
Apple AirPods Max are wireless headphones for rich people that don't value money
Are you rich? Me neither. While I am not poor, I work hard for my money, and I am not about to waste it on frivolous things. So when I saw the price of Apple's new AirPods Max wireless headphones, I nearly fainted. Are you ready for this, folks? The company is asking $550! Seriously. Oh, Apple...
Don't get me wrong, they actually look like nice over-ear headphones. I really like the design; they look well-made and comfortable. And of course, Apple has all kinds of fancy technology to try and justify the asking price. But let's cut out the marketing for a moment and be honest -- you'd be a fool to spend so much money. Hell, these beautiful Audio-Techinca Bluetooth headphones can be had for less than a third of the price!
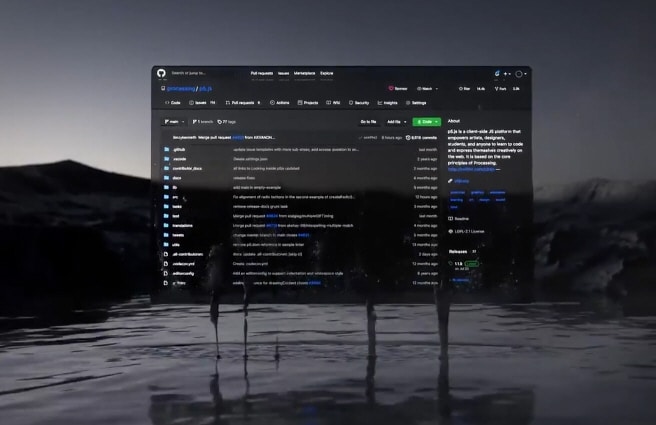
GitHub now has a cool dark mode -- here's how to apply it
As part of GitHub Universe week, the Microsoft-owned software code hosting platform has announced a number of changes, improvements and new features. These include GitHub Sponsors for companies, auto-merge pull requests, discussions for all public repositories, and dependency review.
For a lot of people though, the big news is GitHub now has a stylish dark mode and you can enable it today.

Linux Foundation launches open source identity and access management platform
Verifying digital identity is fundamental to building trust in online security and conducting commercial and personal transactions safely. But it can also prove a performance headache for businesses.
Non-profit organization, The Linux Foundation, is today announcing the launch of the Janssen Project, a cloud native identity and access management software platform that prioritizes security and performance.

User experience wins out over security
While security is clearly a concern for IT professionals, providing the best application experience is more important, with 87 percent saying that security will need to better support the user experience.
This is among the findings of a new study of IT decision makers from Menlo Security, which shows slow access speeds (46 percent), poor connectivity (33 percent), no/ loss of access to resources (28 percent), downtime (27 percent) and decreased productivity due to increased security (27 percent) are all experience-related issues cited by respondents.

Ashampoo Burning Studio 22 adds H.265 support, improves metadata search and retrieval
Ashampoo Technology GmbH has released Ashampoo Burning Studio 22, a major new version of its disc-burning suite for Windows users.
Burning Studio supports the creation of video, audio, and data discs, including DVDs and Blu-rays. There’s also built-in support for ripping CDs to hard drive and creating disc image files such as ISO and BIN. Version 22 adds several new features, including support for H.265-encoded video, an improved metadata search and retrieval tool, and support for customizable desktop shortcuts.

DevSecOps adoption grows worldwide despite security concerns
DevSecOps methodology is an important, rapidly growing trend worldwide, with 63 percent of respondents to a new study reporting they are incorporating some measure of DevSecOps into their software development pipelines.
The survey of 1,500 IT professionals conducted by the Synopsys Cybersecurity Research Center (CyRC) and Censuswide also shows 33 percent have DevSecOps in a mature or widely deployed state in their business.

Open source developers spend less than three percent of their time on security
The latest FOSS (Free and Open Source Software) contributor survey from the Open Source Security Foundation (OpenSSF) and the Laboratory for Innovation Science at Harvard shows respondents spend on average, just 2.27 percent of their total time on security and express little desire to increase that time.
The survey of almost 1,200 respondents working on FOSS software shows the majority of respondents (74.87 percent) are already employed full-time and more than half (51.65 percent) are specifically paid to develop FOSS.

ID fraud surges during pandemic as more people turn to crime
Over the past year the average identity document (ID) fraud rate has increased by 41 percent over the previous year and first-time fraudsters appear to be more prevalent.
A new report from identity verification and authentication provider Onfido shows activity peaked in July and August. But with large parts of Europe encountering a 'second wave' and re-entering lockdown, coupled with the spike in online activity for the holiday shopping season, Onfido predicts fraud rates will start to climb again as the year closes.

Early adopters of iOS 14.2 report iPhone battery drain
It's only a matter of weeks since Apple agreed to pay out $133 million following the batterygate scandal that saw the performance of older iPhones being throttled. Now it looks as though the company could have another battery issue on its hands.
An increasing number of users who jumped to install iOS 14.2 are reporting that their iPhones are losing battery power very quickly. A similar problem is also being reported by people who have installed iPadOS 14.2.

Apple Music finally comes to Google Assistant-enabled devices like Nest Audio
Believe it or not, you really can use just some Apple devices without buying into the ecosystem entirely. Using myself as an example, I own an iPhone and iPad, but I don't own a Mac -- I instead use Linux and Windows on the desktop. I also don't have an Apple Watch or AirPods. I do, however, own a couple of Apple TV boxes for media.
For smart home assistants, I chose Google rather than the Siri-enabled HomePod. The problem, however, is I am a hardcore Apple Music user, and while I can use that service on pretty much any platform, it has not been available on Google Assistant-enabled devices such as the Nest Audio or Nest Hub. This means I haven't been able to call upon Google with my voice to play my favorite tunes from Apple Music. Thankfully, this finally changes today!

WinRAR 6.0 arrives with bug fixes and a host of new features
When it comes to compression software, there are two names that tend to spring to mind -- WinZip and WinRAR. Which you are more familiar with will depend on what you are using your compression software for, but over the years WinRAR has earned itself a place in many people's hearts.
25 years after its first release, WinRAR 6.0 is now available. There is, of course, support for the incomparable RAR format, but also for .zip, .tar, .jar, .lzh, .iso and more. This latest release includes a number of important changes and additions such as improved handling of extracting multiple archives simultaneously, and the addition of new command line switches to give you greater control over the extraction process.
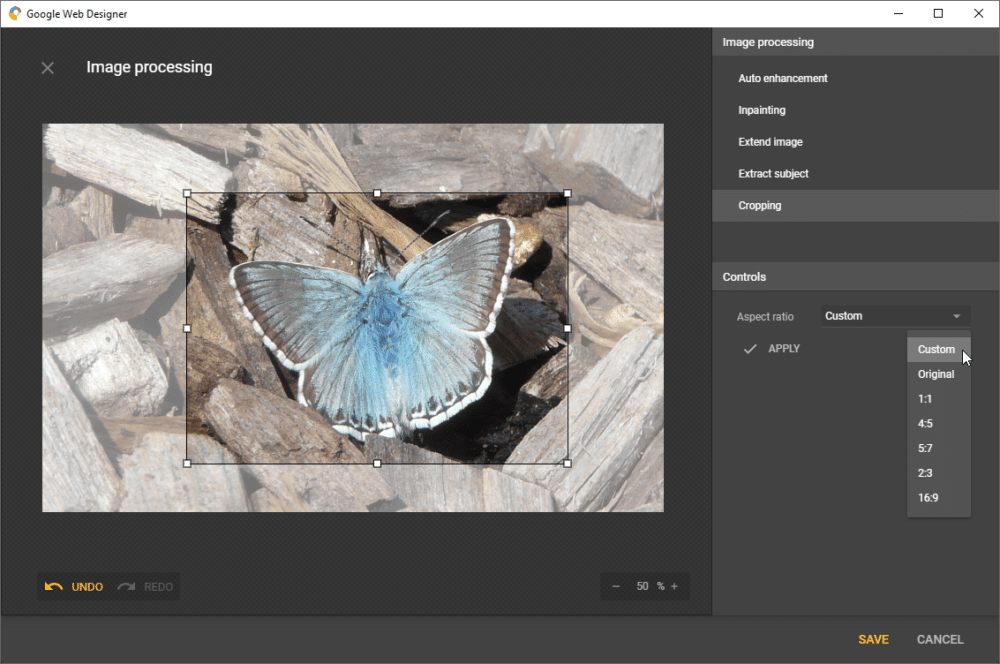
Google Web Designer 10 adds cropping tool to image processing dialog, expands snapping mode options
Google has released Google Web Designer 10.0 in what appears to now be a regular quarterly update. The HTML-5 content-producing tool for Windows, Mac, and Linux is a popular choice for producing all kinds of web content thanks to its user friendliness and helper tools.
Version 10.0 offers four new features and a slew of improvements and fixes, chief of which include the ability to crop images within the image processing dialog, plus new snapping modes.

5G adoption brings new security risks
Most professionals say their organizations are concerned about cybersecurity risks related to 5G adoption according to a new poll from consulting firm Deloitte.
The findings show those at organizations planning to adopt 5G in the year ahead are slightly more worried (80.7 percent) than those currently using 5G (76.4 percent).

Education sector not prepared for cybersecurity in the age of COVID
New research from Malwarebytes reveals that 46.7 percent of IT decision-makers in schools say that no additional requirements have been introduced for students, faculty, or staff who connected to the school's network remotely during the pandemic.
In addition 50.7 percent of IT decision-makers surveyed say that no one was required to enroll in cybersecurity training before the new school year began
PowerToys v0.28 has a great new utility for Windows 10
With the recent release of PowerToys v0.27, Microsoft managed to both excite and disappoint users. While there was a lot to explore and enjoy in that build, the newly released PowerToys v0.28 is even more impressive.
What is there to look forward to? Well, the arrival of the lauded video conference mute feature is something that people have been waiting for for a while... and now it's finally here.


