
IP address view helps guard against attacks
Many organizations need help gaining visibility into the IP addresses across their whole environment in order to understand their attack surface.
New enhancements to the Detectify platform include an IP Addresses view, this lets users gain seamless access to a comprehensive list of all IPs associated with their domains.
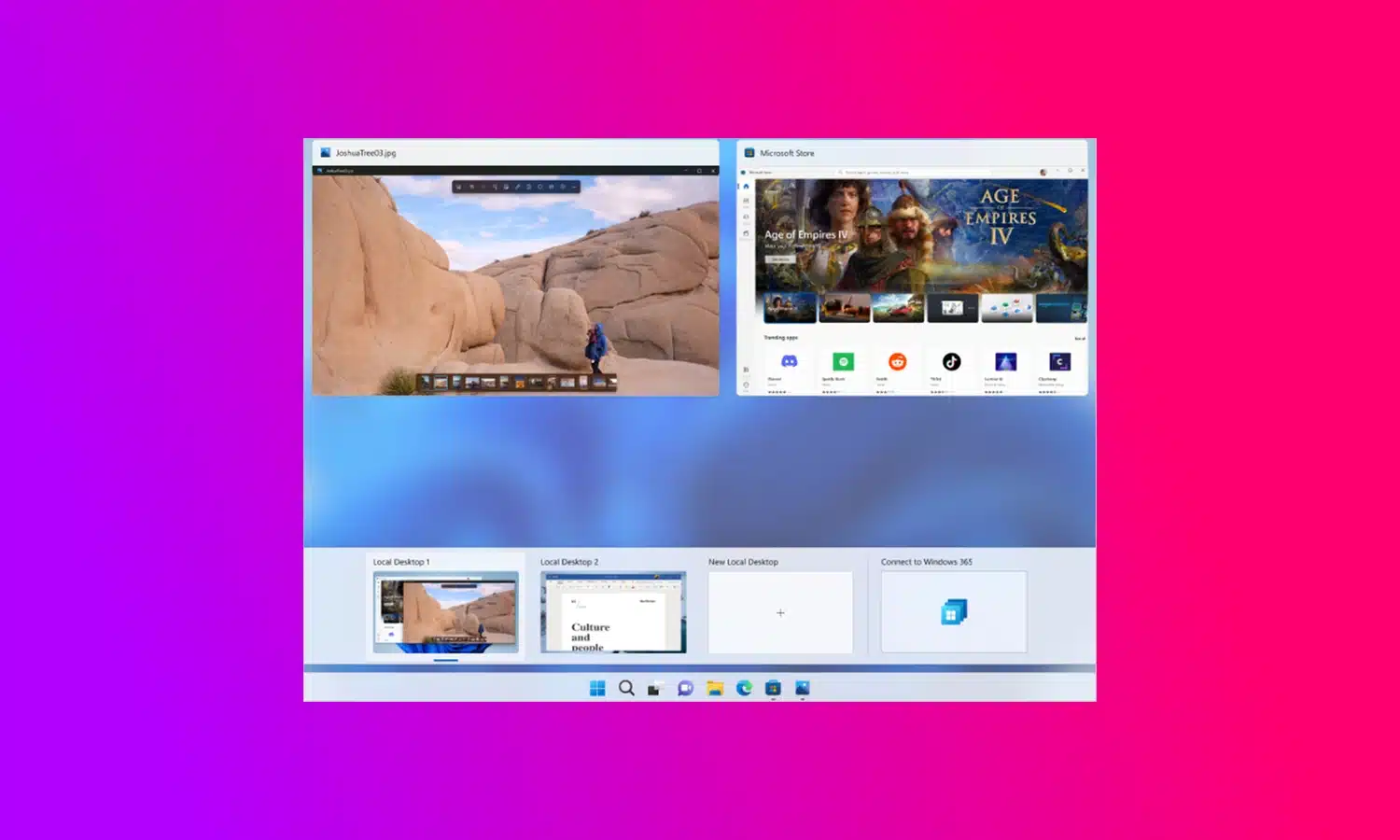
Microsoft releases Windows 365 Switch to simplify moving between a cloud PC and the desktop
Microsoft has announced the availability of the public preview of Windows 365 Switch. The utility makes it easy for Windows 11 users to jump between a Windows 365 Cloud PC and the local desktop.
The company highlights the benefits of the feature to BYOD scenarios, pointing to a seamless experience from within Windows 11 via the Task view feature. Using Windows 365 Switch, switching between a Cloud PC and a local desktop can be achieved with keyboard commands, as well as a mouse-click or a swipe gesture.

Google is switching to weekly Chrome updates to boost security
Google has announced that it will release security updates for Chrome on a weekly basis, doubling the speed with which fixes are delivered to the stable channel.
This will not change the release schedule for significant new versions of Chrome, but it means that users of the browser can enjoy greater security. Google's change in pace is designed to reduce the "patch gap", with the company saying that it treats "all critical and high severity bugs as if they will be exploited".
Microsoft releases experimental Windows 11 Build 25926
Microsoft today releases a new Windows 11 flight for those Windows Insiders who like to live on the cutting edge.
Canary build 25926 comes with new features from the Dev Channel, such as improvements for Windows Ink, advanced screen casting, and local file sharing tweaks, as well as a number of other changes and improvements.

ZOTAC launches Spider-Man-themed MEK HERO G3 A7647, A7646I, and A7646 gaming PCs
ZOTAC is back at it again with its latest unveiling -- the MEK HERO Gaming PCs: G3 A7647, A7646I, and A7646. Each one of these is a powerhouse, perfect for gamers who crave excellent performance without breaking the bank.
The talk of the gaming community will undoubtedly be the Spider-Man: Across the Spider-Verse-themed graphics cards featured in these systems. Powered by ZOTAC GAMING GeForce RTX 4070, 4060 Ti, and 4060, alongside AMD's Ryzen 5 7600 processors, these PCs promise to deliver unparalleled gaming experiences.

AOC AGON PRO AG276QZD OLED gaming monitor has 240Hz refresh rate
AOC has excited the PC gaming community today with its latest display: the AGON PRO AG276QZD. Boasting a 26.5-inch OLED panel, the monitor offers a razor-sharp QHD resolution (2560x1440), a breathtaking 240Hz refresh rate, and a mind-blowing 0.03 ms GtG response time.
The advanced OLED technology incorporated here is something that's hard to find even in the most high-end LCD monitors. Expect immersive gameplay with HDR10 support and perfect blacks for an extraordinary visual experience.

How can Europe create a thriving deep tech economy?
Europe possesses tremendous potential in the field of deep tech. Boston Consulting Group reports that European deep-tech investment has grown by approximately 50 percent annually since 2015. It stands as one of Europe's most promising areas for growth, with leading start-ups in AI, quantum computing, automation, and more.
Nevertheless, Europe faces a dilemma as an increasing number of deep-tech firms redirect their focus to the United States to accelerate their expansion. The decision of chip designer ARM to list on the US Stock Exchange was a particularly painful blow. State-backed initiatives in the US and China present a formidable challenge for European governments, with multi-trillion-dollar investment packages providing significant opportunities for American tech firms. Europe now has an opportunity to foster the growth of deep tech firms by developing a clear strategy that drives innovation and maximizes the continent's existing strength in STEM.

Detection needs to improve to combat evolving malware
Critical infrastructure protection specialist OPSWAT has released its latest Threat Intelligence Trends survey looking at organizations to manage the current threat landscape and how to prepare for future challenges.
It finds that 62 percent of organizations recognize the need for additional investments in tools and processes to enhance their threat intelligence capabilities. Only 22 percent have fully matured threat intelligence programs in place though, with most indicating that they are only in the early stages or need to make additional investments in tools and processes.

Get 'Hacking For Dummies, 7th Edition' (worth $18) for FREE
Your smartphone, laptop, and desktop computer are more important to your life and business than ever before. On top of making your life easier and more productive, they hold sensitive information that should remain private. Luckily for all of us, anyone can learn powerful data privacy and security techniques to keep the bad guys on the outside where they belong.
Hacking For Dummies takes you on an easy-to-follow cybersecurity voyage that will teach you the essentials of vulnerability and penetration testing so that you can find the holes in your network before the bad guys exploit them. You will learn to secure your Wi-Fi networks, lock down your latest Windows 11 installation, understand the security implications of remote work, and much more.

Demonstrating application security is becoming key to closing business deals
According to a new report, 84 percent of CISOs say that they are called into sales engagements related to closing sales of their company's products and services, highlighting the connection between AppSec and business growth.
The study from Checkmarx also reveals that 96 percent of CISOs say their prospects consider the level of application security of their organizations when making purchase decisions.

TEAMGROUP launches T-CREATE EXPERT CFexpress memory cards
TEAMGROUP has introduced not one but two new memory cards under its creator-centric sub-brand, T-CREATE: the T-CREATE EXPERT CFexpress Plus Type B and T-CREATE EXPERT CFexpress Type B Memory Cards.
Designed for the sophisticated requirements of DSLR, cinema, and high-end SLR cameras, these cards will absolutely meet the needs of creators needing continuous high-speed shots. Whether shooting 4K or 8K RAW high-bitrate videos for extensive periods, these cards should have no trouble keeping up.

UK Electoral Commission systems breached for over a year
Systems at the Electoral Commission, the body which oversees elections in the UK, have suffered a breach exposing electoral registers which hold the data of anyone registered to vote between 2014 and 2022. The Commission’s email system was also exposed in the breach.
In a statement on its website the Commission says it identified the incident in October last year but that systems were accessed as long ago as August 2021.

Will CISOs become obsolete in the future?
Navigating the complexities of today’s digital landscape, it's clear that cyber security can no longer be the sole accountability and responsibility of one person -- the CISO. As cyber threats evolve, becoming more frequent and sophisticated, a single individual can't feasibly manage it all. As a result, and at some point in the future, we may dare to consider that the traditional CISO role might eventually become obsolete as business units become secure-by-design.
We need to pivot. Rather than placing the weight of managing an organization's entire security on the shoulders of one person, we need to integrate cyber security throughout every layer of our operations. This means moving towards a world where every business unit and every employee in an organization understands and owns their role in maintaining cyber security.

How AI is going to shape the developer experience [Q&A]
Recent developments in generative AI have led to a good deal of debate around whether jobs are at risk. Since new AI applications like OpenAI Codex and Copilot can write code, developers could be among those under threat.
We spoke to Trisha Gee, lead developer evangelist at Gradle, to find out more about how AI is likely to change the way developers work.

All Windows 11 users should install the KB5029263 update as soon as possible
Microsoft has released a large new cumulative update for Windows 11 in the form of the KB5029263 update.
As this release fixes a series of security issues in the operating system, everyone running Windows 11 22H2 should install it as soon as possible. KB5029263 is a mandatory update so it will be installed automatically -- eventually -- but it is important enough to justify taking manual action to ensure you have it immediately.



