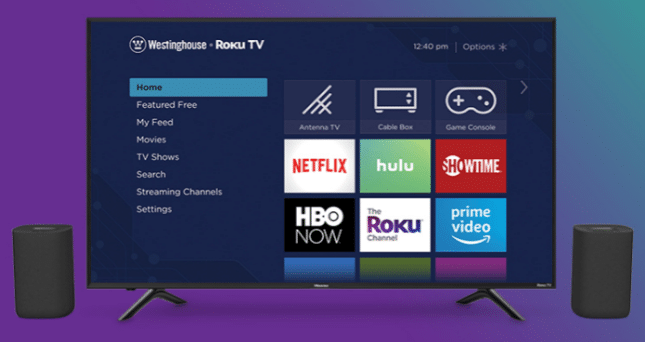
Enter to win a 55-inch 4K smart television and Roku TV Wireless Speakers
Need a TV? You should definitely buy a 4K model. Even if you don't have any UHD content now, it makes sense to "future-proof" at this point as pricing has gotten quite low.
If you are averse to spending money, I have good news -- Roku is giving away a 55-inch 4K Westinghouse TV. This smart TV has an integrated Roku, making it easy to stream content. The model of TV is "WR55UE4019," which I have been unable to find for sale online. That's not all, however -- the company is also including its Roku TV Wireless Speakers for a superior audio experience.

Mozilla bans Firefox add-ons with obfuscated code
As Mozilla continues to try to make it safer than ever to use Firefox, the organization has updated its Add-on Policy so that any updates that include obfuscated code are explicitly banned.
Mozilla has also set out in plain terms its blocking process for add-ons and extensions. While there is nothing surprising here, the clarification should mean that there are fewer causes for disputes when an add-on is blocklisted.

Data breaches spark increased interest in password managers
People have been predicting the death of the password for some time, but it's still the case that most online accounts rely on them, even if supplemented by another feature like 2FA.
A new report from Avira to coincide with World Password Day shows that so far in 2019, there have been at least four major data breaches, each impacting more than 200 million records.

Social media phishing attacks up more than 70 percent
Social media phishing, primarily on Facebook and Instagram, has seen a 74.7 percent increase in the first quarter of 2019.
A new report on the current phishing landscape from predictive email defense company Vade Secure also shows that Microsoft has retained its spot as the most impersonated brand for four straight quarters, due to the potentially lucrative returns to be gained from Office 365 credentials.

Lack of security and operations basics leave businesses unprepared for breaches
A new report from endpoint management specialist 1E reveals 77 percent of IT decision makers polled believe that they are not well prepared to react to a serious data breach and 60 percent have experienced a security breach in the past two years.
The study conducted by Vanson Bourne polled 300 decision makers from from IT operations and 300 from IT security, and finds 80 percent say digital transformation increases cyber risk.

US companies waste over two months a year resetting passwords
To mark today's World Password Day, access and identity management company OneLogin has released a report that shows IT professionals at US companies waste 2.5 months a year resetting internal passwords.
It also finds that almost half of US businesses (44 percent) take up to a month or more to deprovision ex-employees, while 28 percent take a full working week.

Putin signs law to create 'sovereign internet' for Russia
President Putin has signed into law a bill that will give Russia a "sovereign internet" -- one which could be disconnected from the global web if the Kremlin decided to do so. It is being sold as a way to "ensure the safe and sustainable functioning" of Russia's internet should the country's enemies try to block access.
But there are fears that the law -- which will require ISPs to route traffic through government-controlled servers -- amounts to the creation of a Russian version of the Great Firewall of China and will lead to severe online censorship.

Patriot Memory launches surprisingly affordable Signature Premium DDR4 RAM
Patriot is a company that makes many flash memory products, such as USB flash drives, solid state drives, and storage cards to name a few. System builders are probably most familiar with its RAM products, however. Along with companies like Corsair, Kingston, and G.SKILL, Patriot's sticks of RAM are very much respected. This includes Viper, which is Patriot's gaming brand.
Today, Patriot launches a new line of DDR4 RAM. Called "Signature Premium," you'd expect the memory to be expensive, but actually, it is surprisingly affordable. Capacities range from 4GB to 32GB, while there are two speeds from which to choose -- 2400Mhz and 2666MHz. And yes, they feature heat spreaders -- great for cooling and looking attractive too.

Microsoft releases Windows 10 20H1 Build 18890 to the Fast ring
Windows 10 19H1 -- the May 2019 Update -- is currently undergoing additional testing in the Release Preview ring to try and solve a number of upgrade blocks, including one which prevents the update from installing if you have a USB drive or SD card plugged in.
Microsoft is still working on future releases though, and today pushes out Build 18890 to Insiders on the Fast ring (and those who had previously opted to Skip Ahead).

Forget Avengers: Endgame or Game of Thrones -- watch 'Clippy: The Unauthorized Biography' instead
Steven Sinofsky was a senior executive at Microsoft who is perhaps best known for presiding over the creation of Windows 8 and RT. However, he also had a key role in the development of Microsoft Office back in the 1990s. This was a time when users feared to attempt to write a letter in Word because just starting it could well summon up Clippy -- the Candyman of productivity software -- who would attempt to help, but was rarely of any real use.
Clippy might have been retired for 15 years now, but to mark the Office assistant’s 25th anniversary, Sinofsky has made an Unauthorized Biography of the divisive animated paperclip which you can watch in full here.
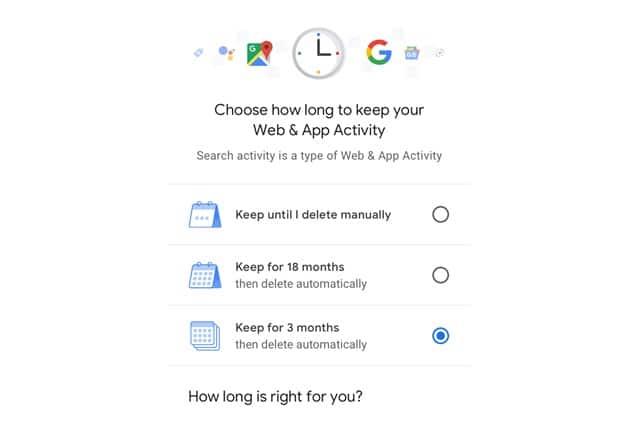
Google to roll out auto-delete controls for location history and activity data
Google has announced that it is giving users greater control over how long the company holds on to location history and activity data.
A new time-limiting feature makes it possible to have information such as account activity and location data automatically deleted after a period of time. The privacy-focused move comes after feedback to Google which found users wanted the company to provide simpler ways to manage or delete the private data it holds.

TechSmith releases Camtasia 2019 with automatic audio leveling
We’ve given up on people reading through instructions supplied with their order. You can write important points in bold and people still ignore what’s supplied. Rather than replying to everyone individually, we’ve found it easier simply record a live demonstration of how to solve a particular issue and send them a video of the results.
You need a quality screen recording tool to produce a video which is professional enough to reflect your business. We recently wrote about Captura 8, which is an excellent freeware screen recording tool, but you’ll want to step up a level or two if you’re recording for paying customers.

Windows 7 users not rushing to upgrade to Windows 10
It took a very long time for Windows 10 to finally overtake Windows 7, but the new OS finally achieved that feat four months ago, according to figures from NetMarketShare.
In March, Windows 10 made large share gains, while Windows 7 declined significantly, and that is a picture one would have expected to see continue in April, especially now that Microsoft has started alerting Windows 7 users to the impending end of life of their chosen OS. However, that has proven not to be the case. Despite the warning, it seems Windows 7 users aren’t in a rush to upgrade anytime soon.

AIOps tools successful in delivering value for 87 percent of organizations
Artificial Intelligence Operations (AIOps) tools are delivering value through proactive IT operations and improved hybrid infrastructure resilience in 87 percent of implementations, according to a new report.
The study from OpsRamp reveals the three biggest benefits of AIOps tools as productivity gains from the elimination of low-value, repetitive tasks across the incident lifecycle (85 percent), rapid issue remediation with faster root cause analysis (80 percent), and better infrastructure performance through noise reduction (77 percent).

These are the current upgrade blocks for the Windows 10 May 2019 Update
After the disaster that was the buggy October 2018 Update, which most Windows 10 users have avoided like the plague, Microsoft has taken the wise step of introducing additional testing.
The next big feature update is expected to roll out to all by the end of May, but for the moment it’s undergoing extended analysis in the Release Preview ring.
