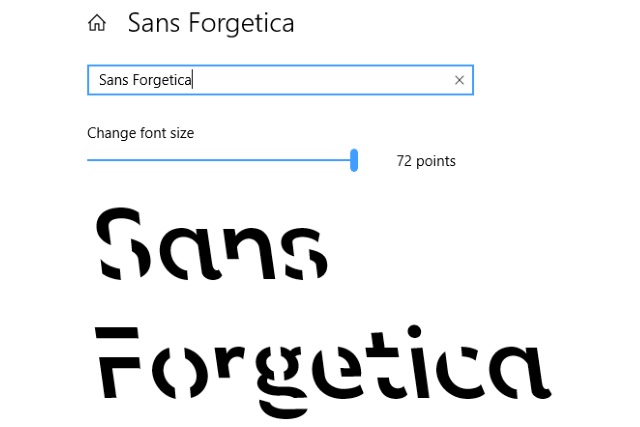
Sans Forgetica: the font that could help you remember
Researchers from Australia's RMIT University have created a font which they say could help you to retain more data.
Sans Forgetica is the result of work involving typographic design specialists and psychologists, and it has been designed specifically to make it easier to remember written information. The font has purposefully been made slightly difficult to read, using a reverse slant and gaps in letters to exploit the "desirable difficulty" as a memory aid.

The new Calculator app in the latest Windows 10 update is HUGE, but you can fix that
Five years ago, I wrote a story about how Windows 8.1's Calculator app summed up what was wrong with Microsoft's new OS. Windows 8.x was designed as a one-size-fits-all operating system, and apps were designed with little thought given to the different screen sizes they'd be viewed on.
The problem was, on a desktop PC with a large screen, the Windows Calculator was massive. Or, as I put it at the time, "bloody huge -- filling my screen with buttons the size of business cards." Fast forward to 2018, and Microsoft is at it again, this time in the Windows 10 October 2018 Update.

New Kodi 18 'Leia' Beta 3 arrives -- download it now!
Development on the next big version of Kodi, codenamed 'Leia', is progressing nicely. It’s expected to be released by the end of this year.
For those who can’t wait, you can install pre-release versions, and the newest of these -- Beta 3 -- is available to download and install today.
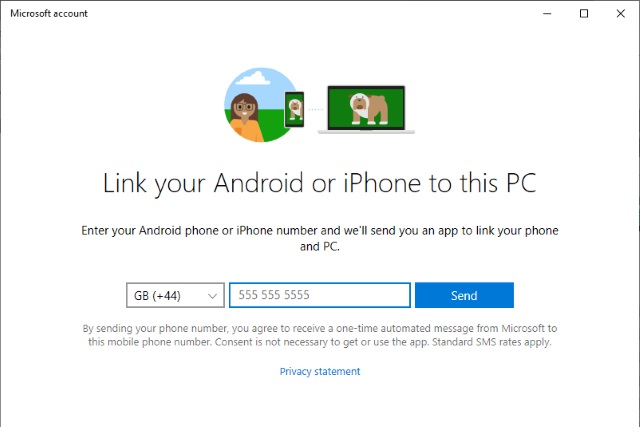
How to access your Android phone from Windows 10 with Microsoft's Your Phone app
Without a mobile operating system of its own, Microsoft is doing more for iOS and Android users than ever before. One example of this is the Your Phone app which makes it possible to view your Android phone's photos on your computer, as well as viewing and sending text messages from the comfort of Windows 10. Microsoft has also promised to enable an exciting-sounding app-mirroring feature.
As long as you have upgraded to the Windows 10 October 2018 Update, you'll have the Your Phone app installed on your computer already. Here we take a look at this handy tool and show you how to get started with it.

DevOps and digital transformation are creating more insecure apps
For enterprises looking to build new applications as the cornerstone of their digital transformation initiatives, techniques like DevOps are undeniably attractive.
But while they speed up development they also mean that nearly 70 percent of every application is made up of reusable components like third-party libraries, open source software. This means that applications can easily inherit the vulnerabilities in those components.
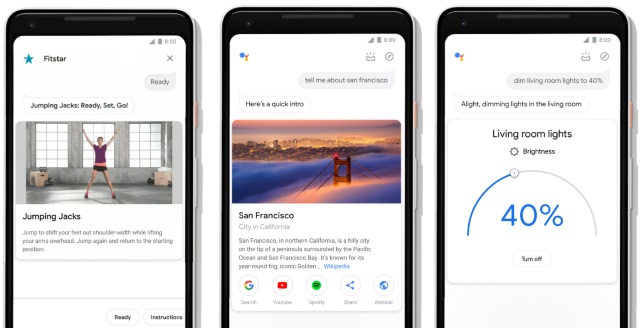
Google Assistant gets a revamp and new features
Having introduced a new Voice Access app to allow for full voice control of Android phones, Google has also redesigned Google Assistant on both iOS and Android.
The revamp makes the app a more visual experience, with Google acknowledging that while the Assistant is a voice-activated tool, touch is also a key component. With the redesign, Google hopes that bigger visuals and new controls will make it easier and faster to get things done with a combination of voice and touch.

Amazon unveils Fire TV Stick 4K with Alexa Voice Remote, Dolby Vision, and HDR10+
Traditional cable TV providers should be very worried. These days, it is easier than ever to cut the cord. Thanks to streaming media, a small box, dongle, or stick can deliver high-quality movies, TV, and music over the internet. Using myself as an example, I leverage YouTube TV, Apple Music, Amazon Prime Video, and Netflix for all of media needs. The local TV provider no longer gets my money -- except as my ISP, that is.
Believe it or not, 4K content is becoming more and more common, and lately, 4K streaming devices have become very affordable. Last month, for instance, Roku unveiled new 4K devices starting at just $39.99 -- $10 more if you want the voice remote. Not wanting to be left out, today, Amazon unveils the Fire TV Stick 4K and it looks like an insane value. Not only does it come with an all-new Alexa Voice Remote, but it features Dolby Vision, Dolby Atmos, and HDR10+ too -- all at a rock-bottom price.

Microsoft releases Windows 10 19H1 Build 18252 to the Skip Ahead and Fast rings
Yesterday, Microsoft made the Windows 10 October 2018 Update available to anyone who wants it, meaning there’s currently only one development build on the go.
Because of that, new builds on the 19H1 branch are now being pushed out to insiders on both the Skip Ahead and Fast rings. If you’ve yet to opt out of the Insider program or switch to the Slow ring, and your PC downloads and installs Build 18252, released today, you will need to roll it back and take appropriate action.

Wi-Fi gets brilliant new naming scheme
For tech savvy consumers, buying a wireless router or adapter is a fairly simple affair. For the majority of shoppers, however, it can be very confusing. Let’s be honest, it is impossible to know that 802.11ac is better than, say, 802.11n without first researching it. I mean, hell, how is the average consumer supposed to know what the letter designation following the 802.11 really means? It is simply nerdy jargon.
Apparently the Wi-Fi Alliance wants to make it easier to decipher. Starting with the 802.11ax, numbers will be used instead. For instance, ax will be Wi-Fi 6, while n and ac will retroactively be called Wi-Fi 4 and Wi-Fi 5 respectively.

Insiders cause more than half of data breaches
Most companies consider hacker attacks to be the most dangerous threat, but according to a new report, insiders cause the majority of security incidents by either malicious or accidental actions.
The study from threat detection specialist Netwrix looks at the experiences and plans over 1500 organizations have in addressing IT risks. The insider threat is underlined by the fact that 44 percent of respondents either don't know or are unsure what their employees are doing with sensitive data.

Avira Internet Security 2019 boasts triple-faceted protection with new password manager
Security developer Avira has released Avira Internet Security Suite 2019, a brand new version of its flagship security tool for Windows.
Version 2019 brings together all the vendor’s tools under one roof, and adds one new component to the mix: Password Manager. This comes with a Security Status feature that will alert users to global account, website and password breaches.

Data theft malware targets Fortnite players
It's no surprise that the release of a new season of Fortnite has led to a rise in scammers keen to exploit gamers who are eager to sample the new software.
Among a rash of supposed free passes and free Android versions of the game that hide surveys and other nuisances, researchers at Malwarebytes have uncovered a malicious program seeking to steal data and Bitcoins.
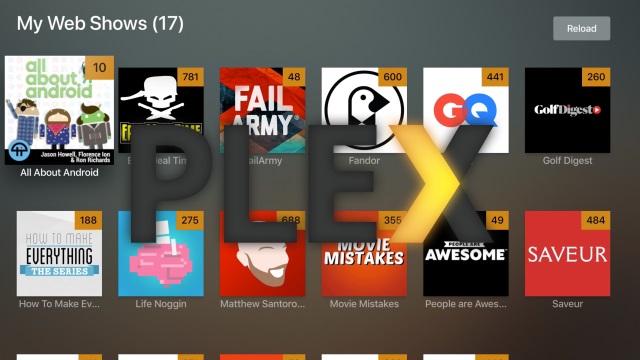
Plex launches beta version of Plex Web Shows offering on-demand streaming shows for free
Continuing to increase its appeal to cord-cutters, Plex has announced a new on-demand streaming feature. Plex Web Shows is launching in beta and includes curated content from independent creators like Epic Meal Time, ASAPscience, Household Hacker, People are Awesome, and The Pet Collective, as well as brands including GQ, Saveur, Epicurious, and Pitchfork.
Plex Web Shows works across a range of devices -- web, iOS, Android, Apple TV, Windows, macOS and more -- and does not require either a Plex server or a paid Plex subscription. Like Plex News and Plex Podcasts, content is not only curated, but includes smart, custom recommendations based on preferences and watching history.

67 percent of organizations believe hackers can penetrate their network
Around two-thirds of executives and IT professionals responding to a new survey believe that hackers would be able to penetrate their networks.
The study from security and application delivery company Radware focused on global companies and reveals that at least 89 percent of respondents have experienced attacks against web applications or web servers of the past year.

Google launches new .page TLD
Google has announced the availability of a new TLD (top-level domain) from its own Google Registry. Joining the likes of .com and .org comes .page which is described as "a new opportunity for anyone to build an online presence".
With security in mind, Google says that all .page websites require an SSL certificate. For businesses and individuals, the race is now on to grab the domain they want before it is snapped up by someone else.


