
Panasonic unveils Toughbook 33 2-in-1 detachable rugged laptop
While some people may feel that their office job is stressful -- and maybe it is -- there are workers in the world that do physically hard work that is much more strenuous. They may work in dangerous and dirty conditions where not only is their health at risk, but so too is their computer. For instance, they may work in a location with tremendous dust, risk of flooding, and falling debris. For these jobs, an extremely rugged laptop or tablet could be needed.
When it comes to rugged computers, Panasonic's legendary Toughbook laptops are always a wise choice. These computers have a reputation for surviving really rough conditions. Today, the company announces its latest bad-ass notebook -- the Toughbook 33. Not only is it a laptop, but a detachable tablet too.

Enterprise IT is back
There is no doubt that public clouds like Amazon AWS, Microsoft Azure, and Google constitute rapidly growing and attractive alternatives to traditional on premise IT operations leading many organizations to conclude that they are "not IT companies" and/or "do not want to be in the IT business."
But few companies can escape the mandate to be present online, to conduct business online, and to deal with partners, suppliers, customers, and employees online. This mandate is causing companies to embark upon initiatives to "digitize" their businesses, which means to implement these crucial business functions in software.

IT leaders want to adopt unified communications systems
Enterprise communications are set to see a major overhaul within the next five years, according to a new report. Research from Fuze found that almost six in ten (59 percent) of companies have prioritized adopting new communication technology.
Based on a survey of 900 IT leaders, the report says 64 percent are looking to cut the number of communications apps to remove complexity. Two thirds (64 percent) are also looking to move their communications completely into the cloud. Sixty-three percent will have adopted a unified communications system by 2022, and 62 percent think video will replace voice-based comms by 2022.

Many senior executives do not know GDPR is coming
More than four fifths (84 percent) of small business owners in the UK, and almost half (43 percent) of senior executives in large companies have no idea what GDPR is and that it’s coming.
That's according to Shred-it’s Security Tracker research, which also found that roughly one in seven (14 percent) of small business owners, and 31 percent of senior executives know what the fines of not complying with the GDPR are.

Get 'Designing UX: Forms' ebook ($30 value) FREE for a limited time
From the words, to how the form looks, and on to interactivity, Designing UX: Forms will show you how to design a web form that works beautifully on mobiles, laptops and desktops.
It’s filled with practical and engaging insights, and plenty of real-world examples, both good and bad.

Does the integration of Microsoft Dynamics 365 and LinkedIn lay the groundwork for a CRM software war?
When Microsoft purchased LinkedIn back in December 2016, many predicted the eventual integration of Dynamics with the world’s primary professional social network. As well as being a valuable business networking tool, LinkedIn is just as useful for cold sales leads and recruitment prospects as it is for connecting people.
With Dynamics 365 designed to combine the company’s CRM and ERP services into a single cloud-based platform, the prospect of having access to nearly 500 million LinkedIn users could be more than enough to sway a new customer towards Microsoft. Dynamics 365 now has a clear advantage, but what impact will this have on the CRM software market when pitted against its competitors?
![ConnectedCar-carDetails-1a[1]](https://betanews.com/wp-content/uploads/2017/05/ConnectedCar-carDetails-1a1.jpg)
The rise of the connected car
Everyone thinks autonomous, self-driving cars are the next big opportunity in the automobile industry -- but it is the connected car that will drive the next major transformation in car owners’ driving experience. Previously, low-bandwidth cellular network connectivity and immature, cobbled-together proprietary technologies prevented automobile manufacturers from fully realizing the potential of the connected car.
However, with the arrival of standards-based, broadband-enabled turnkey connected car platforms, automobile manufacturers can finally make cars an integral part of the Internet of Things (IoT) and offer drivers mobility, preventive maintenance, infotainment and other connected car services that deliver a significantly better driving experience. In addition, the rise of the connected car will be a powerful force driving the development of the technology and infrastructure required to build a real path to a self-driving car future.

IT pros are feeling stressed at work
The road to becoming an IT professional is often thought to be a lifelong process, however, new research claims that this is not the case.
A new report from Spiceworks, entitled "A Portrait of IT Workers," says 41 pe cent of IT pros in the UK consider themselves "accidental" and that they ended up in their career via a "non-traditional" route.

Shocking: Families will spend more than a third of summer staring at screens like zombies
Summertime is almost here, meaning families will begin spending more time outdoors enjoying nature, right? Not necessarily. In modern times, devices seem to rule our attention. Things like computer monitors, televisions, smartphones, and tablets keep our eyes focused on screens like zombies.
To highlight just how bad things have gotten, a new survey reveals that families will spend more than a third of the 2017 summer season with their eyes glued to some sort of screen. To make matters worse, parents say that while they would prefer to do more activities away from devices, outings are far too expensive. A typical weekend family getaway with all things factored in, could average $2,328! Sadly, the overuse of "screens" are negatively impacting the health and behavior of children too.
elementary OS Loki 0.4.1 Linux distro now available for download
Despite the death of Unity, there is still no shortage of desktop environments for Ubuntu. In fact, there are some Linux-based operating systems that exist mostly to provide an arguably better environment and experience. Two good examples of this are Linux Mint and elementary OS. While these distros are more than just Ubuntu with an alternative DE, the UI is largely the star of the show. While Mint caters to folks that have trouble moving beyond the interfaces of yesteryear, elementary instead focuses on a forward-looking experience.
Today, elementary OS Loki -- the latest version of the operating system -- reaches a new milestone. Release 0.4.1 adds many new features, including an updated 4.8 kernel, improved Kaby Lake support, and most importantly, the all-new crowd-funded AppCenter!

Watch today's Google I/O developers conference keynote here, live
Google revealed a lot of new features and products during yesterday’s opening two-hour long I/O keynote, including more about Android O, a stripped down OS for cheap phones called Android Go, an improved way to protect users from bad Android apps, and competition for Siri in the form of Google Assistant for iOS.
That’s not the end of things though, as Google has another keynote today.

OnePlus 5's camera will get a boost from DxO
If it's one thing that consumers expect in a flagship smartphone, it's a great camera. Getting quality photos and videos is one of the main reasons why so many folks spend their hard earned cash on devices like the HTC U11, Samsung Galaxy S8, Apple iPhone 7 or Google Pixel -- and why those devices cost as much as they do.
OnePlus is well aware of this, so it has teamed up with DxO to "enhance [the] photography experience" with the upcoming OnePlus 5. This is one of the few things that the company has revealed about the next flagship killer, aside from the name and the "summer" release date.

Many users rely on VPNs to circumvent geoblocks
A new report has revealed that VPN usage in the UK has increased with almost one in six people now using a VPN alongside their internet connection.
According to YouGov's "Incognito Individual" report, 16 percent of British adults have used either a VPN or proxy server. This up-tick in users trying a VPN was often the direct result of trying access region-locked content or websites. Of those surveyed, 48 percent of respondents admitted to using a VPN or a proxy to access content they would otherwise be unable to view.
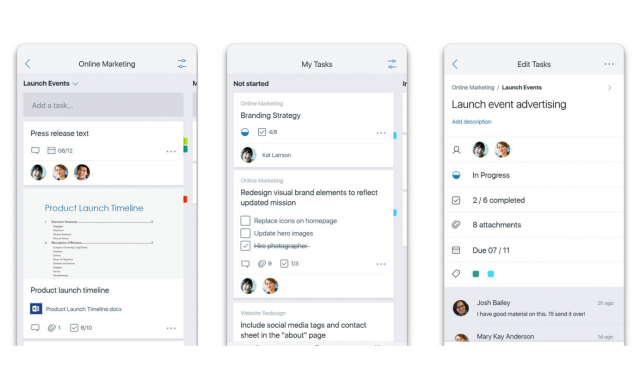
Microsoft Planner now available for iPhone
Office 365 officially received a project management tool, called Planner, in June 2016, but it is not until today that Microsoft introduces an accompanying mobile app. And the platform of choice for the first Microsoft Planner app is iOS.
When Microsoft publicly launched Planner, the software giant said that there will be apps available for Windows and Android devices too, but there is no announcement regarding the support for the other two platforms. Hopefully, that will happen at some point in the near future.

New free plugin filters bot data from Google Analytics
Google's own bot filtering catches only a small percentage of the bot traffic that hits most sites, leading to traffic analysis data being skewed.
Bot detection specialist Distil Networks is launching a free tool designed to remove the bad data created by bots.



