
Second quarter sees an 18 percent rise in DDoS attacks
In the second quarter of 2019, the total number of DDoS attacks grew by 18 percent, compared to the same period in 2018 according to a new report from Kaspersky.
There is, however, a drop compared to the first quarter of this year, with attacks down 44 percent. Kaspersky attributes this to seasonal variation with DDoS attack usually declining in late spring and summer.

A disturbing lack of outrage about the E3 Expo leak
Why don’t I feel bad? I know I should. I know I ought to be alarmed by the news that the organizers of the E3 Expo accidentally leaked the personal or professional contact details for some two thousand registered journalists and members of the media.
But I’m not. In fact, I’m ambivalent about the whole thing. As an early victim of some malicious "doxxing" -- by a fellow tech journalist, no less -- I’ve become a bit jaded about the matter (having satellite images of your house posted online so freaks can target your children will do that to you).

These are the Apple Card restrictions you need to know about
Apple Card is due to launch later this month and there are a few restrictions associated with Apple's predictably-named credit card.
The Apple Card Customer Agreement document drawn up by backing creditor Goldman Sachs shows that it cannot be used to buy cryptocurrencies. Additionally, the iPhone-based digital version of the credit card cannot be used on jailbroken devices.
When did computers get smarter than us?
There are few aspects of our everyday lives that don’t now rely on computers at some level. But does this reliance on technology mean that the machines are getting smarter than we are?
Server and network monitoring specialist CloudRadar has put together an infographic examining our reliance on technology.

Cloudflare terminates 8chan over links to mass shootings
Cloudflare has announced that it is terminating its services with controversial site 8chan. The move comes after the mass shootings in El Paso, Texas and Dayton, Ohio.
There have been numerous calls for 8chan to be taken offline in the past, and Cloudflare has previously considered removing its protective services from the site. What has now tipped the company's decision is the fact that the shooter at El Paso "appears to have been inspired" by 8chan, and even posted a racist manifesto on the site.

Facebook is renaming WhatsApp and Instagram
Being such globally recognized names, you would think that a rebranding of WhatsApp and Instagram would be a crazy exercise... but that's precisely what Facebook is doing.
In a move that is more than a little surprising -- and, many would argue, somewhat pointless -- the social networking giant is to rename the two products Instagram from Facebook and WhatsApp from Facebook. The renaming will make it clear that the company people love to hate is behind the chat and social networking tools.

How to opt out of Amazon listening to what you say to Alexa
There have been privacy concerns about digital assistants for just about as long as there have been digital assistants, and the recent confirmation that Google and Apple were listening to Assistant and Siri conversations has done nothing to allay fears.
The 'were' in that last sentence is important, as both companies have agreed -- at least temporarily -- to cease the practice. Not wanting to miss out on an opportunity for good PR, Amazon is getting in on the action, giving Alexa users the chance to opt out of having their conversations with its digital assistant listened to -- or "manually reviewed", as Amazon would prefer. Here's how to do just that.

Leaked: download the Microsoft Edge for Mac beta
Microsoft continues with the development of Edge, and a new leak gives Mac users a chance to see what the company is doing with the web browser for their preferred operating system.
Renowned leaker WalkingCat has provided a download link to an unreleased beta version of the Mac build of Microsoft Edge. As it's a beta that hasn't been released to official channels, there are possible stability issues, but it serves as a chance to try out the latest Chromium-base version of Edge for Mac.

Amazon Dash buttons get chucked on the scrap heap this month
The much-maligned Dash button from Amazon is being killed off for good. Having previously announced that they were being discontinued, Amazon has announced that as of the end of this month, it will no longer be possible to place orders via a physical Dash button.
This does not mean that the Dash ordering service is ceasing completely -- it will continue to exist in the form of virtual Dash button that can be accessed from a range of devices.
Gridlocked! Imagining the aftermath of an OTA cyberattack on connected vehicles
Twenty percent. A fifth. One in five. That’s how many stalled cars it would take to completely gridlock the Island of Manhattan in New York City. And according to a recent study from Georgia Tech on the impact of a large scale cyberattack against connected vehicles, that’s the more optimistic number. It could go even lower when you factor in traffic flow from side streets and the human propensity towards panic when we feel trapped or boxed in.
Basically, it would be the world’s worst traffic jam, with even emergency vehicles unable to move. And it would all start with a massive, system-wide attack against the Over the Air (OTA) software update mechanisms present in many modern, highly connected cars -- like those made by Tesla.
Best Windows 10 apps this week
Three-hundred-and-forty-six in a series. Welcome to this week's overview of the best apps, games and extensions released for Windows 10 on the Microsoft Store in the past seven days.
Microsoft released a new Windows 10 20H1 build this week that includes traces of a new cloud download feature. The feature adds an option to the PC reset troubleshooting process to download operating system files from Microsoft servers during resets. Windows 10 currently uses the Windows installation for that.

Users complain that Windows 10 is stuck in S mode
Windows 10 S mode is proving problematic for some people, with a number of users complaining that they are unable to get their computers out of the limited mode.
A number of laptops -- including the Surface Go and Surface Laptop -- come pre-configured to run in Windows 10 S mode, preventing users from changing their search engine in Edge, or from installing software from outside of the Microsoft Store. It is supposed to be possible to exit S mode, but the option has been broken for a number of days.

Privacy: Google stops transcribing Assistant recordings and Apple stops listening to Siri recordings
Following the revelations that Apple contractors are listening to recordings of things people say to Siri, and Google workers are manually transcribing Assistant recordings, both companies have said they will cease the practice -- at least temporarily.
Both Apple and Google were "listening in" on recordings with a view to improving their respective digital assistants, but privacy concerns have forced them to take action. But while Apple is suspending its "grading" program worldwide, Google is only changing the way it operates in Europe.
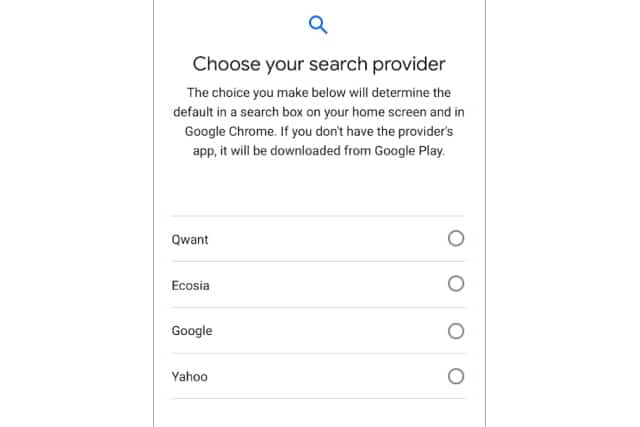
Google to let Android users in Europe choose their default search engine -- and will make money in doing so
In response to a $5 billion fine for antitrust violations in Europe, Google has announced that it will introduce a new "search engine choice" option next year. It's an idea that is similar to the Browser Choice screen Microsoft introduced following anti-competition complaints about Internet Explorer.
Google will "introduce a new way for Android users to select a search provider to power a search box on their home screen and as the default in Chrome (if installed)" in Europe starting in 2020. The search engines that appear in the list will be determined by auctions. Google rivals will have to bid to be featured in the list, meaning the company will -- controversially -- make money from giving users choice.

Ubuntu-based Linux Mint 19.2 'Tina' is here with Cinnamon, MATE, and Xfce
Happy Friday, y'all! What a great day it is. Yesterday, System76 excited the Linux community with a new 4K OLED laptop, and now today, a major Linux distribution sees release. After a very short beta period, Linux Mint 19.2 is here.
All Linux Mint releases are code-named after women, and 19.2 is no different. This version of the operating system is called "Tina," and I want to believe it is named after the lovable character on animated TV show Bob's Burgers -- although it probably isn't.



