
New hardened images set to improve container security
A typical container image carries over 600 known vulnerabilities, nearly half of them years old and for Java workloads, the risk is particularly acute.
To address this BellSoft is announcing Hardened Images, a tool for enhancing the security and compliance of containerized applications in Kubernetes.

Apple bows to Chinese pressure to remove queer dating apps from its App Store
The Chinese government applied pressure on Apple to remove the two biggest queer dating apps from its App Store in the country, and the iPhone-maker has rolled over and done just that.
The two apps – Blued and Finka – have previously been named as being the first and second most popular dating apps for members of the LGBTQIA+ community in China. Some sources suggest that their appeal spread globally.

Companies forced to make financial changes after a cyberattack
A new study from Cohesity finds 70 percent of publicly traded companies have reported adjusting earnings or financial guidance after a cyberattack.
Among the impacts 68 percent say they observed an impact on their stock price, while 73 percent of privately held firms redirected budgets from innovation and growth initiatives.

Would you swap personal information for a bargain?
Ahead of Black Friday a new study shows that, while 95 percent of Americans are concerned their data could end up in a breach, 78 percent are still willing to share personal information for discounts, perks, or free shipping.
The report from Incogni, based on a study of over 1,000 US adults, finds that volunteering personal information for discounts or access to content and rewards has become so routine that few likely consider the implications before doing so.

Why it's time to ditch the VPN and embrace RPAM for secure remote work [Q&A]
As much of the workforce takes time out from the office for the holidays, employees, contractors and third-party vendors continue to log in remotely from holiday homes, airports or hotels, far from the traditional corporate environment.
This surge in remote work access inevitably heightens security risks. For IT and security teams already managing a sprawling attack surface, reduced visibility and control create a challenge that legacy tools like Virtual Private Networks (VPNs) were never designed to address.

Tuxedo InfinityBook Max 15 Linux laptop offers desktop-grade power
Tuxedo designs and builds Linux computers. The InfinityBook Max 15 is the German firm’s newest Linux laptop, and it arrives with Wayland as the standard graphics system, even on models that use Nvidia GPUs.
The new laptop is the company’s third model to use Wayland by default, following the Polaris 15 Gen5 and Gemini 17 Gen3, which both faced issues running X11 under Ubuntu and Tuxedo OS.

New Gcore platform simplifies enterprise AI deployment
Businesses are keen to deploy AI but doing so across hybrid and regulated environments, and managing the resulting workloads, remains deeply complex.
This is why Gcore is launching Everywhere AI, a deployment platform that allows enterprises to deploy, scale, and optimize AI workloads flexibly across on-premises, hybrid, and cloud environments while maximizing performance, efficiency, and revenue.

Free tool fixes Windows 10 ESU registration issues and restores Microsoft security updates
Microsoft officially ended support for Windows 10 last month, leaving most systems without regular updates. For users in the European Union, the European Economic Area, and Switzerland, the software giant offers free Windows 10 ESU (Extended Security Updates) patches to keep PCs protected. Unfortunately, for many who qualify, the ESU registration option doesn’t appear in Windows Update.
The missing registration prompt issue is typically the result of incomplete system updates, disabled Windows services, or files required for the registration process going AWOL. If your Windows 10 installation isn't fully up to date or certain services aren't running, the ESU registration won't automatically appear.

Why enterprises need to fix their data before AI breaks their business [Q&A]
There’s been a boom in AI in recent years and the technology has found its way into more and more areas of commercial enterprise.
But in the rush to adopt AI is the quality of the underlying data being ignored? We spoke to Krishna Subramanian, co-founder and COO of Komprise to find out why good data governance is key to implementing AI successfully.
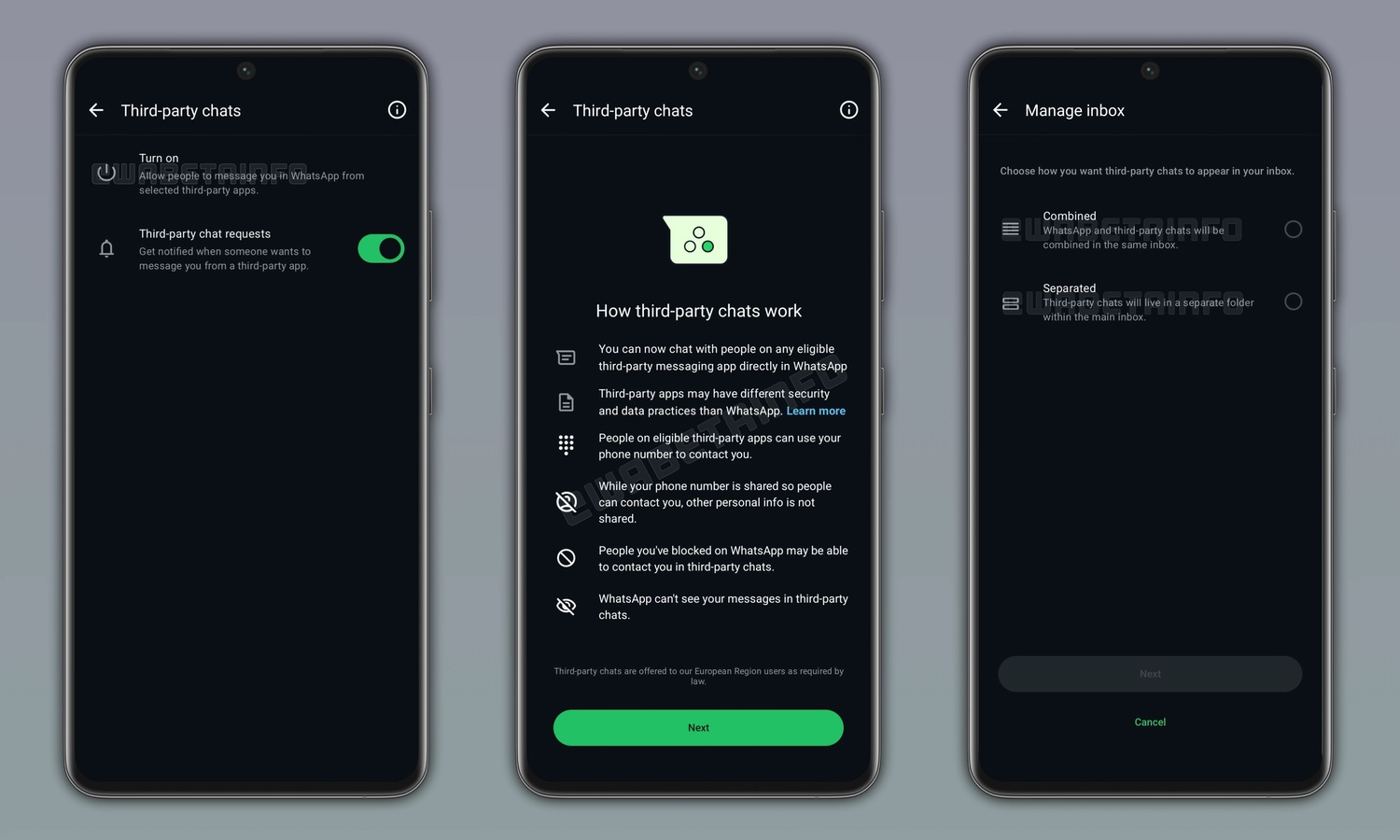
WhatsApp will soon support third-party chats
The wide range of messaging apps now available is great in terms of choice, but it also means that you almost certainly have contacts scattered across a number of different platforms. In turn, this means that you have had to install a large number of app in order to ensure that you are able to contact everyone that you need to.
But this could soon be changing for WhatsApp users. Several years ago, there were various messaging apps that could be used to conduct cross-platform chats, so you could use one app instead of several. This looks to be the direction in which WhatsApp is heading.
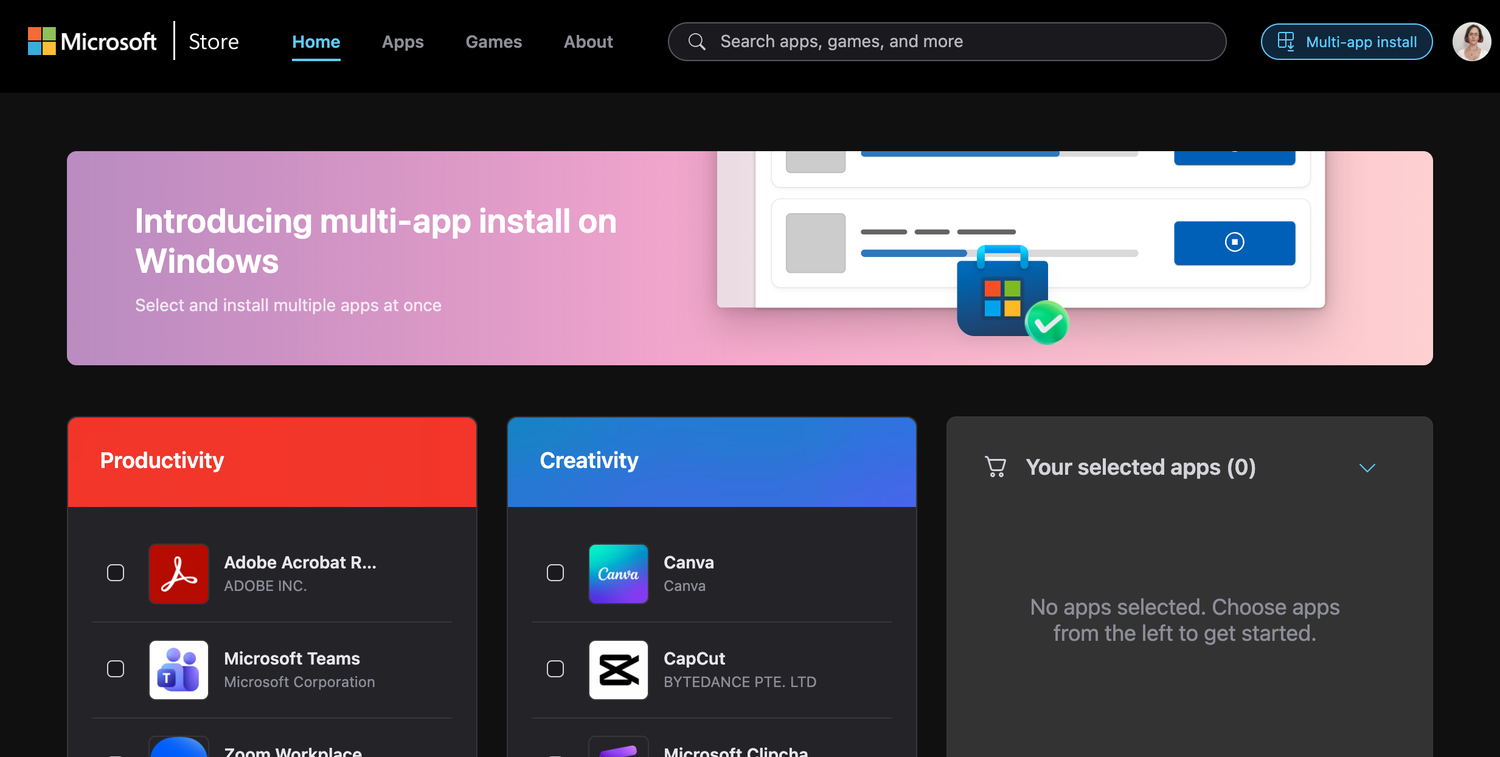
You can now install multiple apps simultaneously from the Microsoft Store
Microsoft has very quietly introduced a multi-app installer option for the Microsoft Store. Working in a similar way to third-party package installers, the new feature makes it possible to add several apps to a “shopping list” and then install them in one fell swoop rather than individually.
There are a few interesting things about this, not least of which is the fact that Microsoft has not made a big announcement about this handy new option. Another curiosity is that the option is only available for some users of the web-based version of the Microsoft Store.

Spotify Wrapped is now a weekly rather than annual event
While it would be an exaggeration to say that Spotify Wrapped is the highlight of the year, the annual look back at what you’ve listened to over the past year is an interesting bit of fun. Sadly, the wait between one Wrapped and the next is incredibly long, but this is changing.
Spotify has announced the introduction of new listening stats which will be updated on a weekly basis. While not, strictly speaking, a weekly version of Spotify Wrapped, it is pretty close.

Intuit launches agentic AI consumer platform for year-round money management
Intuit has introduced an all-in-one Agentic AI-driven consumer platform that combines Credit Karma and TurboTax into a single system to deliver year-round control of personal finances. The company says this unified platform will help users manage credit, debt, wealth building, and tax preparation in one place, powered by advanced AI and supported by a network of 13,000 human experts across the United States.
The platform is built to predict and automate key financial actions, offering what Intuit calls “done-for-you” daily management and wealth optimization. It uses Agentic AI to identify opportunities for users to improve their money situation while combining automation with personalized guidance from human experts. According to the company, this hybrid approach will provide faster access to cash, smarter tax management, and ongoing financial support tailored to individual circumstances.

Identity for AI aims to bring accountability and trust to enterprise AI systems
Ping Identity has introduced Identity for AI, a new enterprise solution aimed at securing and enabling the growing use of autonomous AI agents. The platform focuses on embedding trust, visibility, and accountability into agentic systems as businesses begin to adopt AI-driven processes across operations and commerce.
The company said the technology will help organizations manage the risks and opportunities of agent-based automation by making sure that each AI entity operates within defined, auditable boundaries.

CISO budgets increase with identity and data protection top priorities
A new study from RSAC finds most CISOs’ budgets increased between 2024 and 2025 and their top areas of investment for 2025-2026 are identity and data protection.
While 76 percent of CISOs report that their budgets for 2024-25 had increased, just 12 percent saw their budgets decrease.
