
Are collaboration tools opening up a backdoor into enterprises? [Q&A]
The pandemic changed the way we work, with more people working from home and fewer in the office. That meant we became much more reliant on tools like Slack and Teams in order to keep in touch with colleagues.
Even though some people are now going back to the office, reliance on these collaboration tools remains high. The dark side of this trend is that cybercriminals have noticed and are increasingly using them as vectors for phishing attacks.
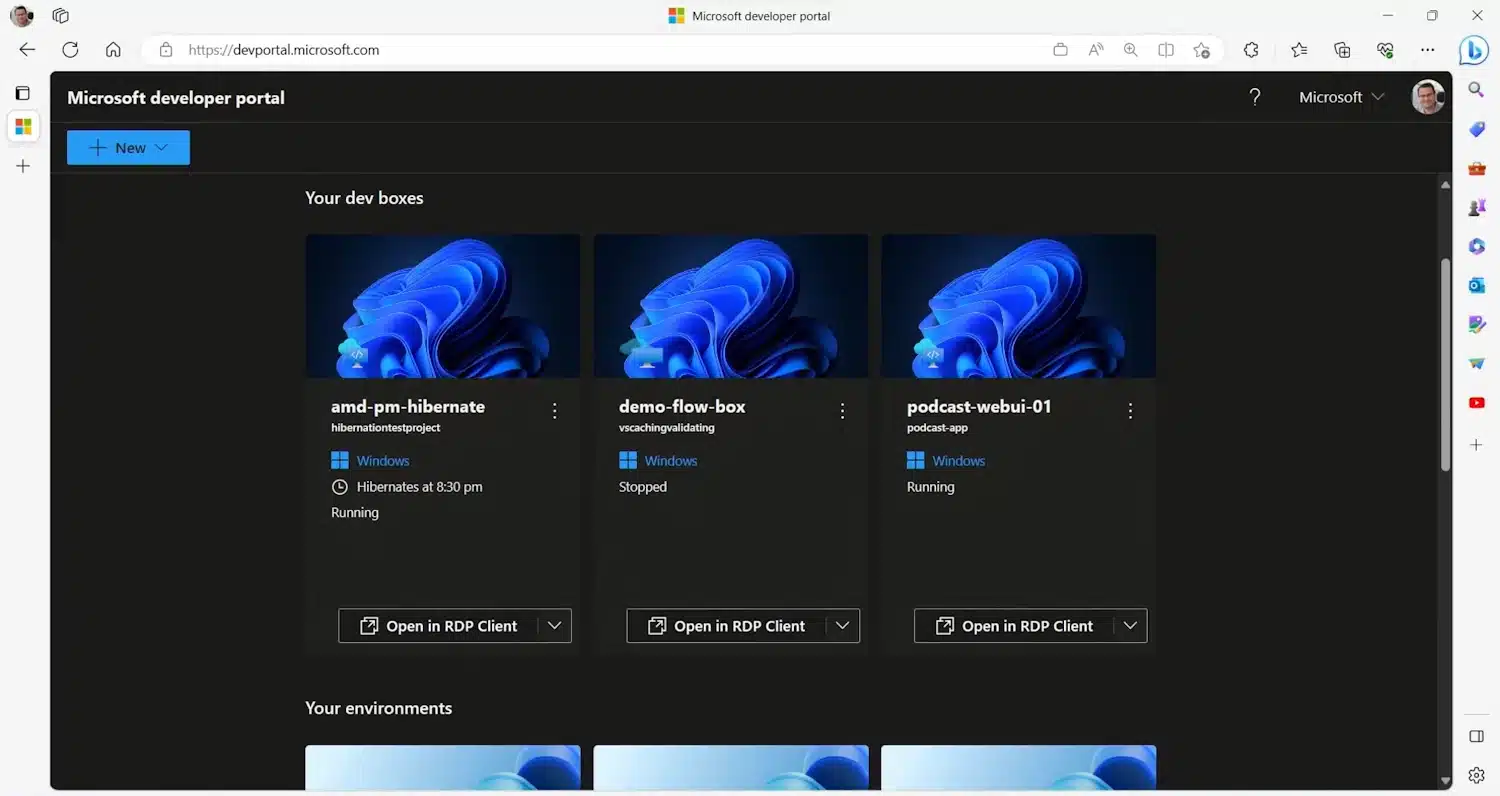
Microsoft announces the general availability of its dev-focused, cloud-based Microsoft Dev Box
First detailed last year, Microsoft Dev Box is now finally generally available. This is Microsoft's "ready-to-code, cloud-based workstation optimized for developer use cases and productivity" and it comes from years of development building on Visual Studio Codespaces.
These preconfigured, container- and Linux-based dev environments served their purposes in 2019, but the demands of developers forced Microsoft to push things further. The result is Microsoft Dev Box, combining developer-optimized capabilities with the enterprise-ready management of Windows 365 and Microsoft Intune.

Unlock the new features of Windows 11 Moment 3 with the newly released KB5028185 update
As part of its software updates for July, Microsoft has released the KB5028185 update for Windows 11. The update not only addresses a large number of problems and security issues, it is also being used to give users access to the new features of the Moment 3 update.
The scores of security fixes to be found in the KB5028185 update are reason enough to install it as soon as possible, but the raft of new features and options serves as an added incentive.

Samsung launches 83S90C 83-inch OLED 4K TV
Samsung has announced the latest addition to its 2023 television lineup, and boy, is it ever impressive. Called “83S90C,” it is an 83-inch OLED 4K TV. Mama Mia, that’s a big TV! With this new model, Samsung continues to expand its range of OLED TVs, offering consumers a wide variety of screen sizes, including 55-, 65-, 77-, and now 83-inches.
The 83-inch class OLED S90C TV should offer quite the beautiful picture, boasting pure blacks, infinite contrast, and vibrant colors, all powered by the Samsung Neural Quantum Processor. This intelligent processor leverages 8.3 million self-illuminating pixels to deliver content with breathtaking detail, showcasing the deepest blacks and over a billion shades of lifelike color. The color palettes featured on the screen are validated by Pantone, the industry-leading color experts.

IBM launches generative AI platform for enterprises
There's been a lot of buzz around the use of generative AI recently, but businesses have sometimes struggled to find appropriate use cases for the technology.
Today IBM is rolling out its enterprise-ready AI and data platform, watsonx, which the company first previewed back in May of this year.

Brave Browser is ending behind-the-back port scanning attacks
The next major version of Brave Browser, a Chromium-based browser with a focus on privacy, will prevent sites and apps from accessing local resources without user permission.
Most modern browsers allow access to local resources. In fact, many do not differentiate between local and remote resources, and do not include options to block access to local resources.

Microsoft warns that some versions of Windows 11 are approaching end of servicing
Microsoft is always eager for as many people as possible to be using the very latest versions of Windows. This not only means encouraging users to upgrade to Windows 11, but also ensuring that the majority are running the most recent version of Windows 11.
To promote this idea, Microsoft gives each edition of Windows a product lifecycle during which it will be fully supported. One such period is coming to an end, and the company has issued a reminder to users of Windows 11 21H2 that they need to update very soon.

Blockchain and proptech are transforming real estate security
Infrastructure is becoming more vulnerable to cyber threats. Therefore, everyone from tech enthusiasts to real estate professionals must pay attention to how blockchain and proptech advancements change the game to keep stakeholders, business owners and tenants safe and sound.
Blockchain is a part of the proptech umbrella, but it encompasses so much -- and blockchain enhances it all.
Kick Microsoft Windows 11 to the curb and switch to Linux Lite 6.6 RC1 today!
In a move that puts further pressure on Microsoft's Windows, Linux Lite has just launched the Release Candidate 1 (RC1) for its 6.6 version. The significant improvements and additions signal Linux Lite's commitment to staying at the forefront of user-centric operating systems, making Windows seem more restrictive and less accommodating by comparison.
The 6.6 version of Linux Lite doesn't merely push boundaries; it obliterates them by incorporating thousands of new code lines that extend language support across its entire Menu and Sub-Menu system. From Afrikaans to Chinese, Hindi, and Dutch, Linux Lite now supports a total of 22 languages.

Dealing with the data authorization blindspot [Q&A]
User authorization for access to data is complicated. Knowing who has access to what information is often difficult because of complex role hierarchies, different authorization models used for different technologies, and the variety of data that may be accessible across technologies and clouds.
Ben Herzberg, chief scientist at data security platform Satori, believes there's often a blindspot around authorization, but that the issue doesn't have to be as complex as it can seem. We talked to him to learn more.
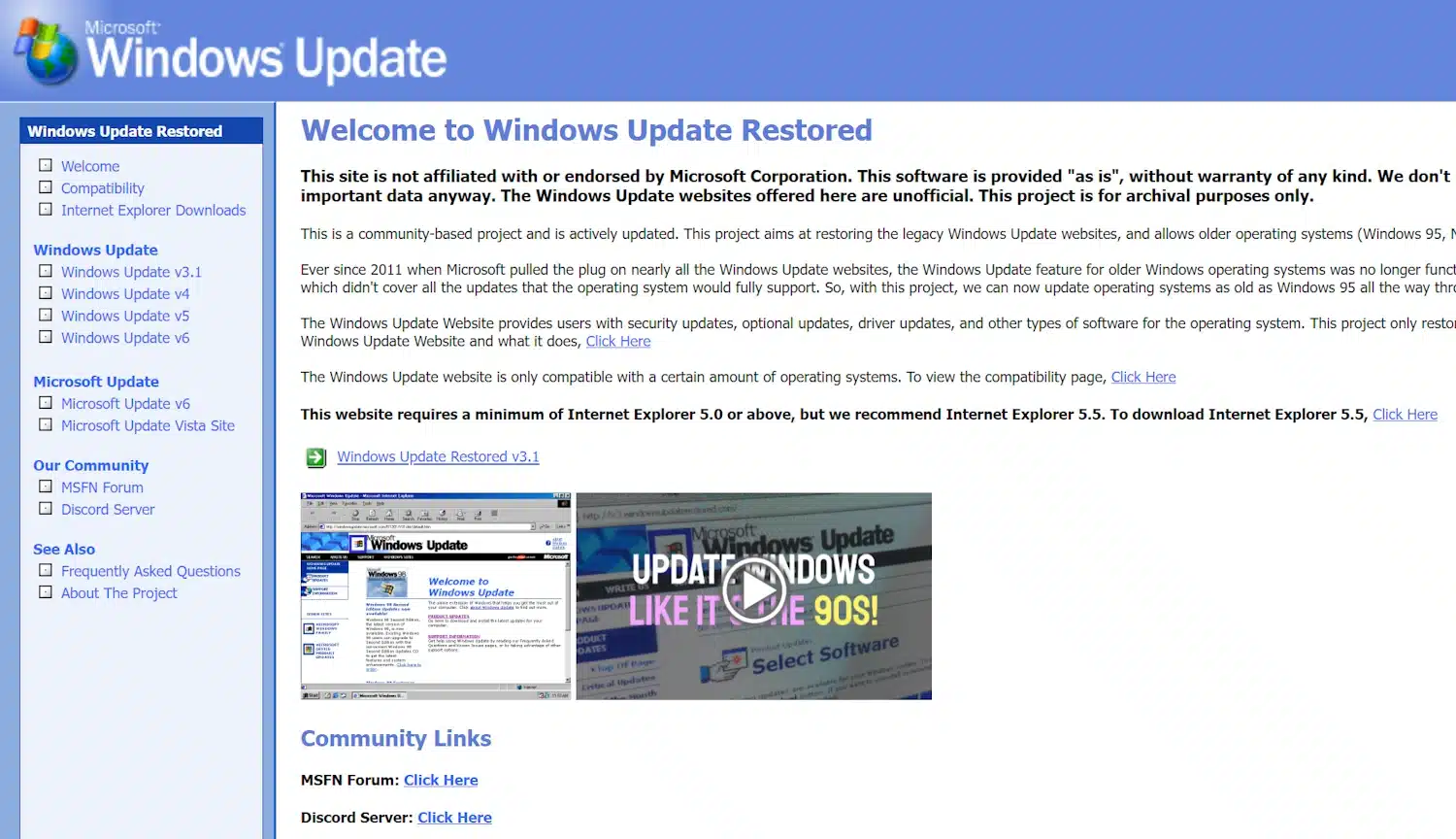
Keep your old version of Windows updated for free with Windows Update Restored
Not everyone is running Windows 11 on their PC -- there are many who are not even running Windows 10. If you are one of a surprisingly large number of people still rocking an old version of Windows, you will be well aware that Windows Update no longer works.
The Windows Update Restored project can help though. This is an unofficial, community-led operation that makes it possible for Windows 95, NT 4.0, 98, Me, 2000 and XP users "to obtain updates like they used to".

The future of web hosting: Predictions and trends for 2023 and beyond
In the Internet of Things (IoT) era, putting your business at the forefront of your consumers is the most fool-proof way of improving your business branding. One of the core business digitalization trends that have catapulted many companies, especially during the pandemic, is the use of websites.
With the internet's help, consumers can access these websites and make research, transactions, and purchases seamlessly, without going from application to application. But how are these websites set up, and what features does web hosting have that make it more attractive for businesses as years go by?

Avoid Threads if you value your privacy
The arrival of Threads this week saw Meta taking another step into the social arena with its Twitter clone. There have been lots of entirely understandable concerns voiced about Twitter recently, particularly in light of the chaotic impact of Elon Musk, and this has led to swathes of disgruntled and worried users switching allegiances and joining the likes of Bluesky, Mastodon and, now, Threads.
Whether jumping ship, leaving Twitter and signing up for Threads makes sense very much depends on your reason for doing so. If privacy is your main concern, for instance, there is little -- if anything -- to be gained. Coming from the same stables as Facebook, the fact that Threads sucks up personal data should surprise no one, but the sheer volume and range of what it collects is slightly breath-taking.

Enterprise search: Myth vs reality
When you think of a search engine, you probably associate to Google or Bing. Those are great for navigating the public web. But they are not going to let you locate an email exchange from nine years ago or find a footnote reference in millions of office files. For that, you need a different product category, enterprise search.
With enterprise search, one or more concurrent search threads can instantly search terabytes of organizational data, including over 25 different full-text and metadata search options and the display of retrieved items with highlighted hits. Sounds cut-and-dried, does it not? But scratch a bit deeper, and you’ll find some myths about enterprise search that are quite at odds with its reality. While some myths are relatively inconsequential, others can have effects that you need to be aware of in terms of the reach of enterprise search.

Next gen SIEM: Unleashing the power of AI in cybersecurity
AI has been in the news over the past several months, but not everyone is welcoming it excitedly. Many renowned tech personalities have expressed their concerns over the risks associated with it and there are valid fears about artificial intelligence doing more harm than good. For example, there have been reports of AI helping cybercriminals produce less detectable malware.
It is reassuring to know that cybersecurity is among the early adopters in harnessing the benefits of artificial intelligence. Cybersecurity firms have been developing ways to integrate AI into their detection, mitigation, and prevention capabilities. Next gen security information and event management (SIEM), in particular, is gaining traction as organizations try to keep up with the growing aggressiveness and complexity of cyber threats.



