Avast hacked -- 400,000 user details stolen

Getting hacked is bad enough for any company -- just ask eBay -- but it’s even worse (and certainly more embarrassing) when the firm in question is responsible for producing security software designed to protect us from the dangers on the web. Eight months ago AVG and Avira had their websites taken over by pro-Palestinian hackers and now Avast admits it’s had to take its forum offline due to an attack.
Avast says "user nicknames, user names, email addresses and hashed (one-way encrypted) passwords were compromised" and while it stresses less than 0.2 percent of users were affected, that still equates to details of around 400,000 people.
Kaspersky recommends Windows Phone security apps

Windows Phone may not be as attractive of a target to hackers as Android and iOS are, but that does not mean users should rest easy. As the platform's installed base grows so will the risks. While the tiled smartphone operating system is fairly secure -- it has received the coveted FIPS 140-2 certification -- there are a number of basic security measures and tools that allow users to keep their personal information, and Windows Phone, safe.
On top of the inconspicuous security features that Microsoft bakes into Windows Phone (such as app sandboxing, and exclusive access to the curated Store), users can leverage the built-in tool find my phone (read this article to find out how to use it), and various apps to step it up a notch. Well-known security firm Kaspersky focuses on the latter in a new blog post, listing five apps that "enhance security on your Windows Phone 8".
The real cost of transitioning your business to the cloud

As knowledgeable as heads of IT and CIOs inevitably are, there is at least one area where an admission of ignorance is wiser than faked knowledge -- how to determine the true cost of transitioning an enterprise's IT into the cloud.
At first, this might seem counter-intuitive. After all, moving from on-premise IT to the cloud is such a fundamental strategic shift, with so many financial, technical and business considerations, that you'd expect any cloud proposal to contain a detailed breakdown of the costs of transition. This was certainly possible in the early days of cloud computing, when there were only the costs of in-house servers and software to measure.
Watch the LG G3 launch here live

One of the most highly anticipated phones of 2014, the LG G3, is to launch today at simultaneous events in London, New York, and San Francisco. There’s not much we don’t know about the device, thanks to a stream of leaks.
The 5.5 inch handset is expected to have a brushed-metal finish and offer a Quad HD screen with a resolution of 2560x1440. Leaked product information says it will have a Snapdragon 801 processor and 2GB of RAM, 13MP rear camera with image stabilization, 2.1MP front camera, and be water and dust repellent.
VirusTotal Uploader for OS X arrives

VirusTotal has released its first VirusTotal Uploader for OS X, a simple tool which scans a file, folder or application for malware with 50+ antivirus engines.
Using VirusTotal Uploader for OS X can be as easy as dragging and dropping a file onto the program window. It’s uploaded, there’s a delay while the site checks your file with all the main antivirus engines, and finally a "Detections" figure gives you the results ("0/53", hopefully).
Hacker holds Apple devices for ransom

Holding a device for ransom is a scary practice. Hackers seize control, and then ask the owner to pay a fee to unlock it. If the victim does not comply with their demand, there is little that can be done to regain access to private data, which may include sensitive information like bank account passwords, photos, work documents and so on. Some people cave in, paying the hackers. Others refuse and end up losing everything on their device.
Some Australian Apple users are reporting they are dealing with a hacker (or group of hackers) that goes by the name Oleg Pliss, that holds their iOS and Mac devices for ransom, demanding a certain fee (initial reports say $100) to relinquish control. Affected Apple devices have been locked through Find My iPhone, a tool that lets users track their enrolled iOS and Mac devices, basically rendering them useless.
PlayStation 4 to follow Xbox One into China

Sony's PlayStation 4 console might be leading in the sales war against the Xbox One, but the PS4 isn't resting on its laurels, with Sony having announced plans to enter the Chinese market.
According to a Bloomberg Businessweek report, Sony will make and sell the PS4 in China, forming two joint ventures with Shanghai Oriental Pearl (Group) Co. in which Sony will own a 70 percent stake in one venture, and a 49 percent stake in the other.
Australians fight shark attacks with Google+ and 'clever buoys'

As a young boy on Long Island, I spent many a summer at Robert Moses beach. With the exception of the occasional jellyfish sting, it was very safe. Unfortunately, a child's imagination can be rather powerful. After seeing the movie Jaws, I would become frightened when the seaweed would rub against me. Even though it was only a plant hitting my leg, in my mind, I pictured a ferocious shark.
Unfortunately, shark attacks are a real problem in some parts of the world, including Australia. In that country, they must be extra-careful when swimming in the ocean. A shark can cause severe injuries, including death. A company called Optus however, has created a new way to detect and warn of sharks, using an unlikely partner -- Google+.
LibreOffice 4.3 Beta available to try, improves Start Center
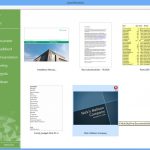
The Document Foundation has unveiled the first public beta of the forthcoming LibreOffice 4.3. The new 4.3 release branch sees some notable user-interface tweaks, performance enhancements and a number of new and tweaked features.
The word processor Writer is the beneficiary of most changes in this next release, while users should also enjoy better quality imports of PDF files.
Create a bootable antivirus disc with ESET SysRescue Creator

ESET SysRescue Live Creator is a handy tool for creating a bootable antivirus rescue CD or USB key.
There’s no shortage of competition in this area, of course, but Live Creator has one or two useful touches that you might appreciate.
How to get the best out of your Huawei Ascend P7

Huawei is not such a well-known smartphone maker as the likes of Samsung, Sony or HTC. But it has recently launched a relatively low cost, relatively high spec phone in the Ascend P7, and despite some quibbles about battery life I gave it a thumbs up in my recent review.
The Ascend P7 runs Android 4.4 (KitKat), and like all higher-end handset makers Huawei has its own skin which it calls Emotion UI. You'll notice this immediately because all the app icons have been given a makeover. The "flat" design is clean and neat looking, and it makes a good first impression. More importantly, perhaps, Emotion UI adds a range of features to the Android staples. Let's take a look at how best to use those features to our advantage.
How to continue getting free security updates for Windows XP -- until 2019
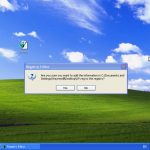
Microsoft has stopped providing XP users with security updates, forcing them to either upgrade to another, newer operating system, or gamble with their safety. While the latest usage figures show that a large portion of users are moving away from XP, there’s still a sizable number of users who aren’t -- or can’t.
If you’re an XP user, or know some XP users, there’s a trick which makes it possible to receive security updates for the aging OS for another five years -- right up until April 2019.
Emerging smartphone vendors put on their fighting gloves

According to a new Kantar Worldpanel ComTech report, smartphone "fragmentation" is on the rise in Europe. Locally-emerging brands, like Huawei and Wiko, are giving established players, like Apple and Samsung, a run for their money, delivering comparable offerings at much lower prices. As the average selling price drops even further, the former are set to erode more of the latter's market share.
The report also suggests that some established brands, that have lost their way, are "showing resurgence" on the old continent. Dominic Sunnebo, the firm's strategic insight director, gives Motorola and Sony as example. The former has crawled its way back on Europe's radar with attractive smartphones like the low-cost Moto G and dirt-cheap Moto E, the latter of which is among the least expensive Android smartphones from a well-known vendor at £89 ($130 in US).
eBay initially believed no user data had been compromised in breach

This week saw a huge eBay security compromise, which opened up user details on a major scale -- but when the issue first came to light, the company didn't think any user data was involved.
You can't have missed the story of this breach -- and the ensuing fracas in which eBay was roundly criticized for its lackadaisical response this week. With passwords involved in the compromise, eBay's push for users to change their passwords was woefully sluggish -- failing to get even a prominent warning up on the site itself until the day after the breach was officially admitted (at least going by GMT; see our closer look at how badly eBay handled its database breach). And indeed there was no forced reset of user passwords.
Protect your personal messages with CTI Text Encryption
CTI Text Encryption is a lightweight, portable text encryption tool. It’s ideal for sending sensitive information via insecure channels (email, online chat, web forums), perhaps from someone else’s computer, although you can also use it to save confidential data in files or elsewhere.
The open source program is a tiny download (827KB), a single executable with nothing else attached. Copy the file to a USB stick and it’s ready to use almost anywhere.
Recent Headlines
© 1998-2025 BetaNews, Inc. All Rights Reserved. Privacy Policy - Cookie Policy.