
Samsung T7 Shield USB-C SSD now available in 4TB
Last year, Samsung released the T7 Shield -- a fast and durable USB-C SSD. At the time, the portable drive was offered in three colors (beige, black, and blue) plus two capacities (1TB and 2TB).
Today, Samsung adds a new 4TB capacity option to the T7 Shield lineup. Yes, you can now get the drive with double the storage of the previous top capacity. Unfortunately, this 4TB variant is only available in black -- fans of beige and blue are out of luck with this capacity.

Linux Mint 21.2 is named 'Victoria'
Are the Linux Mint developers fans of the Spice Girls? That I don't know. What I do know, however, is Linux Mint 21.2 has been code-named "Victoria." I'd like to think this version of the operating system is being named after soccer-star David Beckham's wife Victoria (who once went by the stage name "Posh Spice" as a member of the aforementioned pop singing group), but probably not.
Anyway, besides the codename of "Victoria," the Linux Mint developers have shared some interesting tidbits about the upcoming Ubuntu-based operating system. Most importantly, it will be released in June 2023. As expected, Linux Mint 21.2 will once again come with your choice of three desktop environments -- Cinnamon, Mate, and Xfce. If you opt for the Xfce variant, you will be treated to the cutting-edge version 4.18.
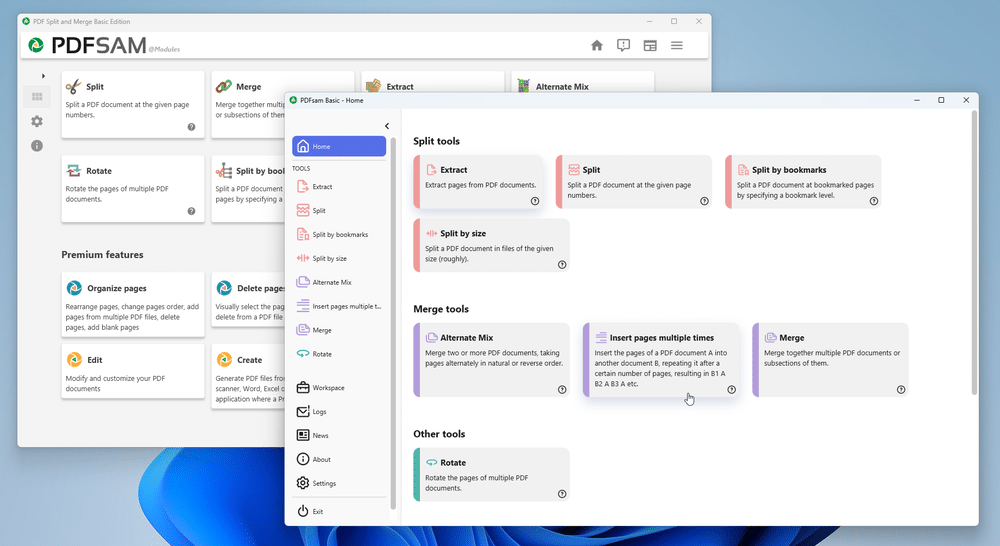
PDFsam Basic 5.0 released, makes it easy to split, merge and extract pages from PDFs
Sober Lemur SRL has just released a major new version of its free and open-source PDF toolkit with the launch of PDFsam Basic 5.0 for Windows, macOS and Linux.
The application, which allows users to quickly and easily extract pages from PDFs as well as offering split, merge and rotate tools, gains a major facelift with the version 5 release, along with a brand new tool and several additions to existing features.

Cloud storage remains popular but comes at a cost
A new survey of 350 IT leaders in the US and UK shows 84 percent of respondents want a large portion of their storage to remain in the cloud, and two-thirds of them want as much storage in the cloud as possible.
On average, enterprises have put 57 percent of their storage in the cloud, whilst keeping 43 percent on premises.
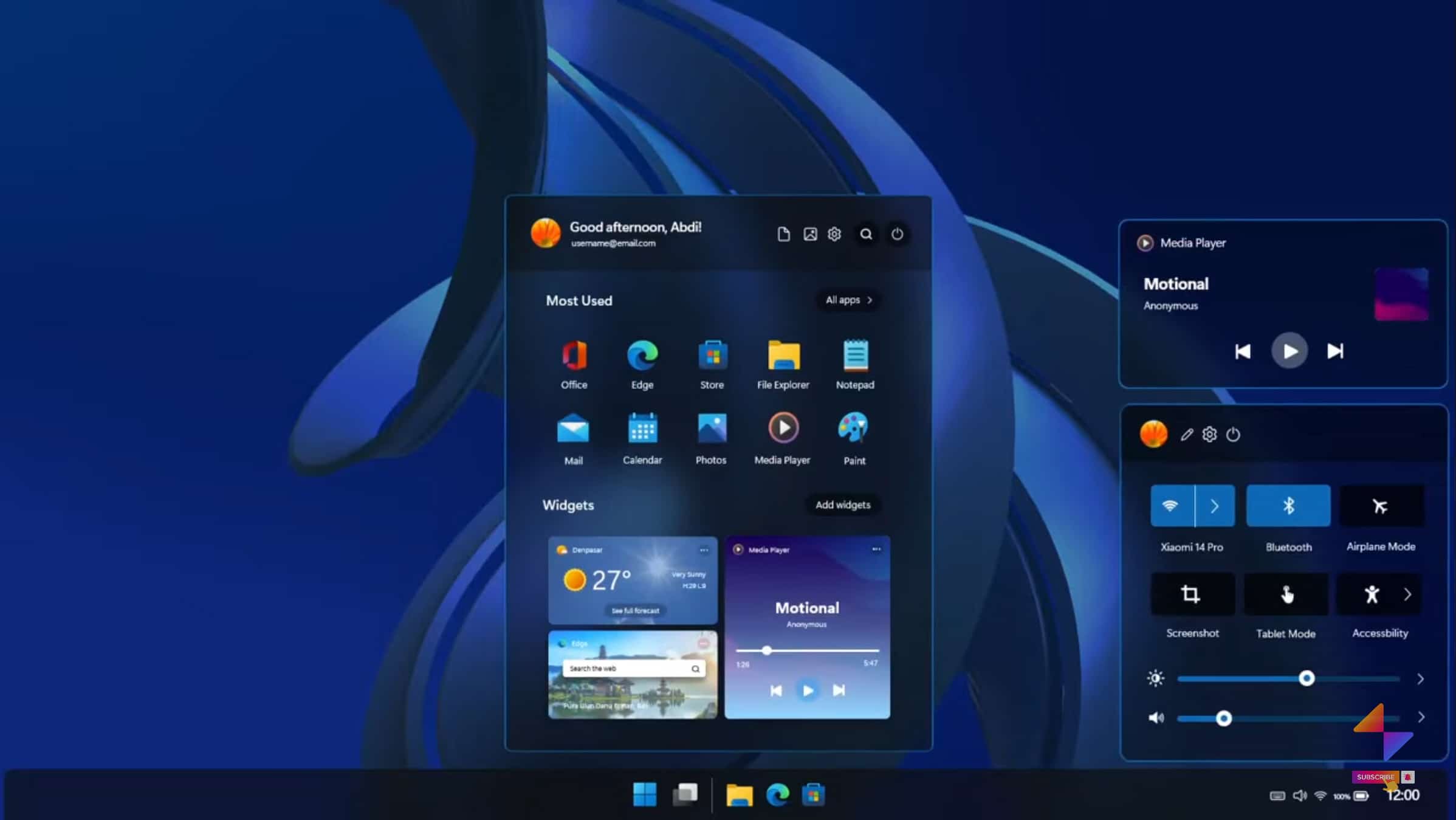
Windows 11X: The dream upgrade your PC needs
Although Windows 11 has a lot to recommend it, it does feel rather unfinished, and it’s a situation which isn’t helped by a never-ending stream of problematic updates -- no wonder people are already talking about its potential successor, Windows 12.
But maybe we don’t need to make a full version leap just yet, perhaps the problems with the new OS could be solved with a bit of thought and attention.

Checkmarx launches Supply Chain Threat Intelligence
The software supply chain is increasingly being weaponized by attackers seeking to compromise businesses and steal information.
Application security specialist Checkmarx is looking to combat this with the launch of a new product which delivers detailed threat intelligence on hundreds of thousands of malicious packages, contributor reputation, malicious behavior and more.

Economic pressure forces connected device makers to seek efficiencies
Economic pressures are forcing delays and price increases on connected device makers, with 38 percent experiencing delays in bringing devices to market, while almost half (48 percent) say they have been forced to increase prices.
New research from the Qt Group -- based on a survey of 250 embedded device manufacturers in the US, UK, France and Germany, conducted by Censuswide -- finds manufacturers are adopting various techniques in order to fuel efficiencies.

Plugable USB-C Stand Dock can turn an Apple iPad, Windows tablet, or Android device into a legitimate desktop PC
Apple's iPad is a tablet, obviously, but when you add a keyboard case, it magically becomes a laptop too. But did you know M1 or M2-powered iPad tablets (running iPadOS 16.1 and higher) can also serve as a desktop PC with full-screen monitor support? It's true! By plugging in a USB-C dock, you can connect a keyboard, mouse, monitor, external storage, and more.
Today, Plugable launches a new USB-C Stand Dock (model number UDS-7IN1). While this product is primarily designed for M1/M2 iPad devices (such as iPad Pro and iPad Air 5), it can work with USB-C Android devices and Windows tablets (such as Surface Pro) as well. While this dock should technically work with laptops and desktops, the "stand" aspect (which props up the phone or tablet like a monitor), would be wasted.

The latest Windows 11 problem sees updates failing with 0x800f0988 and 0x800f0831 errors
It is no secret that the updates released for Windows 11 have been rather more problematic than updates for previous versions of Windows. Microsoft has managed to earn itself an unenviable reputation for poor quality control, with update after update causing a wide range of issues over the past year and a half.
The problems with updates tend to rear their heads once they have been installed, but there is also an issue that is preventing people from installing updates in the first place. The recently released KB5022303 and KB5022360 updates are among those that fail to install, generating various unhelpful error codes including 0x800f0988 and 0x800f0831.
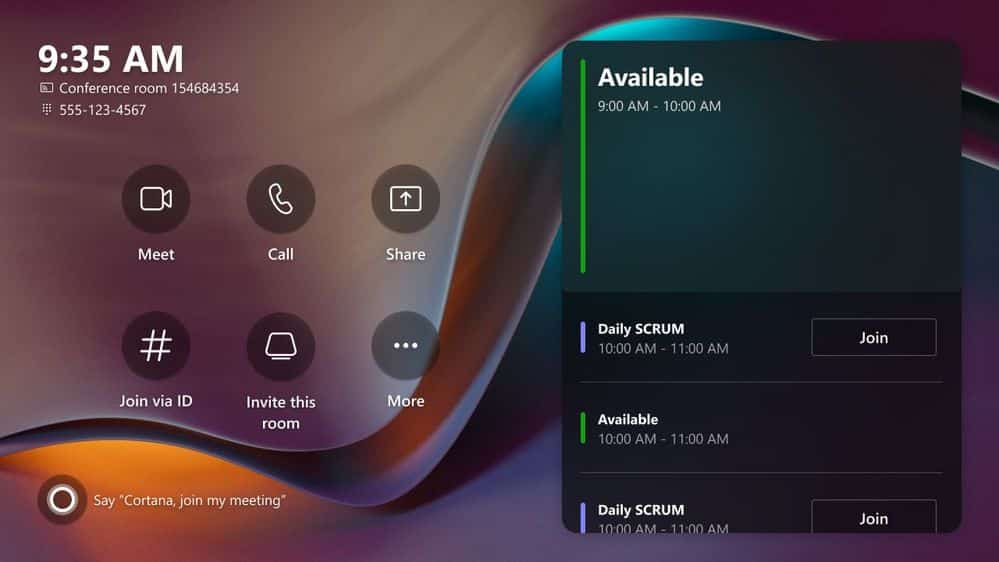
Microsoft Teams Rooms on Windows is getting an amazing new look
Microsoft has revealed details of an upcoming visual update to Microsoft Teams Rooms on Windows which is due to hit general availability by the end of this quarter.
"Vivid" and "vibrant" are words Microsoft is using to describe the new look and feel that will be making its way to the software soon. A quintet of new themes will be added for greater customization options, and there are new buttons, an updated calendar and better alignment of interface appearance across Windows and Android.

GitHub hit by hackers; code signing certificates for GitHub Desktop and Atom applications stolen
GitHub has issued a warning about "unauthorized access to a set of repositories used in the planning and development of GitHub Desktop and Atom" in a hack that took place back in December.
Users are being advised to ensure that they install the latest updates for the affected software, but there is currently no suggestion that GitHub.com has been impacted. With the attackers having stolen code signing certificates, GitHub is revoking the certificates for some versions of Atom and GitHub Desktop on February 2, so users should update before this date.

Real time data collection is needed for eCommerce companies to reach their full potential
According to new research, 62 percent of eCommerce organizations say that real-time data collection will be at the forefront of their priorities for 2023.
The study, carried out for Oxylabs by Censuswide, surveyed over 1,000 senior data decision-makers, split between UK and US eCommerce companies. It finds that as companies begin to rely more on efficient and low-cost data collection methods such as external data gathering, used by 40.54 percent of respondents, there is a clear shift towards gaining more actionable insights.

Whether you like it or not, AI is coming to search engines
The public release of ChatGPT has started an AI craze that has taken the online world by storm. ChatGPT, for those unaware is a language model that has been trained for dialogue specifically.
It works similarly to chatbots, but is not as limited to returning information based on certain keywords in requests.
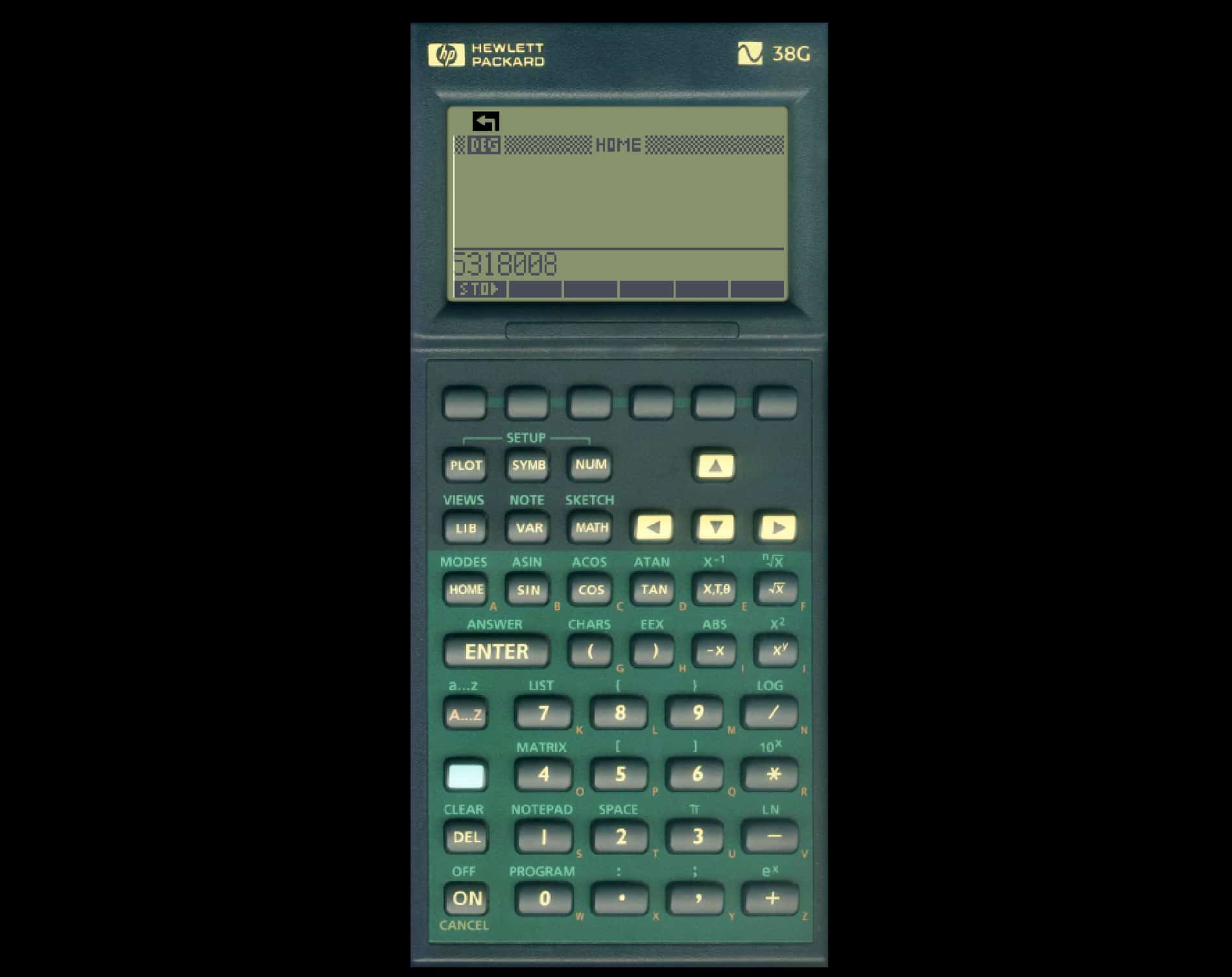
Say goodbye to dead batteries: Calculators now live forever on the Internet Archive
The Internet Archive is home to all manner of emulated hardware, including retro handhelds and vintage consoles.
Now the archive offers a new family of emulators for people to play around with online -- calculators! Like the various console emulators, this has been made possible thanks to the power of MAME (Multiple Arcade Machine Emulator).

Why quantum computing threatens security as we know it [Q&A]
Much of our current IT infrastructure relies on DNS to safely route traffic. Securing that infrastructure is in turn heavily reliant on cryptography, but there's a threat looming on the horizon.
Quantum computing will offer a level of processing power that could render current cryptographic techniques obsolete, and that's a problem for the entire internet and networking world. We spoke to Peter Lowe, principal security researcher at DNSFilter, to discuss the possible impact of quantum computing on security and what can be done to address the threat.
