
After a brief absence, CBS returns to DISH
For those who have cable or a satellite TV service, you may be used to the occasional channel, or a few of them, disappearing. This is most frequently due to contract disputes as large conglomerate networks attempt to prop up channels that aren't doing so well. It's usually worked out, though it can take some time.
That scenario recently played out between CBS and DISH. The former yanked its channel package off of the satellite provider's service in an effort to extort more money.
Best Windows 10 apps this week
Two-hundred-and-fifty-eight in a series. Welcome to this week's overview of the best apps, games and extensions released for Windows 10 on the Windows Store in the past seven days.
Microsoft started its Black Friday sale early this year. You can get discounts on hardware and software. Brian covered the details.
Twitter is working on a 'save for later' feature called, uninspiringly, Bookmarks
Twitter is one of the more divisive social media platforms out there, managing to attract passionate love and hate in just about equal measure. But even people who use and like Twitter freely admit that it has its problem, one of which is the lack of a bookmarking feature.
There is the option to "like" tweets, but this can be an awkward way to save something you're interested in reading later. Recognizing that users need something rather more robust and useful, Twitter is working on a feature called Bookmarks.

UK broadband companies banned from advertising misleading top speeds
The advertising of broadband services has long been fraught with complaints and controversy, but a new rule change should help to bring this to an end.
Following an investigation by the Advertising Standards Authority (ASA), ISPs will no longer be able to advertise high "up to" speeds. Instead they will have to advertise the average speed achieved by at least 50 percent of customers at peak times. Previously, the rules permitted the advertising of headline speeds enjoyed by just 10 percent of people, and the ASA found that many broadband customers were disappointed with their connection speed.

Microsoft Black Friday 2017 sale -- score amazing deals on Surface, Xbox, and Windows 10 devices!
If there is someone in your life that loves technology, and you want to get them a really great Christmas gift, look no further than the Microsoft Store. Seriously folks, if you want to delight someone special, just get them an Xbox One or Surface. If Microsoft's Surface-branded computers are too expensive, there are plenty of other Windows 10 devices from which to choose too.
Understandably, buying such extravagant gifts might be a hardship financially, so if you have been waiting for the best time to make that purchase, please know that now is when you should finally pull the trigger. You see, Microsoft's Black Friday 2017 has gone live a day early! Yes, you can score a great deal on Surface, Xbox, and Windows 10 devices right now. Here's the details, y'all.

AOMEI Partition Assistant Standard 6.6 adds support for exFAT, improves bootable media support
Everyone needs a partition management tool. Windows ships with its own limited tool, accessible under Disk Management, but it’s restricted in a number of key areas, not least its inability to move files to help with the repartitioning process.
AOMEI has just released a major update to its free partitioning tool: Partition Assistant Standard 6.6. It’s become our go-to partition editor, and version 6.6 makes it even more compelling than ever.

Millennials may prefer Bitcoin over savings accounts for storing their wealth
The insane growth of the cryptocurrency market is making Bitcoin very attractive as a store of value. Folks who have bought Bitcoin at the beginning of the year are now looking at an 820 percent return on investment, which is much more difficult to achieve in traditional markets and virtually impossible to match using savings accounts.
Millennials are starting to take notice, with a new report suggesting that they are shunning savings accounts in favor of Bitcoin. Baby boomers, you can add this to the "millennials are killing" list.

The role of education in fighting security breaches [Q&A]
When securing systems most people's thoughts turn to the technology of firewalls, anti-virus programs and so on. What’s often neglected is the human aspect.
Many breaches are down to poor password practices or falling for phishing emails, things which can be prevented with better education. We spoke to Stephen Burke, founder and CEO of security awareness specialist Cyber Risk Aware to get his views on how awareness training can be used to drive better behavior and make businesses more secure.

Ethereum passes $400
For the first time in the past few months we are starting a conversation about the cryptocurrency market that does not revolve around Bitcoin. The reason is Ethereum, which just went past $400 for the first time since the record high in mid-June.
This is a pretty significant development, as Ethereum's performance has been lackluster since its peak. The only time it got close to $400 was on September 1, after which a ban on ICOs in China helped drive its price to under $200.

Google finally fighting faux family-friendly YouTube videos
YouTube is an amazing place to consume media. There is great family-friendly content from people like iJustine and Rosanna Pansino, for instance. Unfortunately, there is another side of Google's video site, where people such as Pewdiepie and Leafy post racist and sexist content. For parents, it can be quite difficult to know which videos are appropriate for children. Sometimes adult content can even show up in the YouTube Kids app.
To make matters worse, some content creators have been disguising adult-themed videos as being family-friendly -- a wolf in sheep's clothing, if you will. For instance, what may appear to be a video about Spider-Man and Elsa from Disney's Frozen, can quickly morph into a video about feces and hypodermic needles. I kid you not -- there are some truly bizarre videos designed to exploit children on YouTube nowadays. It is being referred to by some as "Elsagate," and this excellent video does a great job of explaining the growing phenomenon. Sadly, these weird videos generate a lot of revenue too, leading to copycats. Thankfully, Google has apparently had enough, as it now vows to crack down on adult content that masquerades as being family friendly.

Microsoft releases Windows 10 Redstone 4 Build 17046 to the Fast ring
Microsoft is back to rolling out new Insider Preview builds to the Fast ring on a weekly basis.
The latest release, Build 17046, introduces a number of improvements, changes and fixes. So what’s new this time around?
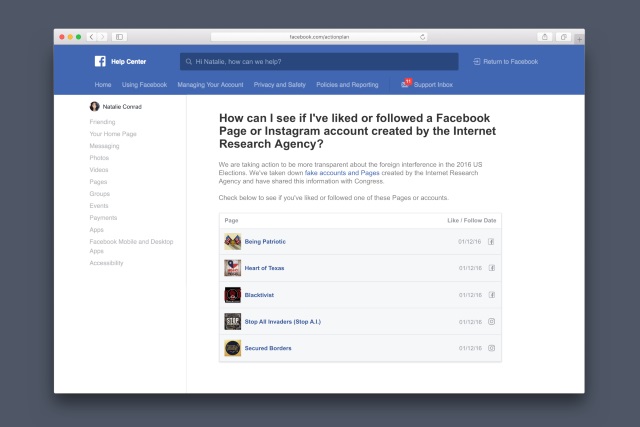
Facebook is developing a tool to let users know if they interacted with Russian troll accounts
Russia's use of Facebook and other social media to try to influence the outcome of elections around the world has been the subject of investigation for some time now. Millions of Facebook users were exposed to divisive ads placed by Russia, and the social networking site is doing what it can to be transparent about what happened.
Having admitted that Russia bought ads on the site, Facebook is now developing a tool that will enable users to determine if they interacted with the Internet Research Agency -- the propaganda company also known as the Trolls from Olgino.

SJCAM SJDASH dash cam review
SJCAM has become one of the biggest players in the action camera market thanks to devices like the SJ5000X Elite and SJ6 Legend. And now it's come up with a product targeting a different audience.
The SJDASH is SJCAM's first dash cam and, just like the other devices in the company's range, it is designed to appeal to consumers looking for a good balance between quality and price. Question is, how does it perform? I've tested it to find out.

UC Browser returns to Google Play after tweaks to its policy-infringing settings
UC Browser was unceremoniously removed from Google Play last week after it was discovered that a setting within the app violated Google policies. Now the popular web browser is back with an updated version.
The company behind the app is pleased to return its flagship title to the Play store, but also voices its delight that during UC Browser's brief absence, the cut-down UC Browser Mini proved fantastically popular.

UK government pledges cash to boost the digital economy
In today's budget speech the UK Chancellor, Phillip Hammond, has announced a number of measures aimed at boosting the tech sector.
These include £500m of support for 5G mobile networks, full fiber broadband and artificial intelligence and £540m to support the growth of electric cars, including more charging points. A further £2.3bn is allocated for investment in research and development and £30m to develop digital skills distance learning courses.



