
The changing nature of mobile: App developers versus mobile solution providers
A recent study by Gartner shows that mobile app use grew an incredible 115 percent from 2012 to 2013. Apple, which offers more than a million apps for the iPhone, iPad and iPod touch, said recently that customers spent more than $10 billion on apps in 2013, yet the most popular apps have a distinct difference.
Take the incredibly popular and successful WhatsApp; the five-year old company has over 500 million active monthly users, and the founder signed a $19 billion acquisition deal with Facebook just a few blocks away from the social services office where he used to collect food stamps.

Privacy and financial threats top mobile malware trends
With mobile malware showing a 68 percent increase over the first half of last year it seems that, as with the PC malware field, profit is the main driving force behind it.
New data released by security specialist NQ Mobile shows that infections were detected in 37.5 million Android devices in NQ Mobile's database of 136 million active user accounts worldwide, an increase of 78.6 percent over last year.

One in five businesses loses data to mobile device theft
The results of a new survey from Kaspersky Lab show that the rate of mobile device theft is increasing but over the same period the time taken for IT departments to respond has increased.
Part of this is down to employees taking longer to report mobile loss or theft. Only half report the theft of a mobile device within a day with 38 percent taking up to two days and nine percent waiting between three and five days.

Isis Wallet to become Softcard to avoid ISIS extremism association
When you see the letters ISIS, what is it that you first think of? Is it the Egyptian goddess of health, marriage and love? The Institute for the Scientific Investigation of Sexuality? Or is it the Islamic State of Iraq and Syria, the jihadist group that has been in the news for some time now? It's quite common for there to be unfortunate sharings of names and acronyms, and it's something that Isis Wallet, the NFC payment service, has fallen foul of. To avoid being associated with the Middle East group, the service is being renamed to Softcard.
The rebranding has not come completely out of the blue. Back in July, company CEO Michael Abbott explained: "Recently, we have observed with growing concern a militant group whose name, when translated into English, is Islamic State of Iraq and Syria -- often referenced by the acronym ISIS. We have no interest in sharing a name with a group whose name has become synonymous with violence and our hearts go out to those who are suffering".

Apple's march of the lemmings
So the Apple media invites are out, and I am laughing my ass off at how effectively the company manipulates the Fourth and Fifth Estates and how willing are the lemmings to be led. (I got no invite, by the way, and didn't expect one.)
So what? We've got the same venue where Steve Jobs unveiled the Mac in 1984. Thirty-year anniversary. Check. The hall is considerably larger than the two others more typically used. Check. Add them together and you have a writ-storm of speculation -- and soon purported, unconfirmed leaks -- about something really big coming on September 9th.

California brings in smartphone kill switch legislation to protect handset owners
In California, a bill has been passed that will require smartphone manufacturers to include a kill switch in their handsets. The bill states that "any smartphone, as defined, that is manufactured on or after July 1, 2015, and sold in California after that date, include a technological solution at the time of sale, which may consist of software, hardware, or both software and hardware, that, once initiated and successfully communicated to the smartphone, can render inoperable the essential features, as defined, of the smartphone to an unauthorized user when the smartphone is not in the possession of an authorized user". It's a lengthy description, but it means the kill switch that many people have been asking for for so long is becoming a reality in another state.
This is not the first time a kill switch bill has been passed -- Minnesota did something similar back in May. The SB 926, Leno Smartphones bill in California is rather more far-reaching and comes partly in response to the statistic that between 30 and 40 percent of robberies in major US cities are smartphone robberies. Once activated, the kill switch will prevent a phone from being registered on a wireless network, and cannot be bypassed even with a hard reset. In the event of theft, a user will also be able to remotely wipe their device to protect any private information they may have stored on it.

Enterprise mobility: How to choose the right strategy
Finding the ideal alignment and balance between hardware, software and employee preference has become the Holy Grail for those tasked with defining enterprise mobility strategy. BYOD delivered many great things, such as higher employee productivity and satisfaction. It also made IT managers rethink their strategies to make technology work for their organization in terms of mobility, security and management. Then COPE (corporate owned, personally enabled) came along, which promised to solve some of the problems that BYOD didn't, such as security. However, COPE also posed challenges of its own and is being followed now by CYOD (choose your own device).
With so many acronyms flying about, it might appear hard to know where to start identifying the best solution. However it would seem that 2014 has heralded the end for BYOD, with a recent report by analyst firm Gartner declaring its demise, stating, "There is no way for IT to assume full responsibility of securing and managing devices without ownership". Indeed, the acronym is now being translated by some as "bring your own disaster", suggesting it would perhaps be wise to learn from others' mistakes.
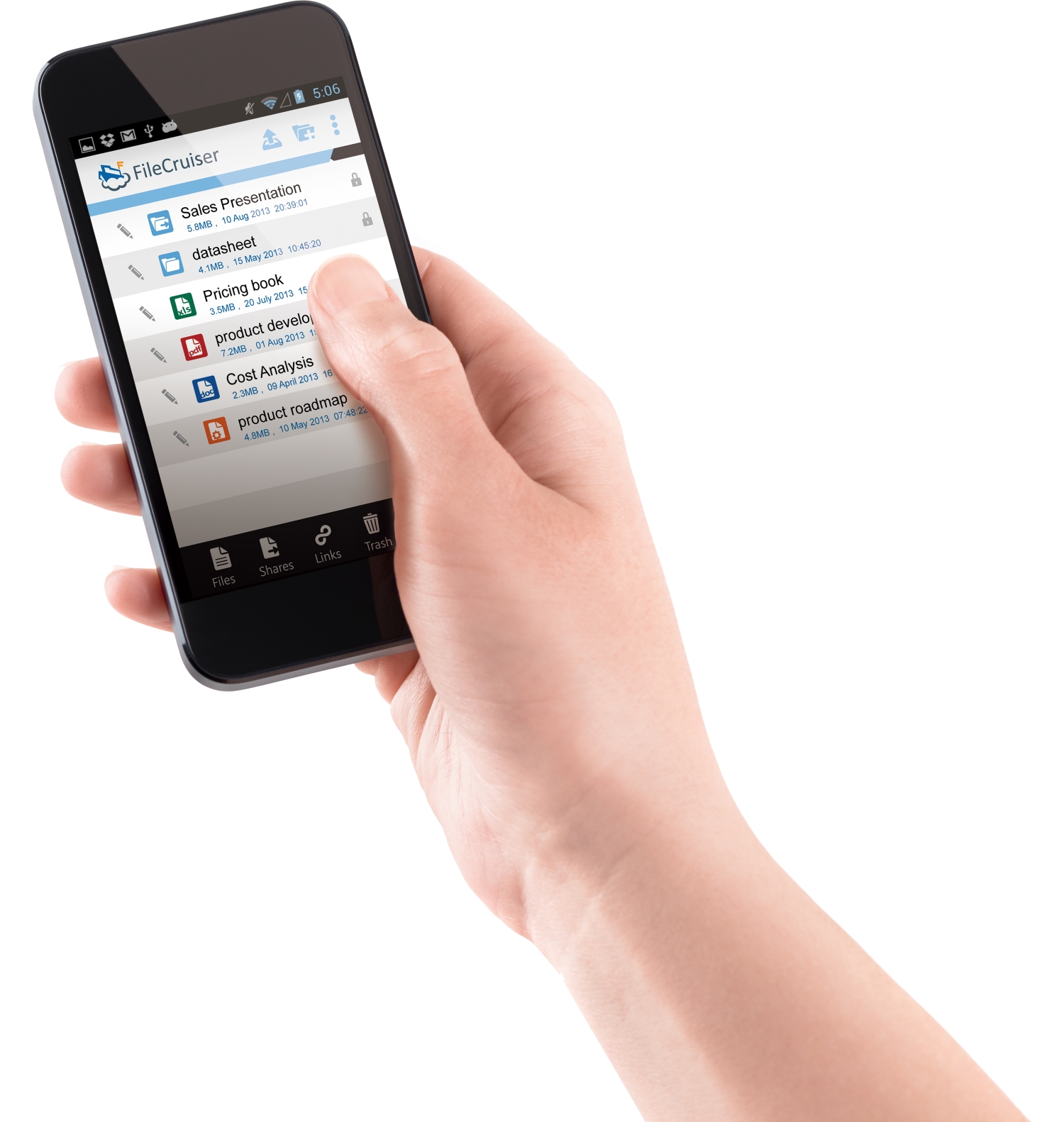
FileCruiser delivers private cloud storage for business
The move towards BYOD in business is bringing a number of new challenges. Not least of these is how to safely and easily share data across a number of devices.
Public clouds provide a tempting option but there are risks in terms of security and control. Now storage company PROMISE Technology is addressing these concerns with a new product called FileCruiser which allows enterprises to build an on-premise cloud. This means admins can manage the entire system, including hardware and software configuration, eliminating the security concerns of storing confidential data on public services.

Constantly turned on -- the bleak reality of being permanently connected
We expect, and are expected, to be contactable at any given moment -- and indeed we often expect the same of others. Send a text, and you expect a response. Pen an email, and you expect to receive one in return, and fast. Hit up someone on Google chat and an all-but-instant reply is all but expected. Maybe this doesn’t sound like you, but I can guarantee that you fit on the spectrum, and also that the people you are in contact with make the same demands of you. When did this change? It used to be that you'd call a landline number and if you didn’t get a reply you might just try again a few hours later. The fact that we now carry mobiles with us virtually 24/7 means that it is weird if someone doesn't answer the call.
They can’t be busy! Try again! Still no reply? Send a text. And an email. And an IM. If it was limited to office hours, it might be understandable -- and bearable -- to some extent, but there has been a massive slip in end-times. It is acceptable to send emails to someone at any time of day. You may have woken up at 3 in the morning and thought of something relating to work, or even just something that made you laugh, and felt the need to share it immediately. The recipient, in all likelihood, will be alerted to this email on a smartphone or tablet if they don’t happen to be sitting at their computer. At 3 in the morning, it might not wake them up, but at, say, 8pm how likely is it that the email will be ignored? The recipient's working day just got extended by several hours.
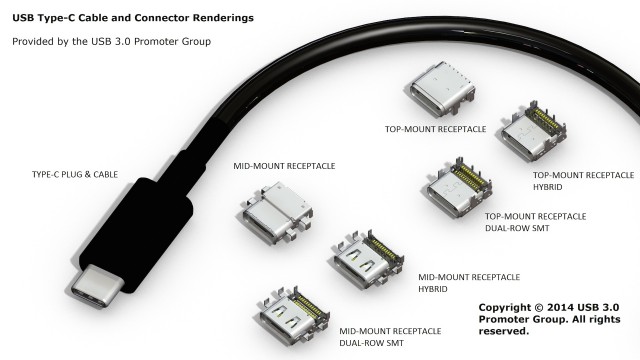
Get ready to enjoy that reversible USB Type-C connector
USB 3.0 Promoter Group announces that the much-awaited USB Type-C connector, which can be plugged in both ways, is now finally ready to enter mass production. It makes way for faster transfer speeds, courtesy of the USB 3.1 standard, increased power delivery, more compact device designs and, arguably, fewer moments of frustration thanks to its reversible orientation, which is similar to that of Apple's Lightning connector which launched in 2012.
"Interest in the USB Type-C connector has not only been global, but cross-industry as well", says USB 3.0 Promoter Group chairman Brad Saunders. "Representatives from the PC, mobile, automotive and IoT industries have been knocking down our door anticipating this new standard. This specification is the culmination of an extensive, cooperative effort among industry leaders to standardize the next generation USB connector as a long-lasting, robust solution". Here is what else you should know.

Super-secure Blackphone rooted at DefCon conference
The Blackphone, billed as a super-secure consumer alternative to standard smartphones, has been successfully hacked.
The hack comes not long after Blackphone sparred with BlackBerry after the latter called the secure device "unacceptable" for enterprise and petty customers.

Most businesses don’t have an enterprise-led mobile strategy
The boom in numbers of mobile devices offers an opportunity for enterprises to change the way they do business, but a majority are failing to take advantage.
A new white paper produced by IDC and sponsored by enterprise mobility specialist Kony looks at how companies are using mobile technology to boost their business.

5 steps to the perfect mobile web strategy
It's not commonplace, but every so often, businesses tell me that their mobile traffic is still too low for them to make it a priority over the traditional PC web. In truth, the low traffic is probably a direct correlation to the poor user experience their visitors have when accessing a non-optimized website via a mobile device. It's a vicious circle, but things have to change.
Not having a mobile web strategy for a consumer-facing company means you're ultimately moving against the market and no business should be swimming against such a powerful tide as that means being left behind. So what is a good mobile web strategy? Here are five key questions you need to answer to know if your website is mobile ready.

Enterprise mobile spending expected to grow more than 50 percent
There has been rapid growth in the number of mobile devices attached to corporate systems in recent years and this shows no signs of slowing down.
A new survey sponsored by Oracle shows that not only are enterprises more committed to mobility, but that the rate of development, deployment and spending for support of mobile applications and devices is set to increase dramatically.
Mozilla takes Firefox OS to new markets and devices, including India
Not to be outdone by Google's Android operating system, Mozilla wishes to push its own mobile platform out to customers. The organization is aiming mostly at the low-end market, but that will be expanding in the future.
The mobile platform initially debuted on just two devices, but Mozilla has managed to scare up a few more partners to produce its product.
