
Shh! Logitech releases MK295 Silent Wireless Keyboard and Mouse Combo
If you are a computer nerd like me, you probably play around with your PC day and night. After a few bottles of Mountain Dew (or other caffeinated beverage), you may find yourself wide-eyed at 3 am typing away. If you live alone, that may be OK. If you are married or still live at home with your parents, however, there 's a good chance your typing and clicking can be quite loud and annoying. Hell, you might even accidentally awaken your family from time to time. This can lead to people being very angry with you.
Luckily, Logitech has a new product that should help you to be quiet when using your PC. Called "MK295 Silent Wireless Keyboard and Mouse Combo," the name pretty much explains exactly what it is -- a wireless keyboard and mouse with silent switches. The MK295 keyboard provides up to 3 years battery life from three AAAs, while the mouse lasts a year and a half with a single AA. Not only should the combo be ideal for home use, but business too -- it should make for a quieter office experience.

Get 'Microsoft Excel 2019 Bible' ($35.99 value) FREE for a limited time
Whether you are just starting out or an Excel novice, the Microsoft Excel 2019 Bible is your comprehensive, go-to guide for all your Excel 2019 needs. Whether you use Excel at work or at home, you will be guided through the powerful new features and capabilities to take full advantage of what the updated version offers.
Learn to incorporate templates, implement formulas, create pivot tables, analyze data, and much more.

Satechi unveils Apple-focused Quatro Wireless Power Bank
There are many power banks on the market these days, and for the most part, they are all very similar. These devices are essentially big batteries with USB ports designed to charge up your smartphone multiple times when on the go. When you can't find an outlet, these power banks can be a godsend, but also, they can be a critical tool during a power outage. If you live in an area that gets hit by hurricanes and/or tropical storms, you should absolutely own at least one of them -- a few if you have a family.
Today, Satechi unveils a new such product that is very Apple-focused. Called "Quatro Wireless Power Bank," it has a dedicated Apple Watch charger, Qi wireless charging (perfect for compatible AirPods), and both a USB-A and USB-C port. Not only is it designed with Apple devices in mind, but its overall aesthetics seem inspired by the iPhone-maker too. It features a matte black design, but the outer rim is surrounded by a beautiful shiny metal. It weighs 0.58 lbs and its dimensions are 6.4 x 2.9 x 0.7 inches.

New development environment streamlines the creation of business apps
Low-code techniques help businesses to develop applications quickly, but in some cases they can lead to added complexity.
With the launch of OXIDE, an Integrated Development Environment (IDE), JourneyApps is seeking to combine the speed and efficiency of low-code platforms with the flexibility and power of professional development, all in a single platform.

Why vishing is the new phishing and how to guard against it [Q&A]
We're all familiar with the menace of phishing but, particularly following the recent Twitter attack, other methods of stealing credentials have been on the rise.
These include 'smishing' (phishing via SMS) and 'vishing' (phishing by voice call). We spoke to Ed Bishop, CTO at email security company Tessian to find out how businesses can identify vishing and smishing attacks, how the attacks work, and how companies can protect their employees.

New platform helps businesses get the most from data lakes
Data is key to the competitiveness of modern enterprises, but the quality of that data determines how useful it is.
Customer data platform Segment is launching a new data architecture product built specifically to help companies deliver better customer experiences. Segment Data Lakes gives companies a foundation to produce advanced analytics, uncover customer insights, and power machine learning and AI initiatives.

Hackers could use Windows 10 themes to steal passwords
People like to be individuals, and in the computing arena one way to be a little different is to change the look of Windows by using themes. But a security researcher has warned of a technique that could be exploited by hackers to trick users into divulging their Windows login details when applying a theme.
Malicious theme packs can be used to execute a "pass-the-hash" attack which sends passwords to a remote server. The specially designed themes are easy to create, andthe way the credential stealing attack works will fool many people -- but there are protective measures that can be put in place.

Zorin OS 15.3 Linux distro can replace buggy Microsoft Windows 10 on your PC
So, here we are in September, six months removed from the release of Zorin OS 15.2. A lot has happened since March -- a pandemic, civil unrest, and out-of-control wildfires are just a few of the things that have made this year quite stressful. Not all is bad, however, as we have football starting up this week -- a great distraction to life's stresses.
Today we also get some big news on the Linux front -- Zorin OS 15.3 is finally here. True, it is just a point release, but once again, it should be the best version of Zorin yet. While great for Linux experts, I highly recommend it to those looking to switch from the buggy and much-maligned Windows 10. Zorin OS is a stable and well-designed operating system that is reminiscent of Windows. And so, its familiarity is a great way for Windows users to comfortably experience Linux. Version 15.3 comes with LibreOffice 6.4.6, which is a great alternative to Microsoft Office.

60 percent of emails in May and June were fraudulent
The COVID-19 pandemic has seen a spike in scams, phishing and malware across all platforms and attack vectors. The latest mid-year threat landscape report from Bitdefender shows that in May and June, an average of 60 percent of all received emails were fraudulent.
In addition there’s been a five-fold increase in the number of coronavirus-themed attacks and a 46 percent increase in attacks aimed at home IoT devices.

Remote work puts extra stress on SMB security teams
Smaller businesses are having to do more with less in terms of security, a situation made worse by the coronavirus pandemic.
The annual SMB IT Security Report from Untangle shows that 38 percent of SMBs are allocating $1,000 or less to their IT security budget, compared to 29 percent in 2019 and 27 percent in 2018.

If you don't want to be Microsoft's guinea pig, pause Windows Updates
We have written a lot about Windows 10 here on BetaNews, and many of these articles have been about problems introduced by new updates. For some time now it has felt as though the updates and patches that are released have not been fully tested, and users of the operating system are being used as guinea pigs when Patch Tuesday rolls around each month.
There is, of course, the argument that Microsoft has an impossible task when it comes to ensuring that patches and updates do not cause problems for people with near unlimited combinations of hardware and software. But that's little consolation if it's your system that gets borked by a patch.

Vivaldi 3.3 unveils new screen-break feature alongside customizable Private Window theme
Uniquely customizable browser Vivaldi gets another major update with the release of Vivaldi 3.3 for Windows, Mac, and Linux. The new release adds a major new Break Mode feature to encourage regular screen breaks.
The new release also offers users the ability to create and apply custom themes to their Private Windows sessions -- a first among web browsers -- as well as several improvements to the Address Bar to improve security and navigation. Full-Page blocking is now supported in the Tracker and Ad Blocker tools, while users can now drag and drop Speed Dials to folders on the Vivaldi 'desktop' on the user’s home page.
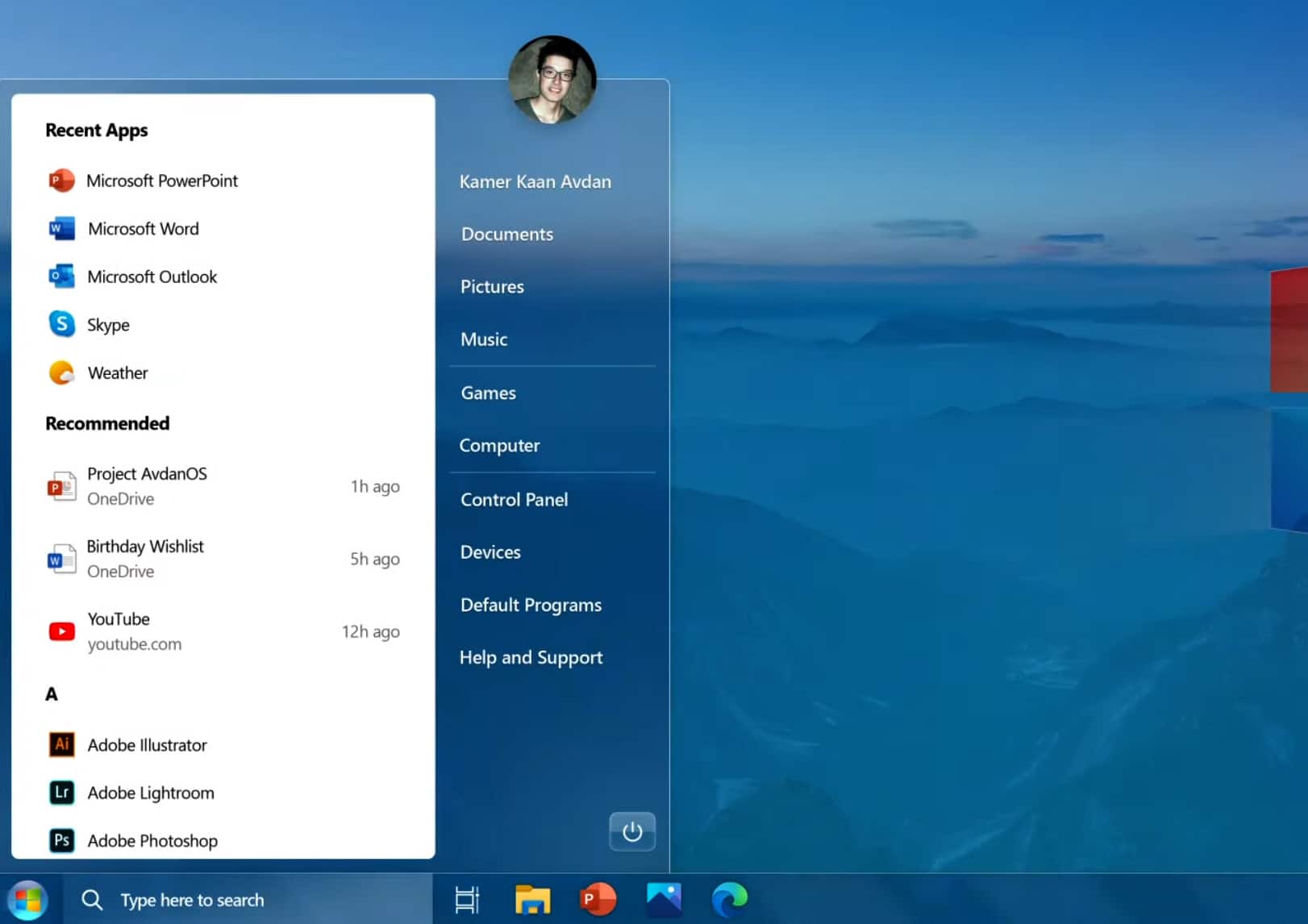
Windows 7 2020 Edition could be the perfect Microsoft operating system
Windows 10 is a good operating system, for the most part, but it’s not without its problems -- I covered just some of these here on the eve of its 5th birthday at the end of July. It seems every new update Microsoft rolls out these days introduces fresh annoyances. No wonder millions of people are still sticking with Windows 7, even though that OS is no longer supported.
For many people, Windows 10 is the operating system they have to use, but not the one they want to. With that in mind, it's not hard to see the appeal of this remastered Windows 7 2020 Edition.

POCO X3 NFC Android smartphone is super affordable and loaded with killer features
POCO -- a sub-brand of Xiaomi Inc. -- is not a well-known name in the USA, but in China and other parts of the world, it is quite popular with Android enthusiasts. The young Chinese brand is synonymous with affordable smartphones that have impressive features. This is important, as it allows regular people to buy respectable Android devices without breaking the bank. Sadly, companies such as Samsung, are pricing their devices well out of reach of the common man. Quite frankly, even if you can afford it, spending more than $1,000 for a smartphone is rather foolish.
With all of that said, today, POCO unveils its latest affordable Android smartphone. Called "X3 NFC," it comes loaded with killer features such as a massive 5,160mAh battery with 33W fast charging. It is optimized for gaming with a special GPU and advanced cooling. Despite being a "mid-range" phone, it has a very impressive display with 120Hz refresh and a 240Hz touch sampling. The POCO X3 NFC even has a quad-camera array (with flash), so it should take impressive photos. And yes, it has a 3.5mm headphone port too! Sadly, all is not perfect -- it does not support 5G.

Microsoft releases KB4497165 and KB4558130 microcode updates for Windows 10 to fix Intel security flaws
Earlier in the year, Intel announced that it had completed software validations on fixes for a series of security flaws affecting many of its processors discovered a couple of years ago. Now Microsoft, in conjunction with the chip-maker, released microcode updates for Windows 10 to fix these issues.
The four problems are connected to the now-infamous Spectre and Meltdown flaws from 2018. They relate to problems with the speculative execution function of many chips, and could allow for sensitive data to leak.


