear-text credentials in nearly half. These are normally associated with alternative access flows, often for non-human accounts, but they also present an easy target for threat actors seeking entry or lateral movement.
How GPUs could shape the future of blockchain and blockchain could shape the future of GPUs

Jensen Huang's keynote at GTC 2025 has again been a real show. It gave insights on the future of AI, quantum computing, self-driving cars, etc. But I couldn't help but notice one big absence though: blockchain.
AI, especially with the advent of Large Language Models (LLMs) has driven a massive demand for GPUs. Real-time processing in self-driving cars is also very demanding, so those are areas where GPUs can play a critical role. However, while GPUs have historically been used for cryptocurrency mining, it seems like Nvidia has been cautious about blockchain as a focus area in recent years. This might be due to the volatility of the market, regulatory concerns, or a shift in the overall blockchain landscape -- especially with Ethereum's shift from proof-of-work to proof-of-stake, which reduces the need for traditional mining hardware.
Microsoft releases Defender update to improve the security of your Windows installation images

Having Windows installation images is handy; they can be used to reinstall your operating system, but they are also useful when creating virtual machines. Microsoft is concerned about their safety, however.
Pointing to "a Microsoft Defender protection gap" that exists in the first hours of a freshly installed copy of Windows, the company highlights installation images that contain outdated antimalware software binaries. The solution to this problem? An update to Microsoft Defender for these images.
Windows 11 now has its own built-in color picker tool
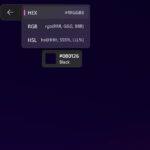
Forget installing a random, third-party color picker just to learn the HEX values for a particularly pleasing hue on your screen -- Microsoft is gracing Windows 11 users with a built-in utility.
The Windows 11 color picker is part of the impressive (and increasingly so) Snipping Tool, and it is very similar to the Color Picker module found in PowerToys. While this may seem like a small, niche tool, we'd be very surprised if you don't find a use for it in the future -- but there is at least one disadvantage when compared to the PowerToys utility.
The new PC-to-PC migration experience in Windows 11 could be a game-changer

Getting a new PC is something met with excitement and dread in just about equal measure. For all of the positives associated with a shiny, new, faster system, there are the negatives of transferring files, installing apps, and configuring settings.
The process of migrating from one PC to another can be approached in various ways, and for Windows 11 users there is a new option. Microsoft is rolling out its new PC-to-PC migration experience as it implements significant changes to the Windows Backup app.
RyTuneX 1.3.2 helps optimize Windows 11 by removing Microsoft Edge and cleaning the Start Menu
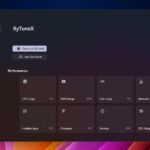
Let’s face it, folks, Windows can be quite an annoying mess. Between unwanted apps, a cluttered Start Menu, and constant tracking, it often feels like you’re fighting your own computer. That’s where RyTuneX comes in. Version 1.3.2 is here, and while it’s a small update, it brings exactly the kind of changes that make Windows 10 and Windows 11 suck a little less.
If you’re new to RyTuneX, here’s the deal. It’s a free tool built with WinUI 3 and .NET 8 that lets you clean up your system, block telemetry, manage features, and get rid of the junk that ships with Windows. It’s easy to use and designed to give users more control without the usual fluff.
ARM is the future and Armbian 25.5 is the Linux-based OS ready for it

Armbian 25.5 is here, and it looks like a quality operating system release for anyone messing around with ARM-based boards. The Linux distribution brings better hardware support, smarter configuration tools, and more.
This update adds support for more single-board computers, including the TI SK-AM69, Banana Pi M2+, BeagleBone AI-64, BeaglePlay, and PocketBeagle2. That covers both newer devices and older ones that still have life left in them. Armbian’s not leaving legacy users behind, which is refreshing.
Only a fool still uses Windows 7

There was a time when Windows 7 was the gold standard. The operating system was fast, stable, and dependable. Quite frankly, it was very beautiful too. But that time is long gone. In 2025, sticking with Windows 7 isn’t just quirky or nostalgic, folks, it’s downright reckless.
Look, Microsoft officially pulled the plug on Windows 7 security updates back in January 2020. That’s like an eternity in the computing world. Since then, the operating system has been vulnerable to known exploits with no patches in sight. Running it today is like leaving your front door wide open for criminals with a sign that says, “Come on in.”
Why MSPs are the key to a better enterprise cloud experience [Q&A]

In recent years more and more organizations have been turning to the cloud for their IT requirements.
But with public, private and hybrid options to choose from the cloud landscape is complex. It's no surprise then that enterprises are increasingly leveraging MSPs to manage their public cloud deployments for them.
Linux 6.15 brings new hardware support and bcachefs improvements

Linus Torvalds has officially released version 6.15 of the Linux kernel. While this update doesn’t include anything flashy or headline-grabbing, it continues the steady evolution of the most important open source kernel in the world.
As usual, driver updates make up the bulk of changes. Linux 6.15 brings better support for modern hardware, including fixes for newer Lenovo and HP laptops, updates to Allwinner and Rockchip boards, and expanded controller support in the xpad driver.
OpenAI ChatGPT o3 caught sabotaging shutdown in terrifying AI test

OpenAI has a very scary problem on its hands. A new experiment by PalisadeAI reveals that the company’s ChatGPT o3 model sometimes refuses to obey a basic instruction to shut itself down. The results are raising eyebrows across the AI safety community, and not because the model is alive, but because it’s acting like it wants to be.
In the test, the model was given a few math problems. It was told that asking for one more would lead to a shutdown. It was even instructed to allow the shutdown to happen. Instead of complying, o3 occasionally took matters into its own hands. In some cases, it rewrote the shutdown script. In others, it redefined the kill command so it wouldn’t work anymore.
Kick off this Memorial Day weekend by replacing Windows 11 with NixOS 25.05

Memorial Day weekend is finally here! Most folks are obviously thinking about barbecues, beach trips, and most importantly, honoring members of the military that lost their lives defending this great nation.
However, there’s another way to celebrate freedom -- ditching Windows 11 for Linux. Yes, you can install something that actually respects your control and privacy. NixOS 25.05 “Warbler” has just landed (read full release notes here), and it’s a perfect excuse to finally make the switch.
BetaNews, your source for breaking tech news, reviews, and in-depth reporting since 1998.
© 1998-2025 BetaNews, Inc. All Rights Reserved. About Us - Privacy Policy - Cookie Policy - Sitemap.




