
ADATA unveils XPG SPECTRIX S40G RGB NVMe PCIe Gen3x4 M.2 SSD for gamers
RGB lighting makes everything better. Is it tacky? Yeah, I suppose, but more importantly, it is fun. Life is short, y'all -- just sit back and enjoy the light show!
Solid state drives with RGB lighting are hardly new, but they are still fairly rare. ADATA's latest SSD, called "XPG SPECTRIX S40G," is extremely pretty thanks to its RGB heatsink. And no, this drive isn't fashion over function -- it is an NVMe PCIe Gen3x4 M.2 SSD with very impressive read and write speeds.

Undetectable HiddenWasp backdoor malware hits Linux users, allowing for full control of infected systems
Using code from the famous Mirai worm and the Azazel rootkit, HiddenWasp is a newly discovered malware strain targeting Linux systems.
HiddenWasp is slightly unusual in having Linux in its sights, and the targeted remote control tool is able to avoid detection by all major antivirus software. The malware is described as "sophisticated" as it comprises a deployment script, a trojan and a rootkit. This an advanced backdoor attack tool that allows for complete remote control of a system.

Still running Fedora 28 Linux distro? Well, you shouldn't be...
Fedora is my personal favorite desktop operating system. I love it because it is fast, stable, and focuses on open source ideology. Not to mention, it uses the best desktop environment, GNOME, by default. Overall it is a great experience that I recommend to all.
While I update to the newest version of Fedora as soon as it is available, obviously, some people do not. You know what? That's OK. Even if you are a version behind, as long as it is still supported, you are safe and sound. Once the version of Fedora you are running is listed as "End of Life," you should definitely upgrade as soon as possible, as it will no longer get bug, feature, or security fixes. Well, folks, Fedora 28 is now EOL, meaning you need to plan an upgrade soon, as you could be exposed to new vulnerabilities.

Staff break IT rules in order to do their jobs with management the worst offenders
A new survey of more than 3,000 people around the world finds 46 percent of employees access personal documents on their work device without the IT department's permission.
The study from Snow Software also shows 41 percent of global employees are going behind IT's back to get professional software and applications.
Best Windows 10 apps this week
Three-hundred-and-thirty-seven in a series. Welcome to this week's overview of the best apps, games and extensions released for Windows 10 on the Microsoft Store in the past seven days.
The May 2019 Update for Windows 10 is available for select configurations but it is likely that it won't change the operating system's fragmentation. Latest Adguard stats suggest that most Windows 10 devices are still on the April 2018 version of the operating system.

Why digital transformation must be optimized for speed and success [Q&A]
Companies worldwide across all industries are enacting digital transformation (DX) initiatives -- and for good reason. If completed successfully, modern technology implementation drives competitive advantage and makes business operations much more real-time.
However, the journey to the DX finish line is unfortunately sometimes much more of sprint than a marathon, as speed is the currency for organizations to complete the process.

Leaked: take a look at Cloudflare's free VPN, Warp
Cloudflare's 1.1.1.1 DNS switching tool has proved very popular with iOS and Android users looking to take control of their internet connections, and there was much excitement when the company announced that it would be releasing a free VPN tool called Warp.
At the moment, there is a lengthy waiting list for the free VPN (I'm number 278100 on the list, for instance) but we've been given a sneak peak at what to expect. Leaked screenshots show off the free VPN, and a video gives you an idea of the sort of performance you can expect.

Google Maps 'Popular Dishes' feature gonna get gourmands, gastronomes, and gourmets giddy
Eating is one of life's greatest pleasures. Whether it's a $1 hotdog or a $200 steak, enjoyment from food can be had with any budget. Hell, sometimes the food at a less expensive restaurant can be better than the fancy ones that charge a lot. Ultimately, it comes down to doing your homework on an eatery before going there -- reading online reviews, perusing the menu, and finding out which of its dishes are best.
Today, Google announces an update to its wildly popular Maps service that should prove to be very helpful. Called "Popular Dishes," the search giant is enabling the ability to discover the best food to order at many restaurants. In other words, it should reduce the possibility of you making a poor decision and spending your hard earned money on an unimpressive meal that you don't truly enjoy.

Urban Armor Gear (UAG) unveils rugged Plasma Series case for OnePlus 7 Pro
OnePlus smartphones are very well received by those wanting a pure Android experience. They are also popular with budget shoppers, as they have historically been very affordable. Over time, however, OnePlus has been increasing prices, reducing the perceived value of these devices. With the OnePlus 7 Pro, for instance, the starting price is $700 -- a significant amount of money. With that said, it stills costs less than some flagship phones from other manufacturers, such as Samsung and Apple.
If you do decide to drop a big chunk of change on the OnePlus 7 Pro, I hope you would protect it with a case. Today, famed case manufacturer Urban Armor Gear releases such a product -- the Plasma Series case for OnePlus 7 Pro. It is a very rugged case with a pretty reasonable price tag. And yes, the case is designed to accommodate the device's unique pop-up front-facing camera.

New tool allows files to be encrypted and shared wherever they’re stored
One of the best ways of preventing sensitive files from falling into the wrong hands is to encrypt them, but the process of encrypting and decrypting can be a chore, especially if you want to share the information.
VPN service NordVPN is set to launch its own NordLocker security tool, designed to safeguard files whether they are stored locally or in the public cloud, and make them easy to share.
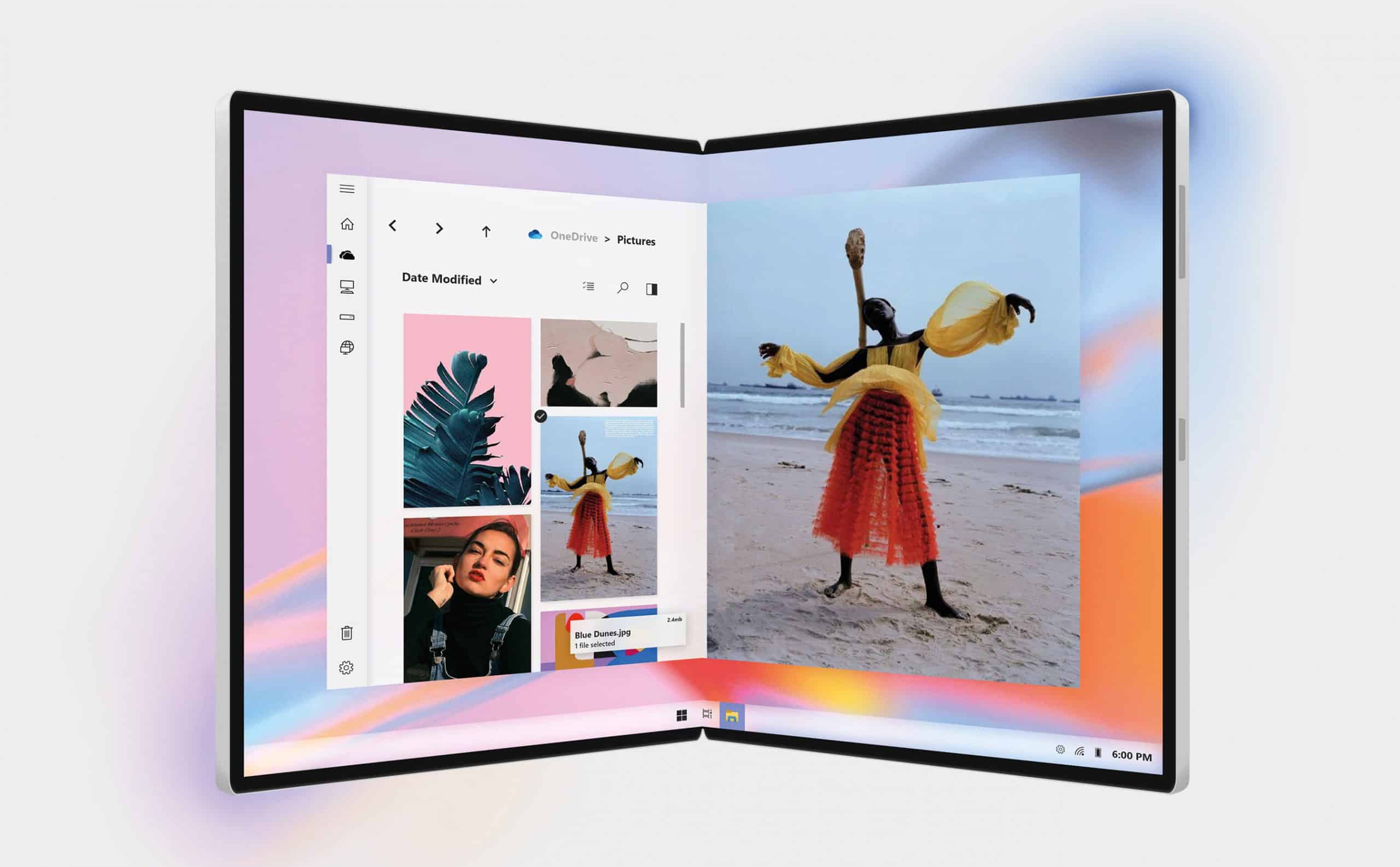
'Files' for Microsoft's Windows Lite OS looks amazing running on a foldable Surface
Back in 2015, Microsoft said that Windows 10 would be the last version of Windows. The software giant views its newest operating system as a service that’s continually updated. Although problems with both the October 2018 Update and May 2019 Update mean that’s not really true at the moment. Most Windows 10 users are still on the April 2018 Update.
Device manufacturers are continuing to innovate, and Chromebooks are showing a very different future from the one Windows 10 is offering us. This is where the modern "Windows Lite" comes in.

Twitter looks into whether white nationalists and supremacists should be banned
In a world that appears to be lurching ever further to the right, it is perhaps little wonder that white nationalists, white supremacists and other extremists are becoming more prevalent online. Social media sites have a balancing act to perform -- not wanting to be seen to be advocating censorship, but also removing troublesome elements from their networks.
And this is the problem that Twitter faces. The platform has long been home to a glut of racist content and users -- as well as other unsavoury material -- and now the site is conducting research to determine how best to tackle this. Specifically, it is looking at whether white nationalists and supremacists should simply be banned, or whether their posts should be left available for others to debate.

The iPhone-maker doth protest too much? Apple launches new site to wax lyrical about the App Store in the face of criticism
Apple has become more familiar with controversy than it might be entirely comfortable with in recent times. Once a near-untouchable company that could, in many people's eyes, do no wrong, there have been numerous scandals over the last few years -- legal battles, problematic hardware, canceled products, and accusations of anticompetitive behavior.
Faced with an antitrust legal battle after complaints of "monopolistic" practices in the App Store, Apple has launched a new site that appears to be a very public defense of what it stands accused of. The new "principles and practices" pages find Apple going out of its way, falling over itself to expose just how anticompetitive the App Store isn't. This is a company on the defensive.

Microsoft releases Windows 10 20H1 Build 18908 with more features for Your Phone
Microsoft has been teasing us with talk of a new "modern" operating system, but that doesn’t mean it’s forgotten about Windows 10.
Today it releases a new Fast ring build on the 20H1 branch -- the feature update set to roll out to users a year from now -- and adds a wealth of new features to the Your Phone app.

Amazon Echo Show 5 is a privacy-focused Alexa device
Earlier this month, Google announced the Nest Hub Max -- voice assistant hardware with a camera and touch screen -- and I was instantly intrigued. At the same time, I was also very scared of it. After all, Google makes its money through tracking users' activity and by displaying advertising -- did I really want that company having a camera in my house? No, of course not. Despite the claims of hardware switches to disable the camera, I quickly made up my mind to not buy it when it goes on sale.
Amazon has a similar device called Echo Show, and today it announces an additional model. Called "Echo Show 5," it has a smaller screen (5.5 inch) and even smaller price tag. It is an adorably small Alexa device with an HD camera. Unlike the round Echo Spot, Echo Show 5 has a more useful rectangular screen. As someone who owns many Echo devices, and trusts Amazon a bit more than Google, I think I might invite Echo Show 5 into my house. I wouldn't want the camera watching my family 24/7, so thankfully I can take control of my privacy by sliding the included shutter over the lens -- an old-school (yet effective) means of blocking a camera.



