
Your Windows 7 desktop has turned black? Microsoft has a fix on the way... and workarounds in the meantime [Updated]
Windows 7 is dead: you know this. There are no more Windows 7 updates for most people: you know this. And some believe Windows 7 should be made open source: yeah, right
Whatever the status of Windows 7, the fact of the matter is that there are plenty of people still using it, and the last update (KB4534310) caused a strange problem for some users, turning their desktops black. Microsoft has now acknowledged the issue, but says that it will only fix the bug for those who are willing to pay.

Microsoft Translator gets Gaelic so we can communicate with more of the Irish
With St. Patrick's Day fast approaching (March 17), many of us will soon be eating traditional Irish cuisine, such as corned beef, cabbage, potatoes, and soda bread. There are sure to be many people wearing the color green as well. On this day, we celebrate all things Irish.
But what if you want to hold a conversation with an authentic Irish person on that holiday (or any other day for that matter)? If the person prefers to speak Gaelic, rather than English, this can be a big problem. Thankfully, Microsoft has come up with a solution. Using its popular Translator service, you can now communicate with those that speak Gaelic -- just use your smartphone to convert words and hold a conversation!

Buy the limited-edition white GHOST Logitech G PRO wireless gaming mouse before it's gone!
Last month, Logitech did something very cool. The company released a limited-edition pink variant of its G PRO wireless gaming mouse. It dubbed this model "PIXEL" and vowed to donate the profits from its sales to charities. This proved to be extremely popular, as the PIXEL sold out the same day it was released. This was a big success, as not only did some Logitech fans score a rare collectible, but charities received money as a result.
Today, the Logitech is doing it again, this time with a mouse called "GHOST." Once again, it is a limited-edition G PRO wireless gaming mouse, but this time, the rare color is white rather than pink. I expect GHOST to sell out much faster than PIXEL, as the pink color had a more limited appeal. A white mouse may entice more shoppers, such as Mac users that want to match with their Apple keyboard, for instance. And yes, there are gamers that use macOS.

Should Microsoft make Windows 7 open source? The Free Software Foundation thinks so!
Windows 7 is dead to Microsoft -- unless, of course, you're willing to pay. It's now ten days since the operating system reached end of life, but many people, for various reasons, are choosing to stick with it rather than upgrading to Windows 10.
This means missing out on security updates, but the Free Software Foundation (FSF) thinks it has a solution. It suggests that Microsoft 'upcycles' Windows 7 and makes the operating system open source so that the community can "study and improve" it.

The perils of choosing convenience over privacy: When is it not worth it?
From the lightbulb and telephone to smartphones, the advanced technology of the day has always been lauded as a way to make peoples’ lives easier. But while today’s technology makes it possible to pay that electricity bill from your phone, it has also opened up privacy concerns that were unimaginable even ten years ago. In that decade, it is reported that more than 4 billion records have been stolen and 15 of the largest data breaches in history have occurred. Has technology marketed as a consumer convenience contributed to these breaches?
While George Orwell presented a dire picture of "big brother," today’s society certainly seems willing to embrace technologies that are always watching, listening and capitalizing on personal data shared in our daily lives. But what’s the true cost of choosing convenience over privacy? Let’s look at how technology has driven privacy complacency for the sake of convenience and how it has changed the way people think about and safeguard their information.

How CCPA will impact on enterprises and individuals [Q&A]
With the California Consumer Privacy Act (CCPA) having come into force at the beginning of the year, and Data Privacy Day coming up next week, privacy is very much in the news at the moment.
But how much of an impact will the new legislation have? And what do organizations need to do to make sure they don't lose consumer trust? We spoke to Chad McDonald, VP of customer experience at Arxan to find out more.

Microsoft confirms that most Windows 7 users won't get a critical Internet Explorer security patch
Internet Explorer may be a relic from the past, but it's still out there and used by surprising numbers of people. Not all versions of it are supported by Microsoft anymore, so when a critical bug was discovered in the Windows 7, 8.x, 10, Windows Server 2008 and 2012 versions of the browser, there were questions about who was going to be protected.
The bug was revealed just days after support ended for Windows 7, and it wasn't clear whether Microsoft would stick to its guns and leave those people still using this operating system out in the cold and unprotected. The company has now confirmed what's going to happen.

Sonos CEO apologizes for device update fiasco
Owners of Sonos devices were disappointed when they were told by the company that as of May 2020, there would be no more software updates released for older equipment. Sonos offered customers two options for "legacy products": keep using them without updates, or brick them by putting them in Recycle Mode in return for a 30 percent discount on a future purchase.
There was an understandable backlash from Sonos' userbase, and now the company's CEO has been forced to pen a letter in which he assures customers that devices will work for "as long as possible". Patrick Spence concedes that "we did not get this right from the start". He continues: "My apologies for that and I wanted to personally assure you of the path forward".

Sorry, Linux and macOS gamers, but you are losing Rocket League online play
Rocket League is one of my favorite PC games. Not only is it extremely fun, but it runs well on average hardware and is very easy to play. Seriously, folks, the learning curve is so low that almost anyone can just start playing right away. If you aren't familiar with Rocket League, please know it is essentially soccer with cars -- you drive into a giant ball and try to get it into the goal.
Another cool aspect of Rocket League? It is cross-platform, running on Windows, Mac, and even Linux. Sadly, this is changing, as the game's developer, Psyonix, is killing support for all desktop PC platforms that aren't Windows. That's right, if you are a Linux or macOS gamer (yes, they really exist), you will get one final patch before March -- when support officially ends. Sadly, this update will remove the ability to play the Mac and Linux versions online. And no, you cannot avoid the patch and continue to play online. In other words, you will soon be limited to offline play. Laughably, the game will continue to work fully on the now-unsupported Windows 7.

Microsoft releases Windows 10 Insider Build 19551 to the Fast ring
Microsoft continues to roll out new test builds for future feature updates of Windows 10, and today sees the release of Build 19551.1005 to Windows Insiders in the Fast ring.
There’s not too much to get excited about here, although Microsoft is now conducting an experiment regarding how driver updates get delivered through Windows Update.
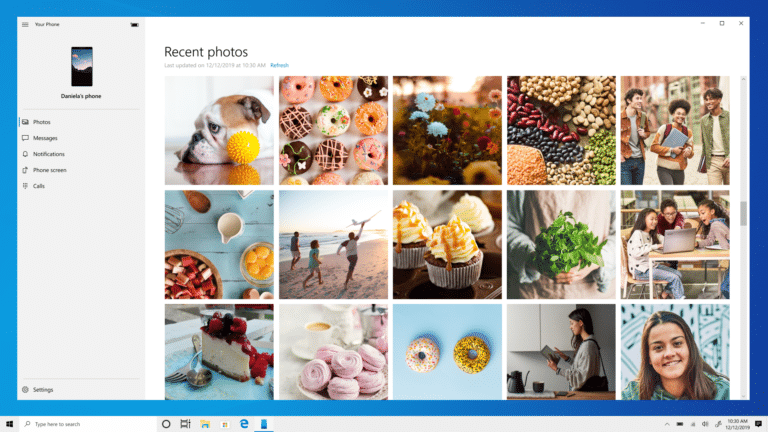
Microsoft's Your Phone app for Windows 10 now displays 2,000 photos from your Android device
Microsoft’s Your Phone app connects your Android smartphone to your Windows 10 PC, making it possible to view and reply to text messages directly in Windows, receive and manage phone notifications, and -- most recently -- make, receive, and decline phone calls directly on your PC.
One of the app’s more useful features is the ability to view and save copies of the most recent photos on your phone, but this did have one particularly annoying limitation.

Twitter adds emoji reactions to DMs
Taking a leaf out of Facebook's book, Twitter has added a new emoji reactions feature.
Unlike Facebook, Twitter reactions are only available for direct messages, not individual posts, but it still adds a new way to respond to messages. In all, there are seven emoji reactions: crying, surprised, sad, heart, flame, thumbs up and thumbs down.

Budget constraints and cyberattacks are top concerns for SMBs
SMB network security specialist Untangle has released the results of a survey of its channel partners looking at current trends and barriers that they face when protecting clients against emerging threats.
It also examines how these companies will shape future strategic business decisions for Managed Security Providers (MSPs) and Value-Added Resellers (VARs).

Lack of data confidence leads to AI failures
More than a third of AI and analytics projects in the cloud are failing due to poor quality data according to a new survey.
The study from data specialist Trifacta surveyed 646 data professionals across different industries and titles to examine how organizations are handling the accelerating transition of data to the cloud, the obstacles of data cleaning for analytics and the time constraints they face when preparing data.
Google researchers reveal flaws in Safari that could be exploited to track users
Apple's Safari web browser was found to have multiple security flaws that allowed for user's online activity to be tracked, say Google researchers.
In a yet-to-be-published paper, the researchers reveal issues in a Safari feature which is actually supposed to increase user privacy. The Intelligent Tracking Prevention (ITP) feature found in the iOS, iPadOS and macOS version of the browser is meant to block tracking, but vulnerabilities mean that third parties could have accessed sensitive information about users' browsing habits.
