
New store provides a one-stop-shop for privacy apps
When choosing data privacy applications in the past businesses have had to choose between a broad spectrum of capabilities of a focus on particular issues.
Now though SAP-backed data discovery and intelligence company BigID is launching a new Application Marketplace that allows organizations to build their optimum data solution, choosing specific capabilities that best fit their needs.

The role of SASE in securing the modern workforce [Q&A]
Digital transformation combined with a shift to more remote working has presented considerable challenges for enterprises when it comes to securing their systems.
One of the technologies being increasingly used to enable remote access is Secure Access Services Edge (SASE). We spoke to Anurag Kahol, CTO and co-founder of cloud security company Bitglass to find out more about SASE and how it can help businesses deliver their transformation projects.

Microsoft Family Safety app for iOS and Android helps parents monitor their kids
Nowadays, the internet isn't just a part of life -- it is life. While that is a rather cold reality, the fact is, most of us are glued to our devices these days. Sadly, this includes children too. Long gone are the days of boys playing baseball or girls skipping rope outside. Instead, it is all about TikTok, Instagram, and SnapChat. Kids don't want to be professional athletes or rock stars, instead wanting to be a famous YouTuber or Twitch streamer.
And so, parents have their hands full when it comes to monitoring their child's online activity. Back in the day, a family might have one desktop in the home, making it easy to know who is online and when. With tablets and smartphones, however, parents are often in the dark. Well, Microsoft has a new app that will empower parents in their quest to monitor their kids. Called "Microsoft Family Safety," it is available for both Android and iOS.

Plugable launches affordable USBC-MD103 USB-C Multiport Adapter for Windows 10, macOS, Linux, and iPad Pro
USB-C is definitely the connector of the future, and many manufacturers have embraced it as the only port on their laptops. Apple MacBook and the Dell XPS 13, for instance, only have Thunderbolt 3, which uses USB-C. If you want to connect legacy devices (USB-A, Ethernet, HDMI, etc.) you will need to use dongles or docks. Some companies include dongles in the box, but as you can expect, Apple does not.
Actually, Apple is happy to sell you its USB-C Digital AV Multiport Adapter for a sky-high $69! That is highway robbery. Almost 70 bucks for a USB-A port, HDMI, and power delivery pass through? Insanity. Thankfully, Plugable is today launching a very similar product (nearly identical) for a fraction of the cost! And not only will it work with an Apple MacBook or iPad Pro, but Windows 10 and Linux computers too. The HDMI port is capable of 4K, the USB port is 3.0 speed, and the USB-C power delivery port supports up to 60W.

Parallels Access 6.0 unveils Remote Help support, while Parallels Toolbox 4.0 adds five new tools -- including screen-break scheduler
Parallels Access 6.0 adds a new Remote Help feature alongside Bluetooth input device support on the latest iPads, as well as adding OneDrive and Google Drive support to the Android app.
Parallels Toolbox 4.0, meanwhile, gains several new tools, including one to help schedule break times, a unit converter and enhanced search tool.

New solution delivers zero trust for multi-cloud and hybrid access
As more organizations move their operations to the cloud and networks become more fragmented, ensuring safe, secure access to systems becomes more difficult.
Secure access specialist Pulse Secure is launching a new Pulse Zero Trust Access (PZTA) solution. A cloud-based, multi-tenant secure access platform that enables organizations to provide users with easy, anywhere access to multi-cloud and data center applications.

IT gets bigger budgets and more respect as a result of COVID-19
A survey of 153 IT decision makers across the UK and US finds that 43 percent of IT leaders feel more respected by their business counterparts since the start of the pandemic.
The research by digital transformation company Ensono also reveals that one in three have been given more scope to define IT spend and a third of organizations are looking to increase IT budgets.

Logitech G announces the PRO X Wireless LIGHTSPEED Gaming Headset
When you are a serious gamer, including those that play competitively, your gear really matters. Players need to carefully select high-end mice, keyboards, headsets, and more if they are going to compete -- especially on a professional level. Many elite gamers choose Logitech G for their hardware needs, and it is not hard to see why -- Logitech's gaming brand has consistently released high-quality gear for many years.
Today, Logitech G announces the PRO X Wireless LIGHTSPEED Gaming Headset. As the name suggests, this wireless headset utilizes Logitech's excellent LIGHTSPEED technology. If you aren't familiar, LIGHTSPEED is the company's proprietary low-latency wireless solution that minimizes many of the complaints gamers have about Bluetooth. If you are a gamer and you want wireless gear, LIGHTSPEED is where it's at.

Security professionals don't have the tools they need to detect threats
A new survey of over 300 security professionals reveals that 93 percent feel they lack the tools to detect known security threats, and 92 percent say they are still in need of appropriate preventative solutions to close current security gaps.
The study from security operations center specialist LogRhythm also finds that 75 percent of security professionals now experience more work stress than they did just two years ago.

Microsoft updates Remote Desktop app for Android with Virtual Desktop support
Microsoft has released a key update to its Remote Desktop app for Android. The app, which allows for the remote use of computers running Windows 10 Pro and Enterprise, Windows 8.1 and 8 Enterprise and Pro, Windows 7 Professional, Enterprise, and Ultimate, and Windows Server versions newer, now features full support for Virtual Desktops.
The update also brings the Android app in line with the iOS and macOS version, so all three versions of the app now use the underlying RDP (Remote Desktop Protocol) core engine. The latest version of the app also brings support for Android TV devices, but there's even more to look forward to.
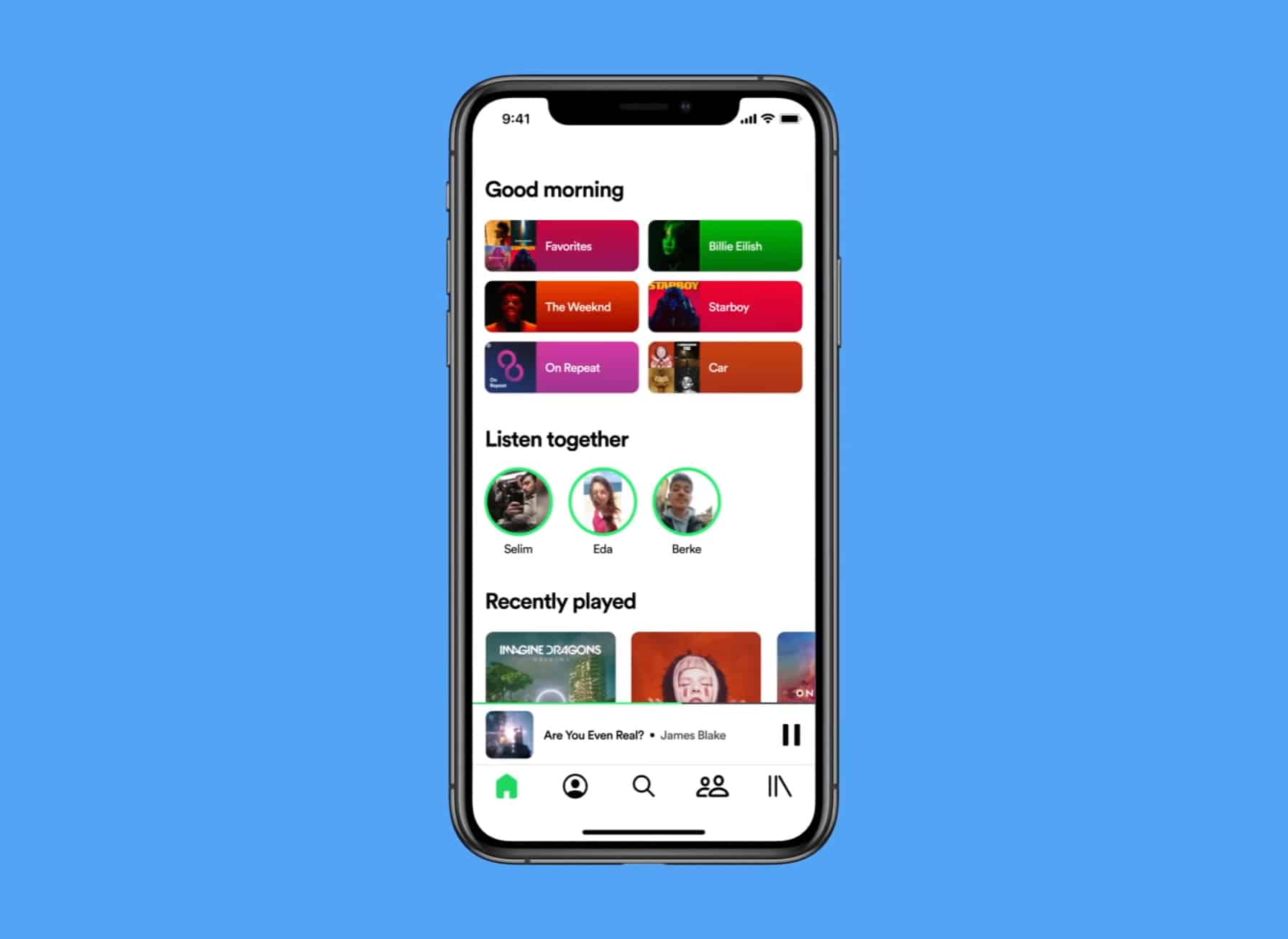
This is the Spotify mobile experience we need
Spotify revolutionized how we consume music, and although it faces strong competition from the likes of Pandora, Apple and Amazon, it remains the number one audio streaming service by some margin, with 286 million active users a month.
That doesn’t mean it’s perfect though. Personally I’m not a lover of Spotify’s look, and I think the mobile experience could certainly be a lot better. I’m definitely not alone here.

Enterprises press ahead with modernizing applications
A new study from cloud solutions provider AHEAD shows that most enterprises are committed to modernizing their application software portfolios, but there are still challenges to overcome and improvements to be made.
Based on a survey conducted by Hanover Research the report shows only 37 percent of respondents are very satisfied with how fast they are currently delivering new software or new features.

BenQ launches the portable and rugged Android-powered GS2 outdoor projector
Right now, we are in the middle of he pandemic, but also, we are in the middle of summer. And so, people are looking for ways to have fun outdoors while social distancing. For this, some folks are going camping in the woods or spending time in their own backyard.
One thing that has exploded in popularity is using a projector to watch a film outdoors. Today, BenQ launches a beautiful projector that should be perfect for outdoor movie watching -- whether in the woods or in your yard. Called "GS2," it is a portable and rugged Android-powered outdoor projector. The beautiful mini projector is IPX2 rated and features 3 hours of battery life. While it runs Android for media apps (Netflix, Hulu, YouTube, and more), the version of the operating system is shockingly old -- 6.0 Marshmallow, which was released in 2015!

Garmin confirms a ransomware attack took its systems offline
As expected, Garmin has confirmed that the ongoing outage that affected many of sport and fitness firm's services was the result of a cyberattack.
In a brief statement the company explains that the attack encrypted some of its systems on July 23, and then goes on to explain what happened and what was affected:

Forcepoint SASE solution helps protect enterprise clouds
Secure Access Service Edge (SASE) technology is increasingly being used to enable secure and fast cloud adoption, helping ensure both users and devices have safe cloud access to applications, data and services from anywhere.
Cybersecurity company Forcepoint is entering this market with a new suite of SASE solutions, including a Cloud Security Gateway and zero trust Private Access features.



