
Almost half of employees have access to more data than they need
A new study of over 700 full-time US employees reveals that that 48 percent of employees have access to more company data than they need to perform their jobs, while 12 percent of employees say they have access to all company data.
The survey by business app marketplace GetApp also asked employees what classifications of data protection are in place at their company. No more than a third of businesses were found to use any one individual data classification.

The hard truth about mass shootings and the internet
"You can’t handle the truth!" That iconic line from the 90’s era Tom Cruise legal thriller, A Few Good Men, is what comes to mind as I mull over the headlines of the past few weeks. From El Paso, Texas to Dayton, Ohio, from Gilroy, California to Christchurch, New Zealand, sick and twisted individuals are committing horrendous acts of violence against innocents. And, as I struggle to understand the seemingly disparate motivations of these despicable individuals, a singular thought keeps popping into my head:
This sort of stuff didn’t happen before the internet.
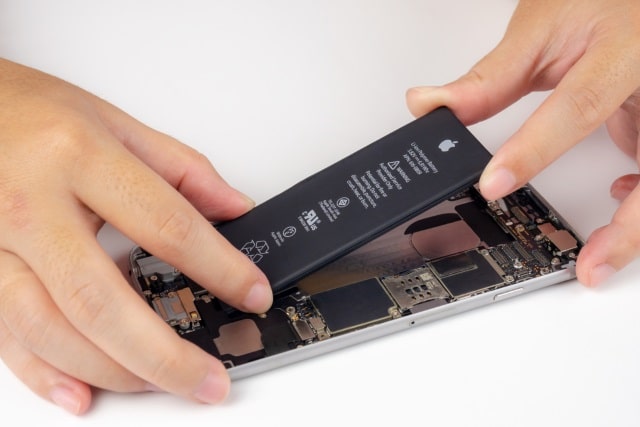
Apple is discouraging the installation of third party batteries by displaying Battery Health warnings
In a move that is going to prove more than a little controversial, Apple is using the Battery Health feature of iOS to strongly discourage people from using cheaper third-party batteries rather than official Apple units.
Now, if you install a non-official battery in an iPhone XS, XR or XS Max, Battery Health will display a "Service" notification that is usually used to indicate that there is a problem. Click through, and you'll see a message that reads: "Unable to verify this iPhone has a genuine Apple battery. Health information not available for this battery".

Load balancer flaw could lead to major breaches at large organizations
A security flaw in the F5 Networks’ BIG-IP load balancer, which is popular among governments, banks, and other large corporations, could be exploited to allow network access.
F-Secure senior security consultant Christoffer Jerkeby has discovered the issue in the Tcl programming language that BIG-IP's iRules (the feature that BIG-IP uses to direct incoming web traffic) are written in. Certain coding practices allow attackers to inject arbitrary Tcl commands, which could be executed in the security context of the target Tcl script.

pdf Creator 9.0 unveils new zipper merge tool, unveils new options for manipulating PDFs
Geek Software GMBH has released pdf24 Creator 9.0, a major new version of its freeware suite of tools designed to create and manipulate PDF files. Features include the ability to merge, split and extract individual pages from PDF files, plus create secure documents.
The program adds several new features, including a zip-like merge tool for PDF documents as well as the ability to quickly reverse a document’s page order. Users also gain a handful of additional options as well as a selection of minor improvements

Satechi launches 72W Type-C PD Car Charger and Apple MFi Certified USB-C to Lightning Cable
If you are a road warrior that spends a lot of time in the car, you know how essential a quality charger can be. Low cost car chargers from little-known manufacturers may work, but not necessarily well. For instance, I have had many cheap chargers die after less than a week of use -- sometimes within a day. Even more often, despite the listed specifications, it can't charge fast enough to maintain battery life during heavy use. In other words, even though my phone is charging, the battery percentage still goes down -- albeit slower than not charging at all.
Ultimately, I learned the hard way, when it comes to chargers, you should always aim for one made by a quality manufacturer. One such company is Satechi, and today, it launches an impressive 72W Type-C PD Car Charger. Don't worry, it also has a USB-A port. In fact, those 72 watts are shared between the two. In addition, the company unveils a new Apple MFi Certified USB-C to Lightning Cable for iPhone and iPad users.

Ransomware turns its sights on large organizations
Detections of ransomware aimed at businesses rose by a massive 363 percent between the second quarter of 2018 and the same period this year. Meanwhile consumer ransomware is down 34 percent.
The latest quarterly threat report from Malwarebytes also sees a 235 percent overall increase in threats aimed at organizations from enterprises to small businesses, with ransomware as a major contributor.

Software producers need more flexible licensing models in order to compete
Once upon a time you bought a license for a piece of software and you could, essentially, run it forever. While much of the market has now shifted to subscription models, 65 percent of producers are still offering perpetual licenses, while 74 percent utilize subscription models for some or all of their products.
A new report from Flexera, which looks at changing licensing and deployment models, finds that when software producers are asked how they will change their monetization models over the next 18 months, both usage and subscription models will see the strongest increases.

IBM launches new toolkit to boost understanding of and trust in AI
AI and machine learning have demonstrated some impressive abilities in recent years, but the models behind the technology and the reasons why it came to the decision it did are often hard for the people interacting with it to understand.
In order to help people gain an insight into machine decision making, IBM Research is launching AI Explainability 360, a comprehensive open source toolkit of state-of-the-art algorithms that support the interpretability and explainability of machine learning models.

Linux Journal shuts down, because cheapskate Linux users don't spend money
Linux users are cheap as hell. Sorry, but it is largely the truth. I am not just talking about traditional Linux desktop users either, but Android users too. This is why iOS is so profitable despite its paltry market share compared to Android. iPhone users will actually buy apps, while Android users would rather look at ads than part with a measly dollar. Sadly, many people only choose Linux because it is free -- not because they prefer it.
And look, that's fine. There's nothing really wrong with being averse to spending money. Quite frankly, not wasting money is a noble trait. However, like it or not, there is no such thing as a free lunch, and that includes open source software. Eventually, when developers can't pay their bills, that free software you love will disappear.

Half of companies won't move mission critical workloads to the cloud
A new report from enterprise file sharing platform FileCloud looks at cloud and data security and finds that 50 percent of companies don’t plan on moving mission critical workloads to the public cloud.
The survey of 150 professionals from industries including health care, financial services and educational institutions finds that shifts in perceptions of data security are impacting movement to the cloud.

Will hackers turn the 787 Dreamliner into a flying nightmare?
Do you like airplanes? I know I do. Get me inside an airport terminal and I become glued to the glass watching them move about on the tarmac. Big ones. Small ones. I love them all.
And not just from the outside. I love traveling in planes, too. In fact, I’ve flown in nearly every type of major short or long-haul jet in service. From humongous A380’s to diminutive MD88’s, I’m a seasoned veteran of the air travel game.

Samsung Galaxy Note10 and Note10+ are powerful, beautiful, and very expensive
Earlier today, Samsung had its big "Unpacked" event in New York, and BetaNews was there to take it all in. As was expected, the Galaxy Note10 was unveiled. Yours truly was in the third row, listening to well-placed Samsung employees loudly "ooh" and "ah" at every little thing shown off on stage. While their feigned enthusiasm was comically overdone, there actually was some exciting stuff revealed, including the removal of the old-school headphone jack -- finally!
This year, there are two new Android 9.0 phones -- Note10 and Note10+. This is the first time a Note smartphone has been offered in more than one screen size. The plus in the name indicates it is the better device, including having a bigger screen. It has a 6.8-inch Dynamic AMOLED Infinity-O display with 3040×1440 resolution, while the non-plus has a 6.3-inch screen with a 2280x1080 resolution. Both are HDR10+ certified.

Microsoft announces Windows 10 20H1 Build 18956 with network and notification improvements
Last week, Microsoft released Build 18950 to Insiders on the Fast ring, and it’s fair to say it wasn’t the most exciting of releases with the headline addition covering Japanese IME improvements.
Today’s new flight, Build 18956, is much more interesting with a redesigned Network Status page, notification settings improvements, and Calculator and Cortana app updates.

3 ways IoT will impact our future
The Internet of Things (IoT) industry is growing rapidly with the number of IoT-connected devices projected to surpass 20 billion by 2020. It’s an amazing number, but a number that wouldn’t be possible without the concurrent growth and availability of WiFi and cellular. However, even with all this growth, industry leaders don’t believe existing WiFi and cellular capabilities can keep up with IoT’s trajectory.
Thankfully, a little innovation called 5G is on the way. Offering the technological boost needed to sustain this growth, the imminent arrival of 5G presents valuable opportunities for IoT. Let’s take a look at where IoT is today, and what the future holds.



