
UK court blocks iPhone users' privacy case against Google
The UK's High Court has blocked legal action brought against Google by the group Google You Owe Us. The group represented Apple smartphone owners and claimed that Google had collected personal data from over 4 million iPhone owners.
Fronted by former Which? director Richard Lloyd, Google You Owe Us said that between August 2011 and February 2012 the search giant bypassed iPhone privacy settings and gathered user data for advertising purposes.
Google Safety Centre arrives in Europe -- or Safety Center... Google hasn't decided
Google has announced that its Safety Centre hub is rolling out across Europe. The announcement means that people in Belgium, France, Germany, Italy, the Netherlands and the UK have access to Google's selection of tools and tips for staying safe online.
The launch has been timed to coincide with European Cyber Security Month, but Google doesn't quite seem to have decided how to spell the name of its own offering.

Understanding the privacy paradox
In the modern world people often say they care about privacy, but their actions don't reflect their words. Exploring this privacy paradox is a new infographic from privacy app company Keepsafe.
It shows that 35 percent of people have concerns when making purchases on their mobile devices, but 43 percent do so anyway in the name of convenience.

Walmart teams up with MGM to create content for Netflix alternative Vudu
Walmart has partnered with movie studio Metro Goldwyn Mayer to help boost content for its video-on-demand platform Vudu.
Vudu -- which Walmart bought eight years ago -- has failed to attract a userbase anything close to that of rival Netflix, but by teaming up with MGM, there is clearly a push to change this. MGM will create original content based on its library of film and TV franchises. Walmart is also planning to introduce a new "shoppable" video ad format.

Firefox 64 will support Action Center notifications in Windows 10
Following the footsteps of Microsoft Edge and Chrome, Firefox is -- at long last -- going to offer support for the delivery of notifications through Windows 10's Action Center.
The move will please many Firefox users as this is a highly-requested feature, and it brings Mozilla's web browser in line with its rivals. While there is no release date for the finished version of Firefox 64, Action Center notification support has already made its way into the nightly builds.

Facebook Lite for iOS is now a thing
Just as there is a trend for dark themes in software at the moment, there is also something of a movement of "Lite" apps that use less data and resources. Originally intended for parts of the world where connectivity iss an issue, such apps have become popular with more and more people; because if you can use less data, why not?
We've seen Twitter Lite, Facebook Messenger Lite, and Facebook Lite -- although, until now, this last app has only been available to Android users. Now, however, Facebook Lite is expanding its reach with the launch of an iOS app.

How to disable Smart Compose predictive text suggestions in Gmail
If you're a Gmail user, you've probably noticed a new feature in the web version recently. Building on the Smart Reply feature that makes it possible to insert stock responses with a click, Google has been rolling out a predictive text component called Smart Compose.
The idea is simple, and will be familiar to users of the Gboard keyboard on Android. As you type a message, Gmail guesses what you might be trying to say and offers to complete your sentences for you. In theory this sounds helpful, but many people find it irritating and invasive -- and very possibly a privacy concern when you consider that it means your messages have to be analyzed. Here's how to disable Smart Compose.

Mageia 6.1 Linux distribution now available
While many people are familiar with popular Linux distributions like Ubuntu, Fedora, and Mint, there are far more open source operating systems available. There are probably too many, but I digress. Please know, just because a distro isn't very well known, doesn’t mean it's bad.
One such quality Linux distro that isn't super popular is Mageia. It is a fork of the once wildly popular Mandriva operating system. Today, Mageia 6.1 becomes available for download. It features LTS Linux kernel 4.14 and updated Nvidia drivers.
Voice control and dictation options are coming to Facebook Messenger
The ability to control devices and apps with your voice is becoming increasingly common, and Facebook is looking to bring this capability to its Messenger app.
Analysis of the Android version of the Facebook Messenger app shows that the company is looking to use its M assistant in messages to listen out for commands. App code shows that users will be able to make requests of M: "You can ask me to make calls, send messages, and create reminders".

Microsoft pulls the problematic Windows 10 October 2018 Update
Microsoft made its latest Windows 10 feature update available to download on Tuesday, and shortly afterwards the problems started. It didn’t play nicely with some Intel CPUs, Edge and Windows Store apps didn’t work for some users and, most damningly, the update was found to be deleting personal files.
In the face of so many problems, Microsoft had to do something, and it has. The update has been pulled.

Windows 10 October 2018 Update breaks Microsoft Edge and Windows Store apps for some users
Every time Microsoft rolls out a new Windows 10 feature update we hear of problems being encountered by early adopters, even though the update undergoes serious testing through the Windows Insider program.
The Windows 10 October 2018 Update only became officially available on Tuesday, and already it’s had to be blocked on certain Intel CPUs and, most damningly, it’s been found to be deleting user data (thankfully there’s a way to get the content back). Now it seems the new update is also causing problems with Microsoft Edge for some users.

Nintendo Switch: Fortnite -- Double Helix Bundle is here!
The Nintendo Switch is much less powerful than both the Xbox One and PlayStation 4. However, that being said, Nintendo’s offering is arguably the best of the three. Why? Well, it serves double duty as both a home and portable console. Not to mention, it has Nintendo exclusive games, featuring iconic characters like Mario and Link from Zelda. Let’s be honest, Nintendo’s own games are top shelf.
Today, Nintendo announces a special Fortnite edition of the Switch. No, the hardware is not different. The "Fortnite -- Double Helix Bundle," as it is called, simply features some exclusive content and bonus in-game currency. For fans of the wildly popular Fortnite game, this is sure to be quite enticing.
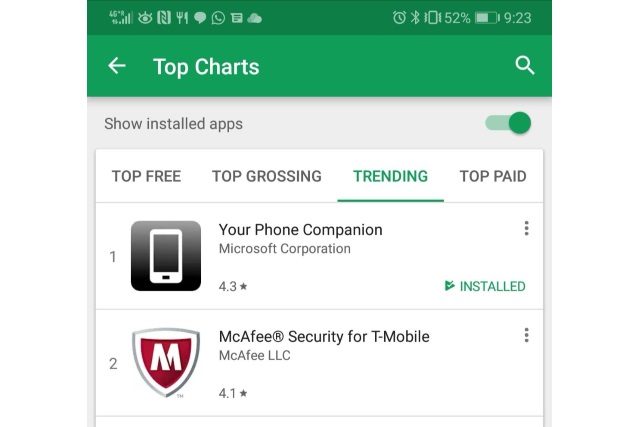
People love Microsoft's Your Phone so much, it's the top trending Android app in the Google Play Store
Having abandoned its own mobile operating system, Microsoft is increasingly embracing Android and iOS and improving interoperability with Windows. A recent example of this is the Your Phone Companion app which makes it possible to send texts from your computer and easily access photos stored on your Android phone.
The ability to access and use a phone via Windows 10 has gone down very well -- as the interest in our story about the app showed. So well, in fact, that the Your Phone app is the number one trending app in the Google Play Store.

How to voice-control your Android phone using the Voice Access app
Digital assistants are becoming increasingly popular as people become used to the idea of controlling electronic devices by speaking to them. With Android, Google has supported limited voice control for a while with "OK, Google", but with the release of the Voice Access app you can now do much, much more.
The problem with uttering "OK, Google" at your phone is that there are fairly severe limitations on what you can do -- there are only a small number of supported actions. But with Voice Access you can use your voice to dictate and edit text, and interact with anything that appear on the screen. Here's how to get started.

Apple's proprietary software is blocking third parties from repairing Macs
Apple is using proprietary software to block third parties from making repairs on new iMac Pro and 2018 MacBook Pro computers.
A document sent to Apple's Authorized Service Providers -- seen by MacRumors and Motherboard -- shows that the T2 security chip that's built into modern Macs is being used to prevent authorized repairs from being carried out. The security feature requires Macs to pass Apple diagnostics in order for specific repairs to be performed.
