
Lenovo unveils ThinkBook
Lenovo is very well known for manufacturing high quality business laptops. Its ThinkPad line, for instance, which it inherited from IBM, is considered by many to be the best. Of course, there are others who prefer Dell, HP, or another maker.
Today, Lenovo launches a new line of Windows 10 laptops aimed at small businesses in particular. Called "ThinkBook," there are two models from which to choose -- the 13s and the 14s -- both of which have a screen size that match the model name. There is just one resolution for both -- 1080p. Each model will have an m.2 solid state drive by default -- either SATA or PCIe. You can get up to 512GB of storage.

US Supreme Court rules antitrust case can proceed against Apple's 'monopolistic' App Store practices
The US Supreme Court has said that consumers can sue Apple for allegedly violating antitrust laws with its App Store.
A group of iPhone owners were seeking to bring a class action lawsuit against the company, and now Justice Brett Kavanaugh has said they can do so. The group says that in charging a 30 percent commission, Apple was making users overpay for apps, and that the requirement for apps to be sold through the App Store was unfair.

Website attacks turn to stealth to boost their success
The story of website attacks in 2018 was one of high profile cybercrime, targeted at cryptocurrency, business, elections and more.
A new report from website security specialist SiteLock reveals that attackers are now taking a stealthier approach.

TP-Link launches very affordable Deco W2400 Dual Band Mesh Wi-Fi System
If you have a large home, it can be difficult to blanket it entirely with Wi-Fi. Sadly, many folks experience dead spots, meaning some locations in the house either have no Wi-Fi or an exremely low signal. Speaking frankly, this situation sucks. Sure, you can potentially remedy it with a range extender, and that can be a great solution, but it isn't as elegant as mesh.
Unfortunately, a mesh Wi-Fi system with multiple access points can be a pricey affair. While they have been coming down in price, these mesh systems are still largely too much money for many consumers. Today, TP-Link brings mesh Wi-Fi to the masses with an insanely low price. Called "Deco W2400," this Dual Band AC1200 system costs less than $100!

This little piece of tech can turn your old alarm into a home automation system
When people decide to install home automation systems and also have security alarms they installed several years ago, it's highly likely the new tech and old gadgets won't be compatible.
Similarly, if they have a security system that doesn't work with a smartphone app, they typically have to invest in new hardware and deal with lengthy installations and high bills.

BTW I use Arch Linux... on Windows 10
Ahh, Arch Linux; the distribution with the most pretentious user base. If you aren't familiar with Arch, please know it is a very good operating system that is unnecessarily difficult to set up. As a result, the ones who are successful, and end up using the distro, are often quite full of themselves. Many Arch users seem to look down on those using a different distro, such as Ubuntu or Linux Mint. This is what has lead to the infamous "BTW I use Arch" meme. No, not all Arch users are insufferable, but many are. True story.
And now, thanks to Microsoft's Windows Subsystem for Linux, you can (sort of) become a pretentious Arch user too -- all without leaving the comfort of Windows 10. That’s right, folks, you can now install Arch from the Microsoft Store. These are strange times we are living in, eh?

GitHub Package Registry launches in beta
GitHub has launched the GitHub Package Registry, its new package management service.
Starting out as a limited beta, teh GitHub Package Registry gives developers, coders and organizations an easy way to publish public or private packages next to source code. For now, there is support for the likes of JavaScript (npm), Java (Maven), Ruby (RubyGems), .NET (NuGet), and Docker images, with the promise of more to come.

Google says all new Chromebooks will be Linux-ready
One of the biggest announcements from this year's Google I/O related to the Pixel 3a and Pixel 3a XL, but this was far from being all there was to get excited about. Microsoft may be increasingly embracing Linux in Windows 10, and Google is doing the same with Linux on Chromebooks.
Support for Linux apps on Chromebook is nothing new, but Google has now announced that all Chromebooks that launch from this point forward will be fully functional Linux laptops, regardless of whether they are ARM or Intel devices.
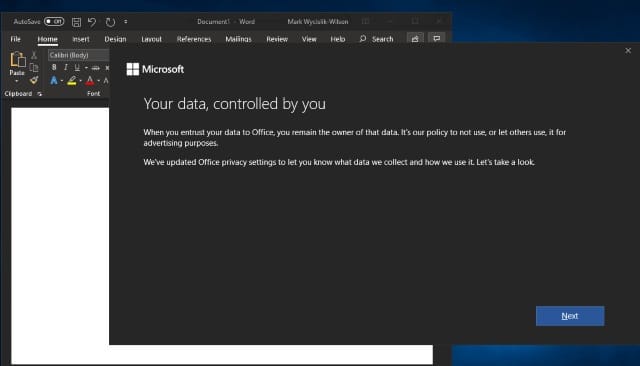
Privacy: Microsoft wants to (sneakily) collect more data from users via Office
Launch Word, Excel, PowerPoint or some other Microsoft Office app on your computer, and you'll be greeted by a dialog entitled "Your data, controlled by you". You'll then be invited to review your privacy settings to determine how much telemetry data Microsoft is able to collect through Office.
Earlier this month, Microsoft made reference to privacy and user feedback in its office suite, saying that "Office is built on trust". Now, the company is using a popup dialog to give users a chance to control the data they share; or, looked more cynically, to trick them into agreeing to share more data.

Urban Armor Gear (UAG) 'Scout Series' is a rugged case for Apple iPad Pro and Smart Keyboard Folio
Apple's iPad Pro is the best tablet on the market, and believe it or not, it can be a fairly useful "laptop" when paired with the Smart Keyboard Folio. Microsoft is simply wrong in its claims about Apple's tablet. You can even expand iPad Pro functionality with USB-C dongles. Without mouse or trackpad support, however, iOS will never be a proper desktop operating system, but I am hopeful that will be added eventually.
If you are someone who owns both the Apple iPad Pro and Smart Keyboard Folio, Urban Armor Gear has a really cool new rugged case you should check out. Called "Scout Series," it protects the tablet without the need to remove the keyboard. In fact, this case requires the keyboard be attached. It even has a useful Apple Pencil holder that allows charging.

Microsoft releases Windows 10 20H1 Build 18895 -- fixes Your Phone app
Development is proceeding well on Windows 10 20H1, even though that feature update isn’t set to be released until the first half of next year.
Microsoft rolled out Build 18894 two days ago, with File Explorer and Accessibility improvements, and today it releases build 18895 with an important fix -- although this flight isn’t available to everyone.

Rock Jaw T5 Ultra Connect wireless earphones [Review]
Previously when we've reviewed earphones from Rock Jaw we've found them to be a good compromise between affordability and performance.
The T5 Ultra Connect is the first wireless product we've seen from the firm, so we were keen to find out how they measure up.
Best Windows 10 apps this week
Three-hundred-and-thirty-four in a series. Welcome to this week's overview of the best apps, games and extensions released for Windows 10 on the Microsoft Store in the past seven days.
Will Microsoft retire the Store in the near future? Wayne asked that question recently. I think the Store is here to stay, but Microsoft changed the focus from all-in on UWP to a new strategy that tries to get Win32 developers on-board as well.

Is latency the cloud's Achilles heel? [Q&A]
The cloud is arguably the most transformative enterprise technology in the past two decades. Yet, as powerful as it is, it faces a huge latency problem -- and the big public cloud providers know it.
Their data centers can't be everywhere and close to every end-user, so the big distances created result in unavoidable latency.

Photo storage app Ever is using millions of users' photos to build a facial recognition system
An investigation by NBC News has found that photo memories app Ever has been using billions of images uploaded by people to develop a facial recognition system without making it obvious to users.
Ever is a photo storage app that offers "free, unlimited private backup of all your life's memories". It's not until you delve into the company's privacy policy that you learn that in using the service, users are agreeing not only to have their photos used in facial recognition training, but also for Ever to sell the resulting technology to private companies, law enforcement agencies and the military.


