Download Google's experimental data-sipping Search Lite app

Technology companies are increasingly realizing that if they are to break into emerging markets, they're going to have to reduce the amount of data their apps use. Facebook Lite, Twitter Lite and LinkedIn Lite are just some of the less demanding apps to have been launched recently.
Google doesn’t want to miss out on the action. It is currently testing a data-light version of its search app for use in countries with slow connections. Search Lite (or Search (Test App)) is currently available to download from Google Play in Indonesia -- or from other sources if you're elsewhere in the world.
Malware attacks rising thanks to leaked exploits

Malware threats have reached dangerously high levels, according to a new report that highlights the sheer scale of threats facing businesses today.
The latest Kaspersky Lab Malware report, covering the three months of Q2 2017, claims that Kaspersky Lab's products blocked more than five million attacks involving exploits in this time period.
ADATA launches XPG SX9000 PCIe NVMe M.2 SSD for PC gamers and enthusiasts

NVMe solid state drives are rewarding computer users with exceptional speed nowadays. Compared to SATA, they are much faster, and thanks to the M.2 form factor, they are much smaller too. While 2.5-inch drives are fine for a desktop, they are too large for modern laptops -- especially as manufacturers try to push the boundaries of thinness.
If you are looking to upgrade your laptop or desktop with a fast PCIe NVMe M.2 SSD, ADATA has a new product which might pique your interest. Called "XPG SX9000," it offers tremendous performance using the M.2 2280 form factor. The "XPG" in the product name indicates this ADATA has created this drive for both gamers and enthusiasts. The company is even including a very impressive 5 year warranty.
Facebook expands Marketplace across Europe
Looking to compete with the likes of eBay and Craigslist, Facebook's Marketplace serves as a place for people to go to buy and sell locally. Following on from success in the US, UK, Australia and other countries, the social network is expanding the exchange further into Europe.
In total, Facebook's Marketplace is spreading to 17 European countries, meaning that it is now available in a total of 24 countries.
StarTech launches U.2 NVMe SSD to PCIe Drive Adapter Expansion Card

SATA is so out of style. Nowadays, all the cool kids are using much-faster NVMe PCIe-based solid state drives that utilize either U.2 or M.2 connectors; I prefer the latter, but I digress. Of course, to maximize the performance of these ultra-fast drives, you will not only need the appropriate connectors, but PCIe 3.0 too. If you don't have the correct connector, all is not lost. Thanks to PCIe adapter cards, you might able to add compatibility to your system without the need of a new motherboard.
While M.2 adapter cards are very commonplace, U.2 variants are not. Today, StarTech is back with another very useful product -- the U.2 to PCIe Drive Adapter Expansion Card. If you don't have a U.2 connector port, but do have a PCIe 3.0 x4 or higher slot, this card will allow you to connect a compatible drive at top speed. It will work with PCIe 1.0 and 2.0 too, albeit at much slower speeds. You can mount the 2.5-inch U.2 drive (15mm, 12.5mm, 9.5mm, 7mm, and 5mm height) directly on the card, meaning there are no unsightly cables.
Leaked exploits and hacking tools enable the surge of cyber attacks in 2017

Last year, the interconnectedness of cybercrime was demonstrated by a variety of supply chain hacks and other well-known cybersecurity issues that coalesced to create massive botnets powered by compromised Internet-of-Things (IoT) devices. The events from the first half of 2017 highlight another long-developing issue, which has been made worse by a variety of data dumps from actors such as WikiLeaks, TheShadowBrokers, and others: the leakage of state-sponsored and cybercriminal hacking tools and exploits.
Much like leaked personal data, once those vulnerabilities, exploits, and tools are exposed, they forever remain in the cybercriminal public domain. The May outbreak of WannaCry ransomware and the June outbreak of the data-destroying malware NotPetya both leveraged leaked NSA exploits to disrupt numerous organizations across the globe.
Opera 47 (finally) adds bookmarks export, smoother video playback

Opera Software has unveiled Opera 47.0 for Windows, Mac and Linux. It’s a fast turnaround from Opera 46, taking less than the usual six-week development cycle to go from alpha to final release.
As a result, the new release is light on major features, but does boast a number of improvements, including smoother video and exportable bookmarks. It also updates the underlying Chromium engine to version 60.
Glass Enterprise Edition is super expensive

One of the main reasons why Google Glass failed to take off was because of its crazy price tag. It was hard to get consumers to embrace a new type of gadget when it cost $1,500 and offered questionable benefits.
The new Glass Enterprise Edition may be after a different crowd, but its price has not changed much. A listing on a partner vendor reveals that business customers can expect to pay €1,550 (about $1,830) for a single device with a bundled app.
LogMeIn buys Nanorep to offer personalized user experiences

LogMeIn has revealed a major new deal which it says will help its services become smarter and more personalized than ever.
The privacy firm has announced that it will acquire the digital self-service, chatbot and virtual assistant company Nanorep to provide more personalized experiences for its customers.
Try the public preview of new sign-in experience for Azure AD and Microsoft accounts
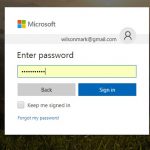
Microsoft has redesigned the sign-in process (or "experience" as the company refers to it) for both Azure AD and Microsoft accounts.
The interfaces for the sign-in screens for both types of account have been updated so they are the same, and there's now a Google-style two-page sign-in procedure. The updated design is available as a public preview and the change has come about through telemetry data collected by Microsoft.
Microsoft releases Windows 10 Fall Creators Update Build 16257, with one big unexpected change

Windows 10 Fall Creators Update isn’t too far off being ready for release, which should mean that the new builds we see are pretty unexciting, with bug fixes and minor improvements the order of the day.
But it appears Microsoft didn’t get that memo, as there’s several big changes in new Build 16257, including one that no one saw coming, and which won't be visible to most.
Putin bans VPNs and proxies in Russia as Apple explains pulling VPNs from Chinese App Store

VPNs and proxies are now illegal in Russia after Vladimir Putin signed a new law which prohibits technology that can be used to access websites that are banned in the country. The law also prevents people from using tools to stay anonymous online, and a second law requires users of messaging tools to be identifiable through their phone numbers.
As Russia hardens it implementation of government-imposed censorship, Apple has explained the sudden disappearance of around 60 VPN tools from the Chinese version of its App Store. The actions of both countries are seen as attempts to further thwart freedom of speech.
Evolving Application Performance Management (APM) to Digital Experience Monitoring (DEM)

Application Performance Management (APM) tools have traditionally provided organizations with key performance metrics, including the speed, reliability, and capacity utilization of datacenter systems. But without clear visibility into the actual experience of users, these metrics mean very little. Just because your servers measure as 100 percent available, doesn’t mean users in all geographies are having a fast, reliable experience.
That’s because there are many other performance-impacting elements standing between your datacenter and your users. If an IT organization can’t effectively monitor the true user experience -- including customers, employees, partners, and suppliers -- it is impossible to know if their applications are delivering sufficient performance. The damaging results include frustrated customers which can lead to churn, decreased revenue and market share, and diminished brand perception.
LG focuses on the customer experience with complimentary G6 second year warranty

When you buy a company's product, the experience doesn't end at the store. Well, at least it shouldn't. While some companies may wipe their hands after the sale, the truly high-quality brands will focus on the overall experience for the life of the product. Apple, for instance, does an excellent job here, making you feel like you've joined a club that cares about you. While buying Apple Care improves that experience, even without it, some consumers may end up with a warm and fuzzy feeling.
Another company focusing on the customer experience? LG. If you weren't already aware, owners of the G6 Android flagship -- an excellent smartphone -- are able to get a complimentary second year warranty at no charge. Yup, you can register for what the company calls the "LG G6 Second Year Promise." In fact, the company even guarantees an expedited turnaround time if your under-warranty G6 should need replacing. Quite frankly, this warranty -- coupled with decreasing price -- makes buying the device a no-brainer. To highlight this previously announced promise, the company has now created a new video explaining it.
Exploring the psychology of ransomware

In recent months we've seen high profile ransomware attacks target many businesses, and we've seen cyber criminals making greater efforts to target their victims.
A new study from endpoint protection company SentinelOne and De Montfort University has been looking at how social engineering tactics are used by cyber criminals to manipulate and elicit payments from victims.
Recent Headlines
Most Commented Stories
© 1998-2024 BetaNews, Inc. All Rights Reserved. Privacy Policy - Cookie Policy.