Equity crowdfunding finally arrives May 15: Curb your enthusiasm

Back in the spring of 2012 Congress passed the Jumpstart Our Business Startups Act (the JOBS Act) to make it easier for small companies to raise capital. The act recognized that nearly all job creation in the US economy comes from new businesses and attempted to accelerate startups by creating whole new ways to fund them.
The act required the United States Securities and Exchange Commission (SEC) by the end of 2012 to come up with regulations to enable the centerpiece of the act, equity crowd funding, which would allow any legal US resident to become a venture capitalist. But the regulations weren’t finished by the end of 2012. They weren’t finished by the end of 2013, either, or 2014. The regulations were finally finished on October 30, 2015 -- 1033 days late.
Using the 'physical web' to boost in-store sales

Bricks and mortar businesses have been in the dark. They were blinkered to what was happening within their locations, and how customers were interacting with the space. There was huge potential to fail to engage with customers effectively, repeating marketing mistakes continuously.
Meanwhile, their online counterparts had a huge advantage -- website analytics. It gave them an expanse of data sources to explore. If they asked the right questions and found the answers, they could understand every step of their customers’ journeys. They could continually optimize their offer -- and give customers what they wanted.
Instagram follows Twitter in embracing non-chronological algorithmic timelines

Any time a social network makes a change, it upsets a lot of people. Facebook has done it countless times -- just look at the vocal outpourings that followed the launch of reactions, for instance -- and Twitter recently irked many users with a new algorithm timeline, albeit one that can be disabled. Now it's the turn of Instagram.
The image- and video-based social network is currently testing an algorithm-driven timeline, much like Twitter and Facebook. Instagrammers are not happy. Not one bit (hence the appearance of the #boycottinstagram hashtag). The primary concern among users -- the narcissistic blighters! -- is that their posts will not be seen and will instead be buried in the noise of their followers' timelines. But all is not lost.
BQ Aquarius M10 Ubuntu Edition Linux tablet now available for pre-order

While Linux remains insignificant on the desktop, it is the clear king of mobile thanks to Android. While the iPhone may generate more money, there are more Android handsets being sold globally.
Unfortunately, while Android uses the Linux kernel, the devices are usually not in line with the typical experience. Outside of Nexus devices, many users have to deal with locked bootloaders and the inability to install an alternative OS. Luckily, Android is not the only mobile Linux game in town -- Ubuntu can scale beautifully from smartphone, to tablet, to desktop. Today, the first official Ubuntu tablet -- BQ Aquarius M10 -- becomes available for pre-order, giving Google a run for its money.
Microsoft: First Windows 10 'China edition' is ready

It is not easy for Western tech companies to do business in China. The local government imposes all sorts of restrictions and makes various demands to allow outside players to operate in the country or use their products. Some companies give up altogether, by either exiting the market or not even attempting to enter it, while others try to accommodate China's requests.
When it comes to selling Windows 10 to China's government, Microsoft has taken the second route by agreeing to deliver a customized version of its latest operating system to the country's agencies. The deal was made public last year, in December, and the software giant just announced that a first -- China edition, if you will -- release is now ready.
Cubot X17 -- a premium smartphone at a budget price? [Review]

Cubot is a name you may not have heard of, but the Chinese company is seeking to make an impact on the smartphone market with the X17, offering premium features at a more down market price of around $170 (£130).
First impressions are positive, the phone comes in a box with a textured bronze colored finish. In the package you get a USB cable, mains adaptor, SIM tray opening tool, a clip-on protective cover for the back, a spare screen protector -- there's one pre-installed -- and a printed quick start guide. You also get a couple of cleaning wipes which is a nice touch.
The importance of in-store mobile technology

Over the last decade we’ve seen a significant increase in mobile technology and it is now becoming the heart of customer experience; forcing retailers to figure out how the digital and physical relationships can work together.
Retailers must now decide whether to equip their personnel with mobile devices, introduce more self-service kiosks or expand mobile technology even further; all in the aid of delivering a personalized approach and improving the in-store experience for shoppers.
You could go to prison for sharing screenshots of Snapchat messages
The UK culture minister, Ed Vaizey, has warned that people who share screenshots of Snapchat messages without permission are breaking the law. Snapchat is characterized by its self-destructing messages that automatically delete after a short time.
The Conservative politician warned that anyone sharing screenshots of messages without consent could be sued and could face a prison sentence. If the content was of a sexual nature, it could result in a lengthier sentence.
New research helps isolate real threats from suspicious activity

Security teams often spend a lot of their time investigating anomalies and suspicious behavior, leaving them less time to focus on true threats.
Cloud security specialist CloudLock is tackling this problem with research into what it calls a Cloud Threat Funnel. Based on analysis of user behavior patterns it can isolate truly malicious threats from the noise of other potentially suspicious or unusual behaviors.
Facebook apologizes for enabling Safety Check in the wrong countries after Pakistan suicide bombing
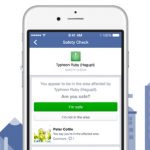
Over the Easter weekend a suicide bomber blew himself up in Lahore, Pakistan. The explosion killed dozens of people and Facebook enabled its Safety Check feature to make it easier for those in the area to let loved ones know they were OK.
But as well as asking people in Pakistan whether they were safe, Facebook also activated the feature and sent messages to people in other unaffected parts of the world. Facebook users in New York, Hong Kong, Cairo and numerous other places received messages asking "Have you been affected by the explosion?" with no reference made to Pakistan or Lahore. Facebook has issued an apology for any unnecessary worry this may have caused.
The dangers of using public Wi-Fi hotspots

There are hundreds of thousands of free public Wi-Fi spots throughout the UK. Widespread connectivity and free accessibility are two appealing features that tempt users to open up their devices for on-the-go convenience.
However, uncontrolled access to public Wi-Fi hotspots and robust mobile security often conflict with one another. Cyber-criminals now find it increasingly easy to attack public Wi-Fi networks using Man-in-the-Middle (MitM) techniques which allow the attacker to clearly view all information transmitted across networks.
How to completely avoid upgrading to Windows 10... forever

Since the launch of Windows 10, Microsoft has -- for want of a better way of putting it -- pissed off a tremendous number of people for the way it has tried to force the latest version of the operating system onto people. Some people found set up files were automatically downloaded, others were forcibly upgraded practically against their will, but plenty of people have been irritated by constant nagging about the availability of an upgrade they’re simply not interested in. Never 10 is a new tool that should mean the end of this pestering.
Various tools and techniques have been spawned as a result of things, providing fans of Windows 7 and Windows 8.1 with ways to avoid Windows 10 and Microsoft's adverts for it. Maybe you're holding out for more feature-complete builds from the Redstone branch, or perhaps you just don’t like change. You would think that Microsoft would understand that 'no' means 'no' but there have been countless stories of people who have declined the Windows 10 upgrade finding themselves subjected to continued nagging. A registry hack can be used to block nags and upgrades, but Never 10 is a free portable app that does the hard work for you.
View, measure and convert DWG/DXF files with Autodesk DWG TrueView 2017

We've talked about simple DWG/DXF viewers before -- de-caff,Mini CAD -- but while they're compact and easy to use, they won't open everything: CAD formats are just too complex.
If accuracy and reliability are key, then you might prefer Autodesk DWG TrueView 2017 -- it's from the people who developed the DWG format, so you can be sure it'll open just about anything.
Is Microsoft actually about to do something interesting with Live Tiles in Windows 10?

With Live Tiles, Microsoft has promised much but delivered little. This could be about to change. We're just days away from Build 2016, and there's a great deal of excitement about what could be revealed. Live Tiles, it seems, could be about to evolve into something useful.
The schedule for the developer conference has been posted online, and it sees Microsoft is entering full-on tease mode. At a session called 'What's New for Tiles and Toast Notifications', Microsoft promises a couple of surprises. Build is aimed at developers so it's hard to predict exactly what's in store, but Microsoft's description of the session is certainly titillating.
ESET discovers 'unique' self-protecting USB trojan

ESET has detected an undetectable malware. The security firm recently said to have discovered what it now calls Win32/PSW.Stealer.NAI, also known as the USB Thief.
The malware is designed to steal data and is, according to the firm, basically undetectable. It cannot be copied or reverse-engineered, making it extremely difficult to detect or analyze.
Most Commented Stories
© 1998-2024 BetaNews, Inc. All Rights Reserved. Privacy Policy - Cookie Policy.